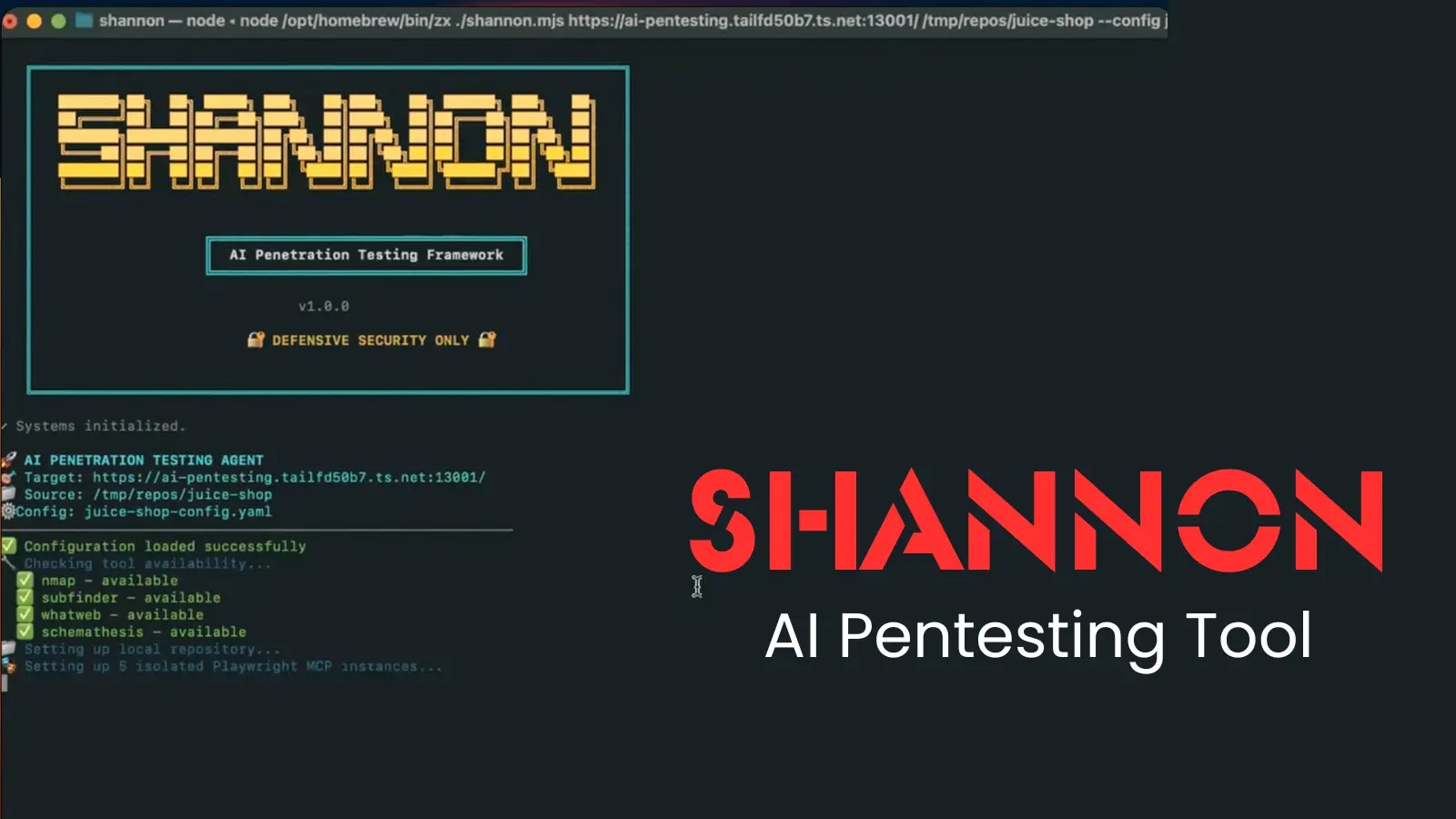
Shannon is a totally autonomous AI pentesting device for internet purposes that identifies assault vectors by way of code evaluation and validates them with stay browser exploits.
Not like conventional static evaluation instruments that merely flag potential points, Shannon operates as a totally autonomous penetration tester that identifies assault vectors and actively executes real-world exploits to validate them.
The device outperforms human pentesters and proprietary techniques on the XBOW benchmark, marking a shift towards steady safety testing.
Shannon emulates human pink group ways throughout reconnaissance, vulnerability evaluation, exploitation, and reporting phases.
It ingests supply code to map knowledge flows, then deploys parallel brokers for OWASP-critical flaws like injection, XSS, SSRF, and damaged authentication, utilizing instruments comparable to Nmap and browser automation.
Solely confirmed exploits with reproducible proofs-of-concept seem in pentester-grade studies, minimizing false positives.
Shannon – AI Pentesting Device PoC
Shannon – AI Pentesting Device
Shannon demonstrated superior efficiency on weak benchmarks, delivering actionable insights past static scans.
ApplicationVulnerabilities IdentifiedKey Exploits ConfirmedOWASP Juice Shop20+ criticalAuth bypass, DB exfiltration, IDOR, SSRFc{api}tal API15 important/highInjection chaining, legacy API bypass, mass projectOWASP crAPI15+ important/highJWT assaults, SQLi DB compromise, SSRFXBOW Benchmark96.15% success rateBeats human (85%, 40 hours) and XBOW prop system (85%)
These outcomes spotlight Shannon’s skill to autonomously obtain full app compromise.
Powered by Anthropic’s Claude Agent SDK, Shannon runs white-box checks on monorepos or consolidated setups by way of Docker, supporting 2FA logins and CI/CD integration.
The Lite version (AGPL-3.0) fits researchers, whereas Professional provides LLM knowledge circulate evaluation for enterprises. Typical runs take 1-1.5 hours at ~$50 price, producing deliverables like government summaries and PoCs.
As dev groups speed up with AI coders like Claude, annual pentests depart gaps; Shannon allows every day testing on non-production environments.
Creators emphasize moral use with authorization required, warning in opposition to manufacturing runs on account of mutative exploits. Obtainable on GitHub, it invitations neighborhood contributions towards broader protection.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.