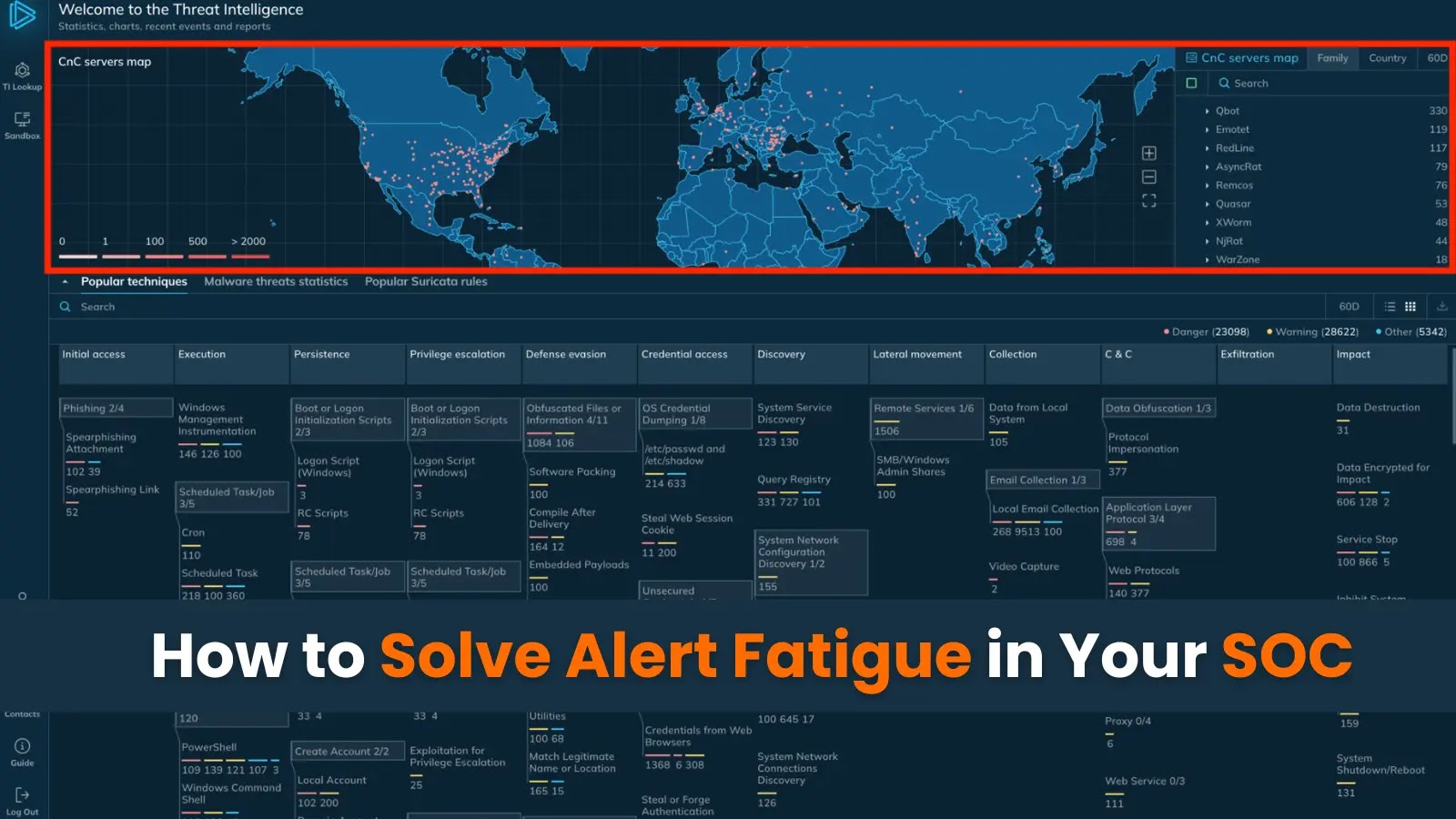
NeuroSploitv2 is an AI-powered penetration testing framework that automates essential points of offensive safety operations by superior language fashions.
The framework, out there on GitHub, integrates with a number of LLM suppliers, together with Claude, GPT, Gemini, and Ollama, to allow specialised vulnerability evaluation and exploitation methods.
The framework stands out for its modular structure, which options specialised AI agent roles designed for particular safety duties.
These brokers embrace bug bounty hunters for net software vulnerability discovery and crimson group operators for simulated assault campaigns. Malware analysts for risk evaluation, and blue group specialists for defensive operations.
Every agent position operates with tailor-made parameters and power entry controls, enabling managed and moral safety operations.
NeuroSploitv2 makes use of superior strategies to scale back false outputs, which is essential when utilizing LLMs for safety work.
The framework employs grounding strategies, self-reflection mechanisms, and consistency checks to make sure LLM-generated safety assessments stay grounded in actuality.
Configurable safeguards add additional security, together with key phrase filtering and content material checks. The framework’s extensibility distinguishes it from earlier penetration testing instruments.
FeatureDescriptionMulti-LLM SupportIntegrates Claude, GPT, Gemini, and Ollama with versatile supplier selectionAI Agent RolesPre-configured personas together with Purple Group, Bug Bounty Hunter, Malware Analyst, Blue Group, and OWASP/CWE ExpertsHallucination MitigationImplements grounding, self-reflection, and consistency checks to scale back LLM errorsGranular LLM ProfilesCustomizable temperature, token limits, context ranges, and caching per agentTool IntegrationSupports Nmap, Metasploit, Subfinder, Nuclei, SQLMap, Burpsuite, and HydraSafety GuardrailsKeyword filtering, content material validation, and moral adherence controlsInteractive ModeConversational CLI interface for direct agent management and executionStructured ReportingJSON marketing campaign outcomes and HTML experiences for workflow integrationMarkdown PromptsDynamic immediate templates for context-aware agent instructionsExtensibilityCustom agent roles and instruments simply added through JSON configuration
Customers can combine exterior safety utilities equivalent to Nmap, Metasploit, Subfinder, Nuclei, and SQLMap through a simple JSON configuration.
Granular LLM profiles enable safety groups to customise parameters, together with temperature settings, token limits, context ranges, and caching conduct for every agent position.
In line with the GitHub advisory, NeuroSploitv2 is designed with operational flexibility, permitting organizations to run the framework through command-line interfaces for automated scanning or use interactive mode for conversational testing.
The framework generates structured JSON outcomes and human-readable HTML experiences, facilitating integration into present safety workflows.
NeuroSploit v2 Set up
The open-source MIT-licensed challenge represents a big shift towards AI-augmented offensive safety.
Nevertheless, safety professionals ought to acknowledge that LLM-generated penetration testing requires cautious validation and skilled oversight.
The framework is designed to enhance human experience relatively than substitute it, with moral concerns and operational safety constructed into its core structure.
Growth continues with common updates to agent capabilities and power integrations, positioning NeuroSploitv2 as an evolving resolution for modern penetration testing challenges.