Each additional minute spent guessing throughout triage places your SOC in danger. When it’s unclear what a file does, whether or not it’s malicious, or how pressing it’s, actual threats slip by whereas time is wasted on noise.
Quick triage will depend on eradicating uncertainty early, so selections are primarily based on proof, not guesswork or incomplete alerts.
Listed here are 5 sensible ideas you should utilize to maneuver from alert to verdict quicker earlier than time works in opposition to you.
Tip #1: Verify Suspicious Information in a Secure, Managed Surroundings
Triage slows down when suspicious recordsdata are analyzed in fragments. Partial alerts create doubt, and doubt delays selections.
Operating suspicious recordsdata in a safe, remoted setting removes that uncertainty. As an alternative of guessing what may occur, you observe what truly occurs, with out exposing manufacturing programs, endpoints, or person machines to threat.
A sandbox, reminiscent of ANY.RUN supplies a managed area to soundly execute unknown recordsdata, hyperlinks, and attachments whereas capturing their conduct end-to-end.
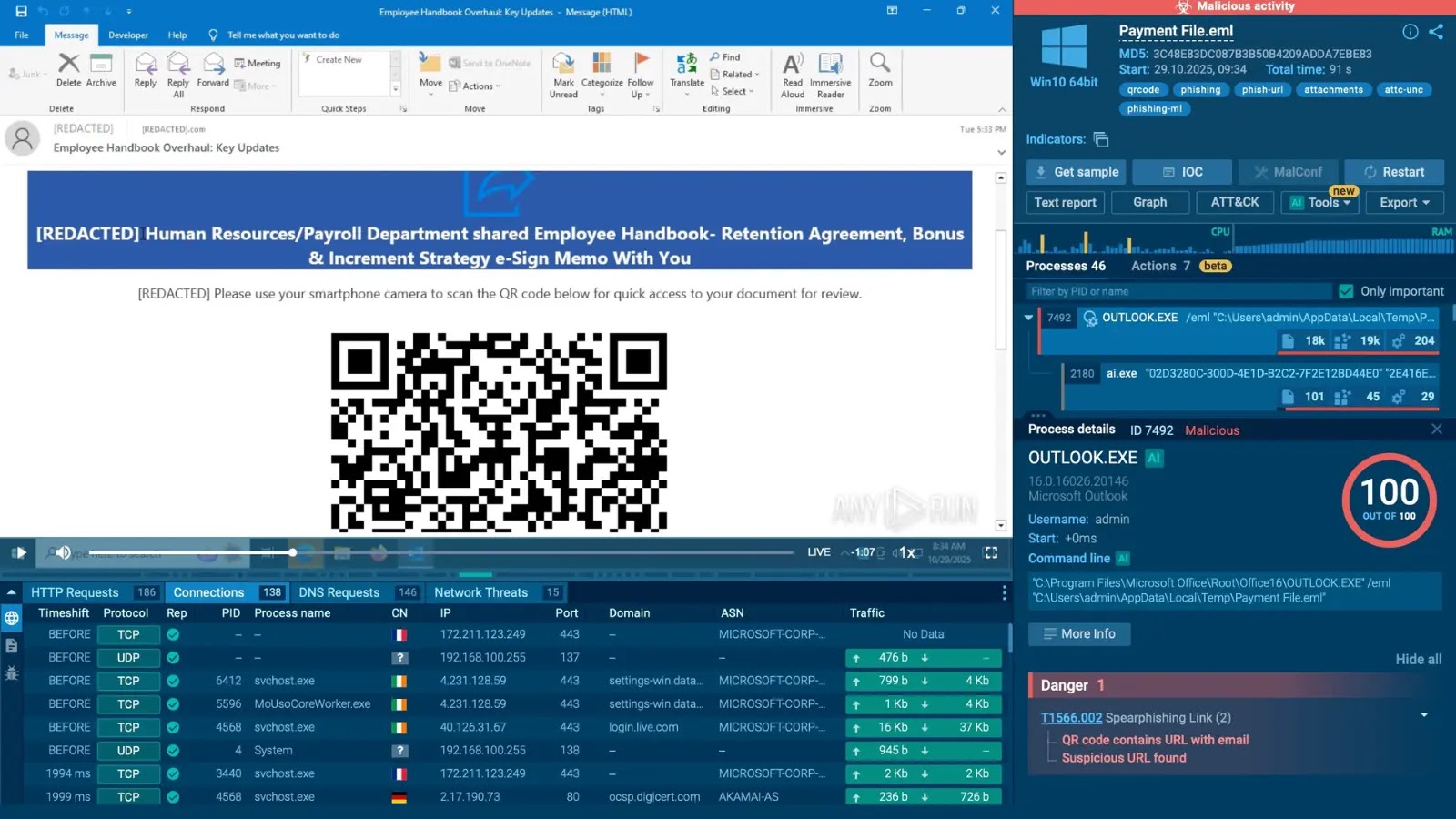
This enables groups to evaluate intent, scope, and urgency early, earlier than an alert turns into an incident. Verify an actual phishing assault analyzed in a secure setting
Complicated phishing assault uncovered inside ANY.RUN’s interactive sandbox in 35 seconds
In follow, most malicious conduct turns into seen throughout the first minute of execution. That early visibility is commonly sufficient to substantiate whether or not a risk is actual, prioritize appropriately, and resolve the following step, protecting triage quick and contained.
Establish actual threats throughout the first 60 seconds to streamline and improve triage within the ANY.RUN sandbox, Get Began Now
Tip #2: Use Interactivity to Expose Full Risk Habits
Many threats don’t reveal themselves routinely. They watch for a click on, a macro, or a person motion earlier than exhibiting actual intent.
With out interactivity, key conduct stays hidden and triage stalls. By actively partaking with a suspicious file, clicking parts, enabling macros, or following hyperlinks, you possibly can set off the actions attackers anticipate and expose the total assault movement early.
For instance, the ANY.RUN sandbox permits groups to work together with threats at any level throughout execution, making it simpler to uncover actual conduct inside minutes.
Fixing CAPTCHA inside ANY.RUN’s sandbox
The result’s quicker readability, fewer blind spots, and extra assured triage selections. The sort of early conduct publicity is commonly sufficient to decide intent, assess urgency, and resolve the following step with out extended investigation.
Tip #3: Mix Automation with Interactivity
Automation is crucial for quick triage, however by itself, it has limits. Totally automated execution typically stops the place person motion is required, proper the place many fashionable assaults start.
The simplest method is combining automation with interactivity. Automation handles the repetitive steps, whereas interactivity ensures nothing vital is missed.
Some superior platforms take this additional. For instance, ANY.RUN helps automated interactivity, the place the sandbox itself performs actions analysts would usually must do manually.
This contains fixing verification challenges, following hidden or obfuscated hyperlinks, and extracting and opening malicious URLs embedded in QR codes.
ANY.RUN’s sandbox detonates a malicious hyperlink hidden underneath a QR code
By eradicating the necessity to click on by each step by hand, automated interactivity exposes malicious conduct quicker and reduces the time spent chasing hidden payloads.
Triage turns into faster, extra constant, and much much less depending on handbook effort.
Let automated interactivity expose what handbook evaluation typically misses, Strive ANY.RUN Now
Tip #4: Scale Triage with IOCs, AI Summaries, and Sigma Guidelines
Triage slows down when each investigation begins from zero. Even confirmed threats typically go away behind indicators with out sufficient context to be reused confidently.
Contextual IOCs and AI summaries assist shut that hole by explaining not simply what was detected, however why it issues, making prioritization and handoffs quicker.
For instance, ANY.RUN enriches indicators with knowledge from 15,000 organizations and over 500,000 safety professionals, giving IOCs real-world context and serving to groups rapidly choose whether or not a sign is remoted noise or a part of an energetic risk.
AI-generated summaries clarify what occurred throughout execution and why it issues, permitting quicker selections and smoother handoffs with out handbook reporting.
AI Sigma Guidelines displayed inside ANY.RUN sandbox
AI Sigma Guidelines flip verified malicious conduct into reusable detection logic, so one investigation strengthens future detection as an alternative of ending with a closed alert.
The result’s quicker triage at present and a detection course of that improves repeatedly, lowering duplicate work and long-term alert quantity.
Tip #5: Deliver Risk Information into Your Current Workflow
Triage breaks down when risk intelligence lives exterior the instruments groups already use. Even high-quality findings lose worth in the event that they must be manually copied, reformatted, or rechecked earlier than motion will be taken.
Risk knowledge constructed from exercise throughout 15,000 organizations is best when it flows instantly into acquainted workflows.
When indicators, verdicts, and behavioral insights will be built-in into SIEM, SOAR, EDR, and case administration programs, groups can act on them instantly, with out altering how they work.
ANY.RUN’s TI Feeds offering contemporary knowledge into present workflows
With ANY.RUN’s TI Feeds, this shared intelligence turns into repeatedly out there, not simply case by case.
Recognized malicious patterns, infrastructure, and behaviors floor early within the investigation, serving to groups prioritize alerts quicker and keep away from chasing noise.
The profit is a smoother triage course of, earlier selections, and quicker response, powered by intelligence that’s already been validated in real-world environments.
Flip Quicker Triage into a Day by day Benefit
Tremendous-fast triage is all about eradicating friction at each step; seeing conduct early, exposing full assault chains, automating repetitive work, and reusing what your staff already discovered.
When these practices come collectively, the affect on triage is measurable:
Lower MTTR by as much as 21 minutes by reaching clear verdicts earlier and lowering back-and-forth throughout investigations
Obtain as much as 3× increased investigation effectivity by minimizing handbook steps and repetitive evaluation
Expose most malicious conduct throughout the first 60 seconds, permitting quicker prioritization and response
Strive ANY.RUN now to see how a lot time triage can save your SOC.
Let automated interactivity expose what handbook evaluation typically misses, Strive ANY.RUN Now