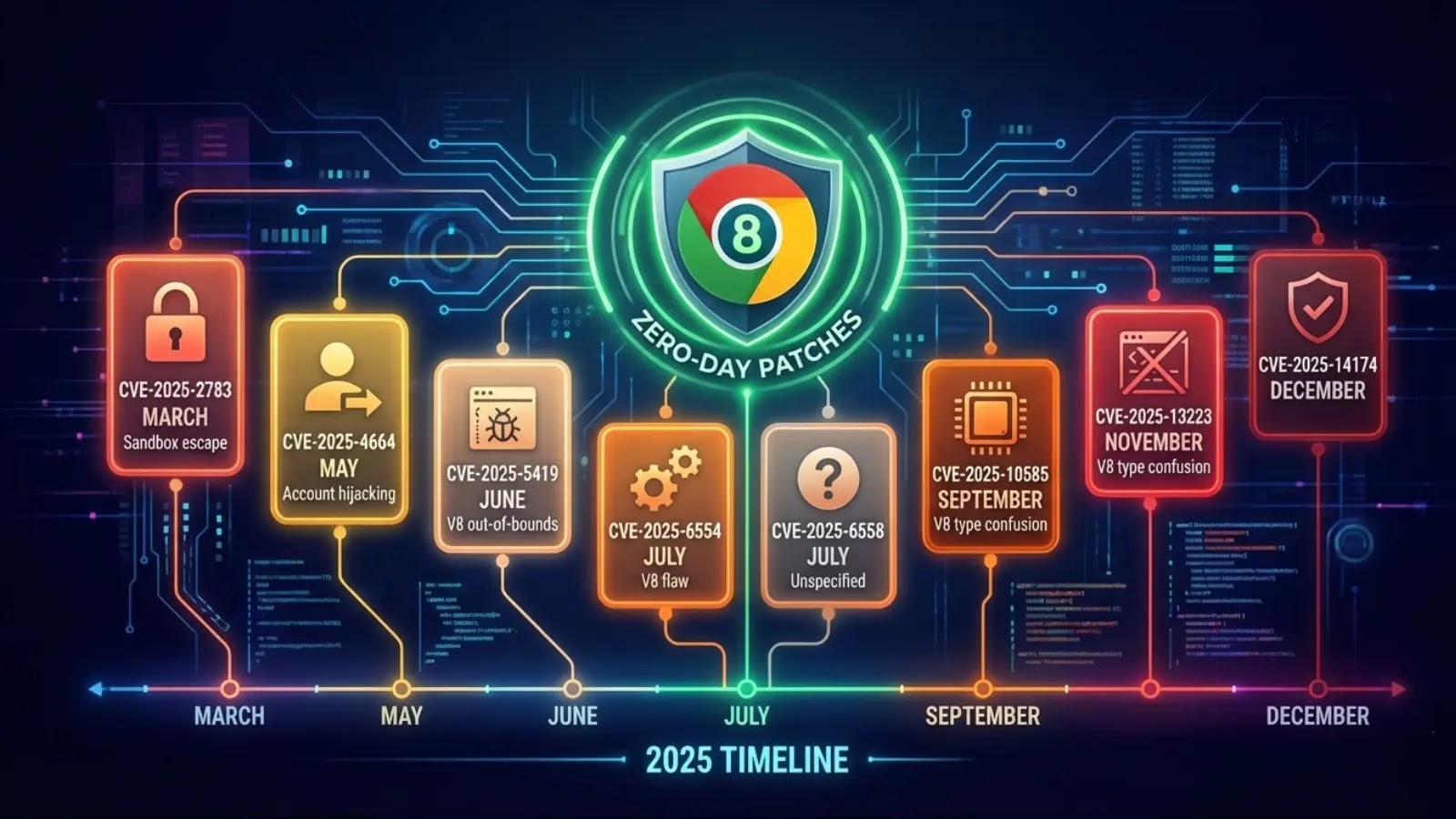
All through 2025, Google addressed a big wave of actively exploited zero-day vulnerabilities affecting its Chrome browser, patching a complete of eight essential flaws that threatened billions of customers worldwide.
These vulnerabilities, all labeled as excessive severity with CVSS scores averaging 8.5, underscore the persistent focusing on of the world’s hottest net browser by subtle menace actors, together with state-sponsored teams and business surveillance distributors.
The vulnerabilities spanned essential parts, together with the V8 JavaScript engine, sandbox safety mechanisms, and graphics rendering layers, with all eight added to CISA’s Identified Exploited Vulnerabilities catalog, mandating speedy remediation for federal companies and serving as pressing warnings for organizations globally.
2025 Chrome Zero-Day Panorama
The eight zero-day vulnerabilities patched in 2025 concentrated closely on Chrome’s V8 JavaScript and WebAssembly engine, which accounted for 4 of the eight flaws, representing 50% of all actively exploited vulnerabilities throughout this era.
This focus displays the strategic significance of V8 as an assault vector, given its position in executing JavaScript code throughout nearly all trendy net functions. The V8 engine processes hundreds of thousands of code executions every day, making any vulnerability inside this part instantly exploitable at an enormous scale.
The remaining vulnerabilities focused equally essential parts: two affected the ANGLE (Nearly Native Graphics Layer Engine) graphics abstraction layer used for GPU operations, one exploited the Mojo inter-process communication framework on Home windows, and one leveraged inadequate coverage enforcement in Chrome’s Loader part.
This distribution reveals attackers’ subtle understanding of Chrome’s multi-layered structure and their potential to determine weaknesses throughout totally different safety boundaries.
Google’s Menace Evaluation Group (TAG) performed a pivotal position in discovering and reporting six of the eight vulnerabilities, demonstrating the corporate’s inside safety analysis capabilities and its concentrate on monitoring nation-state actors and business surveillance distributors.
Exterior contributions got here from Kaspersky’s World Analysis and Evaluation Staff, which found the primary zero-day of 2025, and Apple’s Safety Engineering and Structure staff, which co-reported the ultimate vulnerability of the yr.
The temporal distribution of those vulnerabilities reveals a constant menace all through 2025, with patches deployed throughout eight separate months from March by December. In contrast to typical vulnerability disclosure patterns that usually cluster round main releases or safety audits, the regular stream of zero-day discoveries suggests ongoing lively exploitation makes an attempt by menace actors all year long.
March marked the start with CVE-2025-2783, a Mojo sandbox escape vulnerability exploited in Operation ForumTroll, a classy espionage marketing campaign focusing on Russian authorities organizations and media retailers.
Might noticed CVE-2025-4664, an account-hijacking vulnerability in Chrome’s Loader part that enabled cross-origin information leakage. In June, two essential V8 engine flaws, CVE-2025-5419 and CVE-2025-6554, had been actively exploited by way of kind confusion and out-of-bounds reminiscence entry.
July launched CVE-2025-6558, which exploited inadequate enter validation in ANGLE and GPU parts to realize sandbox escape. September noticed CVE-2025-10585, one other V8 kind confusion vulnerability that allowed heap corruption by way of crafted HTML pages.
November introduced CVE-2025-13223, the seventh zero-day, once more focusing on V8 with kind confusion strategies linked to espionage operations. December closed the yr with CVE-2025-14174, an out-of-bounds reminiscence entry vulnerability in ANGLE particularly affecting macOS customers.
This constant sample of exploitation demonstrates that Chrome stays a high-value goal for stylish adversaries regardless of Google’s substantial investments in safety hardening, together with applied sciences comparable to MiraclePtr for memory-corruption prevention and enhanced sandbox isolation.
Chrome Zero-Day Vulnerabilities Timeline
Technical Evaluation of Exploitation Strategies
V8 Sort Confusion Vulnerabilities
Sort confusion vulnerabilities dominated the 2025 Chrome zero-day panorama, accounting for 3 of the eight actively exploited flaws—CVE-2025-6554, CVE-2025-10585, and CVE-2025-13223.
These vulnerabilities exploit a basic attribute of JavaScript’s dynamic kind system and V8’s optimization methods. Sort confusion happens when the V8 engine misinterprets a reminiscence location as containing a special object kind than truly saved, resulting in reminiscence corruption that attackers can leverage for arbitrary code execution.
The V8 engine employs subtle just-in-time (JIT) compilation to realize excessive efficiency, making assumptions about object sorts throughout optimization.
The technical sophistication required to use V8 kind confusion vulnerabilities is substantial. Attackers should perceive V8’s inside object illustration, together with Hidden Lessons (Maps) that describe object layouts, in-object properties, and the JavaScript object construction inside V8’s heap.
Profitable exploitation usually includes heap spraying strategies to regulate reminiscence structure, manipulating object prototypes to create kind confusion situations, and leveraging the corrupted reminiscence state to realize learn/write primitives that allow code execution.
CVE-2025-10585, found by Google TAG on September 16, 2025, exemplifies this assault sample. The vulnerability allowed distant attackers to use heap corruption by kind confusion in V8, with Google confirming lively in-the-wild exploitation. The flaw required victims to go to a malicious web site containing crafted JavaScript, demonstrating the low barrier to exploitation as soon as the vulnerability is weaponized.
Sandbox Escape Mechanisms
Two of the eight zero-day vulnerabilities, CVE-2025-2783 and CVE-2025-6558, particularly enabled sandbox escape, representing essentially the most extreme class of browser vulnerabilities by permitting attackers to interrupt free from Chrome’s isolation mechanisms and entry the underlying working system.
CVE-2025-2783, found by Kaspersky in March 2025, focused the Mojo inter-process communication framework on Home windows platforms. Mojo serves as Chrome’s IPC mechanism, enabling communication between the browser’s remoted renderer processes and the privileged browser kernel course of.
The vulnerability stemmed from an incorrect deal with being offered in unspecified circumstances, permitting distant attackers to carry out sandbox escape by way of a malicious file.
When CVE-2025-2783 was exploited in Operation ForumTroll, attackers chained it with a separate renderer exploit to realize full system compromise.
The assault started with phishing emails containing hyperlinks to a malicious web site that exploited a renderer vulnerability, adopted by leveraging CVE-2025-2783 to flee the sandbox and deploy LeetAgent adware on victims’ techniques.
CVE-2025-6558, found by Google TAG in July 2025, exploited inadequate validation of untrusted enter in Chrome’s ANGLE part and GPU subsystem. ANGLE serves as a translation layer between Chrome’s rendering engine and device-specific graphics drivers, dealing with OpenGL ES API calls and changing them to native graphics APIs like Metallic on macOS or Direct3D on Home windows.
Reminiscence Corruption Exploitation
Three vulnerabilities, CVE-2025-5419, CVE-2025-6558, and CVE-2025-14174, centered on out-of-bounds reminiscence entry, a category of reminiscence corruption bugs that allow attackers to learn or write reminiscence exterior allotted buffer boundaries.
These vulnerabilities can result in info disclosure by out-of-bounds reads, permitting attackers to leak delicate information from adjoining reminiscence areas, or to arbitrary code execution by out-of-bounds writes that corrupt essential information constructions.
CVE-2025-5419, patched in June 2025, concerned out-of-bounds learn and write situations within the V8 engine that allowed distant attackers to set off heap corruption by way of crafted HTML pages.
CVE-2025-14174, found in December 2025, particularly affected Chrome’s ANGLE implementation on macOS, involving improper reminiscence dealing with that allowed reminiscence entry out of bounds in the course of the rendering of crafted HTML pages.
The technical exploitation of out-of-bounds reminiscence vulnerabilities usually includes rigorously controlling heap structure by strategies like heap spraying, crafting enter that triggers the out-of-bounds entry at a predictable reminiscence location, and leveraging the power to learn or write arbitrary reminiscence to assemble exploitation primitives.
Mitigations
The eight Chrome zero-day vulnerabilities actively exploited all through 2025 signify a classy and chronic menace panorama focusing on the world’s most generally used net browser.
The focus of vulnerabilities in core parts just like the V8 JavaScript engine and ANGLE graphics layer, mixed with the involvement of nation-state menace actors and business surveillance distributors, underscores Chrome’s standing as a essential assault floor in trendy cyber operations.
Past speedy patching, organizations ought to implement complete browser safety methods. Browser isolation applied sciences that execute net content material in distant, disposable environments can successfully sandbox potential threats away from endpoints, offering safety even towards unknown zero-days.
Community-based safety controls, together with next-generation firewalls, intrusion detection/prevention techniques, and net utility firewalls, can determine and block exploitation makes an attempt primarily based on behavioral indicators.
Google’s fast response capabilities and multi-layered safety structure have confirmed efficient in limiting publicity home windows and stopping widespread compromise, but the regular tempo of exploitation all year long demonstrates that decided adversaries proceed to seek out and weaponize Chrome vulnerabilities.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.