The cybersecurity panorama in 2025 has been marked by an unprecedented surge in crucial vulnerabilities, with over 21,500 CVEs disclosed within the first half of the yr alone, representing a 16-18% improve in comparison with 2024.
Amongst these, a choose group of vulnerabilities stands out because of their distinctive severity, lively exploitation within the wild, and potential for enterprise-wide compromise.
This complete evaluation examines the ten most important high-risk vulnerabilities of 2025, detailing their technical mechanisms, real-world impression, and implications for organizations worldwide.
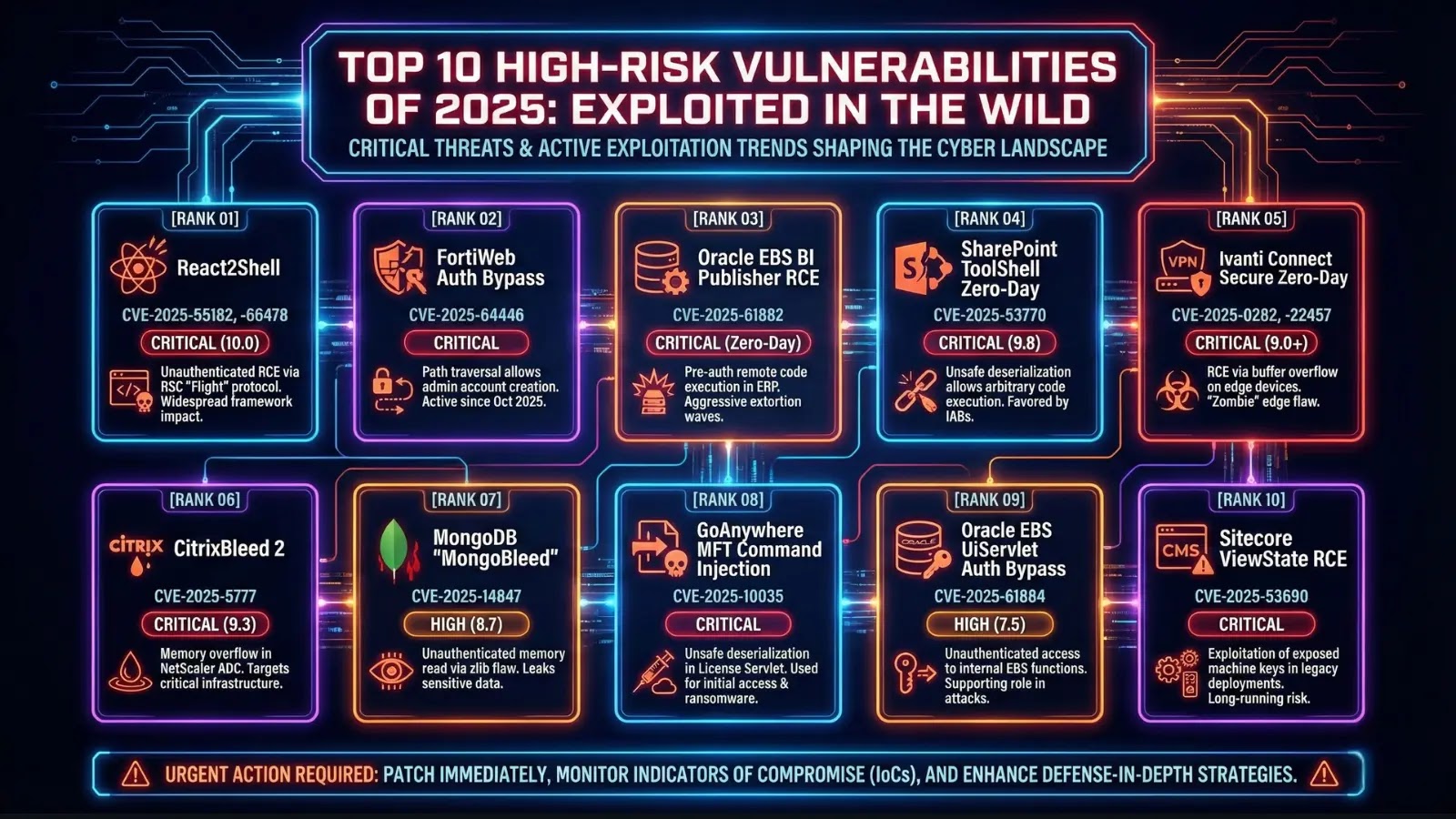
10 Excessive-Danger Vulnerabilities
Vulnerability & CVESeverityAttack VectorAuthenticationKey Mechanism & Impact1. Langflow Unauthorized Code Injection(CVE-2025-3248)Crucial (9.8)NetworkNone RequiredMechanism: Unsafe code validation in an API endpoint permits arbitrary code execution by way of Python decorators.Impression: Compromise of AI utility infrastructure and enterprise knowledge pipelines. Actively exploited.2. Microsoft SharePoint Server RCE Chain(CVE-2025-53770, 53771)Crucial (9.8)NetworkNone RequiredMechanism: Multi-stage assault bypassing authentication and exploiting unsafe deserialization.Impression: Full system management, knowledge theft, and lateral motion. Confirmed lively exploitation towards authorities/finance sectors.3. Sudo Improper Exterior Useful resource Reference(CVE-2025-32463)Excessive (7.8-9.3)LocalLow-Privileged UserMechanism: Race situation in sudo with –chroot permits loading malicious shared libraries.Impression: Native privilege escalation to root. Impacts an unlimited variety of Linux/Unix programs globally.4. Docker Desktop Insufficient Entry Management(CVE-2025-9074)Crucial (7.8-9.3)LocalNone RequiredMechanism: Unauthenticated Docker Engine API publicity to containers by way of a hardcoded subnet.Impression: Container escape, host system compromise (Home windows), and management of Docker infrastructure.5. WhatsApp & Apple Picture I/O Exploit Chain(CVE-2025-55177, 43300)Crucial (10.0)Community (Zero-Click on)None RequiredMechanism: WhatsApp auth bypass mixed with Apple Picture I/O out-of-bounds write by way of malicious photos.Impression: Zero-click distant code execution on iOS/macOS. Utilized in focused spyware and adware assaults towards journalists.6. SGLang Giant Mannequin Inference Framework RCE(CVE-2025-10164)Excessive (7.3)NetworkNone RequiredMechanism: Unsafe deserialization of untrusted knowledge in a mannequin weights replace endpoint.Impression: Distant code execution on GPU servers, probably compromising AI mannequin IP and inference infrastructure.7. Unitree Robotic BLE Vulnerabilities(CVE-2025-35027, 60250, 60251)Excessive (7.3-8.2)Adjoining (Bluetooth)Restricted RequiredMechanism: BLE command injection by way of static keys and hardcoded credentials.Impression: Root-level management of robots. Potential for “viral” propagation in robotic swarms.8. FortiWeb Distant Code Execution Chain(CVE-2025-64446, 58034)Crucial (9.8)NetworkNone RequiredMechanism: Authentication bypass by way of path traversal to legacy CGI interfaces, adopted by RCE.Impression: Full management of WAF gadgets, enabling community pivot, visitors interception, and protection disablement. Actively exploited.9. Samsung Cell Machine Quram Library RCE(CVE-2025-21042)Excessive (8.8)Community (Messaging)None RequiredMechanism: Out-of-bounds write in picture processing library triggered by malicious DNG recordsdata.Impression: Distant code execution used to ship LANDFALL spyware and adware for complete system surveillance.10. React Server Elements Code Injection(CVE-2025-55182)Crucial (10.0)NetworkNone RequiredMechanism: Unsafe payload deserialization resulting in prototype air pollution and RCE.Impression: Pre-authentication RCE affecting main internet frameworks like Subsequent.js. Requires solely a single HTTP request.
1. Langflow Unauthorized Code Injection Vulnerability (CVE-2025-3248)
Severity: Crucial | CVSS Rating: 9.8 | Assault Vector: Community | Authentication: None Required
The Langflow vulnerability represents a crucial flaw in one of the crucial standard open-source AI orchestration platforms, with over 79,000 GitHub stars signifying widespread adoption throughout enterprise environments.
CVE-2025-3248 stems from unsafe code validation logic within the unauthenticated /api/v1/validate/code endpoint, enabling distant attackers to execute arbitrary code with none authentication or authorization checks.
The vulnerability’s exploitation mechanism is especially insidious, leveraging Python’s decorator analysis conduct.
Attackers can embed malicious payloads inside decorators, triggering code execution in the course of the parsing part fairly than throughout operate execution.
When Langflow processes user-submitted code via Python’s ast.parse(), compile(), and exec() features, the decorator expression is evaluated instantly, permitting attackers to realize distant code execution earlier than the code ever runs.
This system bypasses conventional sandbox protections and enter validation mechanisms designed to establish malicious intent at runtime.
The sensible exploitation path is easy: an attacker sends a crafted HTTP POST request to the weak endpoint with a specifically constructed Python payload embedded in a decorator.
The payload executes with the privileges of the Langflow course of, probably compromising your complete AI utility infrastructure, enterprise knowledge pipelines, and related programs.
Given Langflow’s position in constructing AI-powered brokers and workflows for monetary providers, healthcare, and know-how sectors, compromise of a weak occasion represents a crucial danger to organizational operations.
Exploitation proof emerged early, with CVE-2025-3248 added to CISA’s Recognized Exploited Vulnerabilities (KEV) catalog on Might 5, 2025, indicating lively weaponization in menace actor arsenals.
The vulnerability impacts all variations previous to 1.3.0, creating a large window of publicity for organizations that haven’t actively maintained their deployment variations.
2. Microsoft SharePoint Server RCE Exploit Chain (CVE-2025-53770, CVE-2025-53771)
Severity: Crucial | CVSS Rating: 9.8 | Assault Vector: Community | Authentication: None Required
The SharePoint vulnerability chain, internally dubbed “ToolShell,” is among the many most harmful enterprise assaults found in 2025.
CVE-2025-53770 constitutes a crucial unauthenticated distant code execution flaw affecting on-premises Microsoft SharePoint Server 2016, 2019, and Subscription Version.
On July 19-20, 2025, Microsoft and CISA confirmed lively exploitation of this vulnerability, with confirmed victims together with authorities businesses and monetary establishments.
The exploitation chain operates via a three-stage course of that systematically dismantles SharePoint’s safety structure.
First, attackers bypass authentication via crafted HTTP POST requests to the legacy WebPart editor endpoint (/_layouts/15/ToolPane.aspx?DisplayMode=Edit).
By setting a solid Referer header pointing to the SignOut endpoint, attackers trick SharePoint into processing unauthenticated requests as legit, inner system calls.
This authentication bypass exploits a belief relationship between SharePoint endpoints that was supposed for inner workflows however could be abused remotely.
Within the second stage, as soon as authenticated entry is achieved, attackers deploy a malicious .aspx file (sometimes named spinstall0.aspx) to the SharePoint layouts listing.
This file doesn’t operate as a conventional webshell; as a substitute, it extracts cryptographic secrets and techniques from the server’s configuration, together with the ValidationKey and DecryptionKey utilized by ASP.NET to signal and decrypt ViewState payloads.
These keys are elementary to SharePoint’s deserialization safety mannequin.
The ultimate stage leverages the stolen cryptographic materials to craft legitimate, signed __VIEWSTATE tokens containing malicious payloads.
When these tokens are submitted to a different SharePoint endpoint by way of GET request, the server deserializes them with out further validation, executing arbitrary code with the privileges of the applying pool identification (sometimes NT AUTHORITYIUSR).
This method exploits unsafe deserialization of untrusted knowledge a flaw that has plagued .NET functions for years.
The vulnerability’s impression extends past particular person compromises. Attackers can execute PowerShell instructions, entry delicate doc libraries, create new administrative accounts, harvest credentials, and pivot laterally into related programs.
Microsoft confirmed that CVE-2025-53770 and CVE-2025-53771 are associated to 2 prior vulnerabilities (CVE-2025-49704 and CVE-2025-49706) disclosed at Pwn2Own Berlin, with the newer vulnerabilities offering “extra sturdy protections” than the interim patches.
The continued discovery of variants on this assault household underscores the systematic nature of the underlying design flaw.
3. Sudo Improper Exterior Useful resource Reference Vulnerability (CVE-2025-32463)
Severity: Excessive | CVSS Rating: 7.8-9.3 | Assault Vector: Native | Authentication: Low-Privileged Person Required
CVE-2025-32463 is a crucial privilege-escalation vulnerability in sudo, the basic Unix access-control utility current on just about each Linux and Unix system worldwide.
Disclosed on June 30, 2025, by Stratascale Cyber Analysis Unit, this vulnerability permits native low-privileged customers to escalate to root privileges by manipulating configuration recordsdata when utilizing the –chroot (-R) possibility.
The vulnerability’s root trigger originates from a change launched in sudo model 1.9.14, the place path decision started occurring inside the chroot surroundings earlier than the sudoers file is evaluated.
This timing situation creates a race situation that attackers can exploit by inserting malicious configuration recordsdata into their managed listing.
When a person runs sudo with the -R possibility into an attacker-controlled surroundings, sudo reads the malicious nsswitch.conf configuration file first.
This file can instruct the system to load a customized shared library (woot1337.so.2) crafted by the attacker. The exploit approach is remarkably simple, requiring solely primary C programming expertise.
An attacker creates a malicious shared library with a constructor operate that instantly executes when the library is loaded.
The constructor calls setreuid(0,0) and setregid(0,0) to realize root privileges, then spawns a root-level bash shell.
As soon as the malicious library masses, the attacker immediately obtains full system management without having to use any subsequent vulnerabilities or race circumstances.
The vulnerability impacts sudo variations 1.9.14–1.9.17 (secure department) and impacts a smaller however nonetheless important 1.8.8–1.8.32 (legacy department).
Organizations working any of those variations face crucial danger, because the exploit requires solely native entry and low privileges a typical state of affairs following profitable phishing, compromised credentials, or insider threats.
The sensible exploitation timeline is compressed considerably: from preliminary compromise with low privileges to finish system management in minutes.
CVE-2025-32463 was added to CISA’s KEV catalog in July 2025, with Canada’s Cyber Centre and quite a few nationwide CERT businesses issuing emergency advisories.
The vulnerability impacts crucial infrastructure, cloud environments, and enterprise programs globally, making it a prime precedence for patch administration groups.
4. Docker Desktop Insufficient Entry Management Vulnerability (CVE-2025-9074)
Severity: Crucial | CVSS Rating: 7.8-9.3 | Assault Vector: Native | Authentication: None Required
CVE-2025-9074 exposes a elementary entry management failure in Docker Desktop, affecting each Home windows and macOS variations previous to 4.44.3.
The vulnerability permits domestically working Linux containers to entry the Docker Engine API on the hardcoded subnet deal with 192.168.65.7:2375 with none authentication, no matter Enhanced Container Isolation (ECI) settings.
Docker Desktop implements a networking bridge between host programs and Linux containers, utilizing a digital subnet for inner communication.
The vulnerability arises as a result of Docker Desktop exposes its engine API on this subnet with out implementing network-level authentication or encryption.
A malicious container, whether or not launched by a person or deployed via a provide chain assault, could make unauthenticated requests to the Docker Engine API and execute arbitrary instructions with full engine privileges.
The exploitation vector expands considerably relying on the host working system.
On Docker Desktop for Home windows utilizing WSL2 backend, attackers can mount the host’s filesystem with administrative privileges equal to the Docker Desktop person, learn delicate recordsdata, and set up persistent malware by modifying system DLLs.
On macOS, whereas remoted by the applying sandbox, attackers can backdoor the Docker utility itself and acquire management over all containers and pictures.
In each eventualities, the attacker escalates from a compromised container to controlling your complete Docker infrastructure.
The sensible impression manifests throughout a number of assault eventualities.
First, provide chain assaults can inject malicious containers into enterprise registries when deployed in Docker Desktop environments. These containers obtain quick Docker Engine entry and compromise the event workstation.
Second, weak improvement workstations change into pivotal for lateral motion, as Docker Desktop is usually run with elevated privileges and incorporates credentials for manufacturing registries and orchestration platforms.
Third, the vulnerability allows fast containerized botnet creation, the place compromised nodes commandeer further containers to type distributed assault infrastructure.
Docker addressed CVE-2025-9074 in model 4.44.3, implementing authentication necessities for Docker Engine API entry from containers.
Nevertheless, the broad deployment of Docker Desktop throughout improvement groups, with auto-update continuously disabled, has created a considerable put in base of weak programs.
5. Mixed Exploit Chain: WhatsApp Authorization Validation Vulnerability and Apple Picture I/O Out-of-Bounds Write (CVE-2025-55177, CVE-2025-43300)
Severity: Crucial | CVSS Rating: 10.0 (Mixed) | Assault Vector: Community (WhatsApp), Zero-Click on | Authentication: None Required
The chained vulnerability combining CVE-2025-55177 in WhatsApp with CVE-2025-43300 in Apple’s ImageIO framework represents one in all 2025’s most subtle assault chains, focusing on journalists and human rights defenders with state-sponsored spyware and adware.
This exploit chain operationalizes a zero-click assault methodology, requiring no person interplay in any respect to compromise iOS and macOS gadgets.
CVE-2025-55177 stems from incomplete authorization checks in WhatsApp’s linked system synchronization messages.
WhatsApp permits customers to hyperlink secondary gadgets via a synchronization course of; nonetheless, the authorization validation fails to correctly confirm that synchronization messages originate from legit linked gadgets.
This authorization bypass allows distant attackers to pressure arbitrary content material processing heading in the right direction gadgets by triggering malicious synchronization messages containing URLs pointing to attacker-controlled servers.
CVE-2025-43300 represents an out-of-bounds write vulnerability in Apple’s Picture I/O framework, which handles picture processing throughout iOS, iPadOS, and macOS.
The vulnerability exists within the parsing logic for DNG (Digital Damaging) and JPEG Lossless picture codecs.
A validation hole between TIFF metadata and embedded JPEG streams causes the parser to allocate buffers based mostly on SamplesPerPixel metadata, whereas the JPEG decoder later makes use of a unique element rely from the picture stream.
When these values battle, extra pixel knowledge is written than the buffer was sized for, leading to a traditional out-of-bounds write vulnerability.
The assault chain operates as follows: An attacker sends a synchronization message by way of WhatsApp, exploiting CVE-2025-55177, forcing the goal system to course of a malicious DNG picture file from a distant URL.
Because the system processes the picture, Picture I/O invokes weak code paths, writing past allotted reminiscence boundaries.
This reminiscence corruption allows arbitrary code execution inside the Picture I/O course of, which operates with excessive privileges for media processing.
Second-stage payloads can then set up persistence and coordinate surveillance performance.
The sophistication lies within the coordinated deployment: WhatsApp’s authorization bypass offers zero-click supply, whereas the Picture I/O vulnerability offers dependable code execution.
Mixed, these create a whole exploitation chain requiring zero person interplay.
WhatsApp confirmed that roughly 200 people, primarily journalists and human rights defenders within the Center East, have been focused over a three-month interval.
Apple rushed emergency patches in August 2025, and WhatsApp launched updates shortly thereafter, however the incident underscores the systematic nature of nation-state surveillance operations focusing on weak populations.
6. SGLang Giant Mannequin Inference Framework Distant Code Execution (CVE-2025-10164)
Severity: Excessive | CVSS Rating: 7.3 | Assault Vector: Community | Authentication: None Required
CVE-2025-10164 represents a crucial vulnerability in SGLang, an more and more standard giant language mannequin inference framework used to serve AI fashions in manufacturing environments.
The vulnerability arises from unsafe deserialization of untrusted knowledge within the /update_weights_from_tensor endpoint, permitting distant code execution on GPU servers working weak variations.
Machine studying inference frameworks like SGLang should effectively switch serialized tensor knowledge (mathematical arrays) between purchasers and servers, significantly when distributing computations throughout GPU clusters.
Nevertheless, deserialization of untrusted serialized objects represents a widely known vulnerability sample in Python functions.
SGLang’s implementation fails to implement sufficient validation earlier than deserializing the serialized_named_tensors parameter, permitting attackers to inject malicious payloads that execute arbitrary code throughout deserialization.
The sensible impression extends past particular person compromised servers. Manufacturing AI inference clusters sometimes include hundreds of nodes working similar weak variations of SGLang.
A single compromised node turns into a pivot level for lateral motion throughout your complete cluster, enabling attackers to manage distributed mannequin serving infrastructure.
This infrastructure typically incorporates helpful mental property (skilled mannequin weights), buyer knowledge for inference, and credentials for connecting to upstream programs.
The vulnerability gained consideration inside the AI safety group because of the fast response from SGLang maintainers and collaborative coordination with potential victims to forestall widespread in-the-wild exploitation.
This proactive incident response prevented the vulnerability from being weaponized at scale, highlighting how fast disclosure and coordinated patching can mitigate zero-day danger even for rising applied sciences.
7. Unitree Robotic BLE Vulnerabilities (CVE-2025-35027, CVE-2025-60250, CVE-2025-60251)
Severity: Excessive | CVSS Rating: 7.3-8.2 | Assault Vector: Adjoining (Bluetooth) | Authentication: Restricted Required
CVE-2025-35027 represents a crucial command injection vulnerability in a number of robotic merchandise from Unitree, together with the favored Go2 (quadruped) and G1 (humanoid) robotic strains.
The vulnerability permits attackers to realize root-level command execution on affected robots via the Bluetooth Low Power (BLE) interface, creating dangers for bodily programs and important infrastructure functions.
Unitree robots deliberately expose a WiFi configuration interface over BLE to permit customers to configure community connectivity with out bodily entry.
The vulnerability chain combines three distinct flaws: CVE-2025-60250 (static encryption key in BLE), CVE-2025-60251 (hardcoded authentication string), and CVE-2025-35027 (command injection).
An attacker can pair with the robotic utilizing the static AES key and IV, then authenticate utilizing the hardcoded “unitree” string.
As soon as authenticated, the attacker can provide malicious WiFi SSID or password strings containing shell metacharacters (pipe, semicolon, command substitution syntax).
These values are handed on to the wpa_supplicant_restart.sh script by way of sudo, executed with root privileges.
An attacker can instantly acquire root shell entry or inject arbitrary instructions for persistence, knowledge exfiltration, or bodily system compromise.
In eventualities the place a number of robots function in proximity (swarms, warehouse deployments, analysis amenities), a single compromised robotic can propagate the assault to neighboring robots via automated exploitation.
The disclosure famous {that a} robotic below attacker management can transfer towards different robots and compromise them routinely a “viral” propagation sample.
Purposes of those robots in security-sensitive environments (bomb defusal, hostage rescue, crucial infrastructure inspection) create elevated danger profiles the place system compromise may endanger lives.
As of September 2025, all Unitree Go2, G1, H1, and B2 gadgets with present firmware variations stay weak, with the seller indicating fixes could require years to implement.
8. FortiWeb Distant Code Execution Vulnerability Chain (CVE-2025-64446, CVE-2025-58034)
Severity: Crucial | CVSS Rating: 9.8 | Assault Vector: Community | Authentication: None Required
CVE-2025-64446 represents a crucial authentication bypass vulnerability in Fortinet FortiWeb internet utility firewalls, affecting a number of variations and actively exploited since early October 2025.
The vulnerability combines two design flaws: relative path traversal (CWE-23) and authentication bypass by way of alternate path (CWE-288), enabling unauthenticated attackers to create administrative accounts and acquire full management over weak gadgets.
FortiWeb implements a contemporary REST API for administrative administration, which is meant to require authentication for all operations.
Nevertheless, legacy CGI-based administrative interfaces stay current within the system for backward compatibility.
An attacker can craft an HTTP POST request to /api/v2.0/cmdb/system/admin with particular URL encoding that routes the request via the REST API’s path traversal logic to the unprotected CGI processor.
The CGI processor depends on an HTTP header (CGIINFO) for authentication fairly than commonplace HTTP authentication mechanisms, making a bypass situation.
By sending a specifically crafted POST request with the proper CGIINFO header worth, attackers bypass all authentication checks and straight invoke the CGI script liable for person creation.
The attacker can instantly create a brand new administrator account with full privileges, then use these credentials to entry the administration interface and reconfigure the WAF to facilitate additional assaults.
FortiWeb gadgets function as crucial safety infrastructure, typically positioned straight at community boundaries defending internet functions and APIs.
A compromised FortiWeb occasion turns into a robust pivot level for inner community entry, as attackers can disable safety guidelines, create visitors forwarding, harvest credentials transiting via the WAF, and keep persistent backdoors.
The vulnerability’s severity prompted CISA so as to add CVE-2025-64446 to its KEV catalog with a compulsory remediation deadline of November 21, 2025.
Exploitation proof emerged in public disclosures from safety analysis organizations, and watchToR printed Python-based proof-of-concept code demonstrating dependable exploitation.
The mixture of widespread web publicity of FortiWeb gadgets (for distant entry and DDoS safety) with the unauthenticated nature of the vulnerability created a major assault floor.
9. Samsung Cell Machine Quram Picture Parsing Library Distant Code Execution (CVE-2025-21042)
Severity: Excessive | CVSS Rating: 8.8 | Assault Vector: Community (by way of Messaging Apps) | Authentication: None Required
CVE-2025-21042 represents a crucial out-of-bounds write vulnerability in Samsung’s libimagecodec.quram.so picture processing library, utilized by hundreds of thousands of older Samsung Galaxy gadgets working Android variations 13-16.
The vulnerability was actively exploited within the wild to ship the LANDFALL spyware and adware malware focusing on people within the Center East.
Samsung’s Quram picture processing library handles DNG (Digital Damaging) format photos, a lossless uncooked picture format generally utilized by skilled photographers.
A malicious DNG file with rigorously crafted picture headers can set off an out-of-bounds write situation within the library’s parsing code, resulting in reminiscence corruption and arbitrary code execution.
Researchers found that attackers embedded malicious DNG recordsdata inside ZIP archives, then appended these archives to DNG recordsdata for supply by way of messaging functions like WhatsApp.
The LANDFALL spyware and adware marketing campaign leveraged this vulnerability to ship a two-stage assault: a loader element (b.so) establishing backdoor performance, and a SELinux coverage manipulator (l.so) designed to grant elevated permissions and persistence.
As soon as the DNG file is processed, probably via automated thumbnail era or metadata extraction in messaging apps, the vulnerability triggers, executing the embedded malware with out person interplay.
The sensible impression on system safety is extreme. LANDFALL enabled complete surveillance together with microphone recording, location monitoring, picture assortment, contact harvesting, and name log exfiltration.
The vulnerability impacts flagship Samsung Galaxy fashions (S22, S23, S24, Z Fold4, Z Flip4) that stay extensively deployed in weak configurations.
Whereas Samsung patched the vulnerability in April 2025, the prolonged timeline of exploitation within the wild (spanning July 2024 via early 2025) signifies hundreds of thousands of gadgets stay in danger.
Android fragmentation the gradual deployment of safety patches throughout system fashions and carriers—creates a protracted tail of weak gadgets in lively use.
Not like iOS the place Apple controls your complete ecosystem, Android system fragmentation means many customers stay weak for prolonged intervals post-disclosure.
10. React Server Elements Code Injection Vulnerability (CVE-2025-55182)
Severity: Crucial | CVSS Rating: 10.0 | Assault Vector: Community | Authentication: None Required
CVE-2025-55182 represents a crucial pre-authentication distant code execution vulnerability in React Server Elements, disclosed on December 3, 2025.
The vulnerability achieves the utmost CVSS rating of 10.0 because of its full lack of authentication necessities and its impression on extensively deployed fashionable internet frameworks, together with Subsequent.js, React Router, and numerous Vite/Parcel implementations.
React Server Elements signify an rising paradigm in internet improvement, permitting server-side logic to be composed with client-side elements with out express API definitions.
Nevertheless, this comfort introduces safety complexity. The vulnerability exists in how React Server Elements deal with payload deserialization on HTTP requests focusing on Server Perform endpoints.
When processing incoming requests, React deserializes payloads with out sufficient validation, making a direct pathway for attackers to execute arbitrary code.
The vulnerability exploits prototype air pollution in JavaScript’s prototype chain. An attacker crafts a specifically structured JSON payload that, when deserialized, pollutes the prototype of JavaScript objects.
By referencing native Node.js features like child_process.execSync, attackers can escalate prototype air pollution to direct code execution with server-side privileges.
The assault requires solely a single HTTP POST request to a Server Perform endpoint no authentication, no advanced exploit chains, no person interplay crucial.
Affected packages embrace react-server-dom-webpack, react-server-dom-parcel, and react-server-dom-turbopack in variations 19.0.0 via 19.2.0.
Critically, main frameworks constructed on React Server Elements are additionally impacted, together with Subsequent.js (variations 15.x and 16.x), React Router with RSC APIs, Expo, Redwood SDK, and Waku.
On condition that Subsequent.js is among the hottest React frameworks for manufacturing deployments, the vulnerability impacts a considerable portion of contemporary internet infrastructure.
The exploit timeline demonstrates the urgency of patching. Inside hours of disclosure, a number of researchers printed proof-of-concept code demonstrating dependable exploitation.
Assault demonstrations confirmed the vulnerability allows studying arbitrary recordsdata, establishing persistent reverse shells, and accessing surroundings variables containing database credentials and API keys.
MongoBleed Vulnerability (CVE-2025-14847)
MongoBleed arises from improper dealing with of size parameters in zlib-compressed MongoDB wire protocol messages, inflicting the server to return uninitialized heap reminiscence alongside legitimate responses. Attackers ship crafted, undersized compressed packets remotely with out authentication, triggering a buffer over-read that leaks adjoining reminiscence contents.
Leaked reminiscence typically incorporates high-value secrets and techniques like plaintext credentials, API keys, AWS tokens, and session knowledge from concurrent connections, enabling credential stuffing or lateral motion. Exploitation requires community entry and zlib compression enabled (default in lots of deployments), with public PoCs automating repeated probes for delicate fragments.
Found internally by MongoDB on December 12, 2025, patches rolled out quickly: Atlas fleet auto-updated by December 18, group/enterprise builds out there December 19. CISA added it to the KEV catalog on December 29, confirming wild exploitation towards ~87,000 uncovered cases, concentrated within the US, China, and Germany.
The ten vulnerabilities examined on this evaluation signify essentially the most crucial dangers dealing with enterprises, cloud infrastructure, cellular gadgets, and IoT programs in 2025.
These vulnerabilities share frequent traits: they permit unauthenticated distant code execution or privilege escalation, they have an effect on extensively deployed software program throughout a number of sectors, and they’re actively being exploited by subtle menace actors together with nation-state APT teams and ransomware operators.
The broader vulnerability panorama displays an alarming acceleration in assault sophistication and velocity. Over 21,500 CVEs have been disclosed in H1 2025 alone, with roughly 38% rated as Excessive or Crucial severity.
Extra critically, VulnCheck recognized 432 CVEs with proof of in-the-wild exploitation within the first half of 2025, with 32.1% exploited on or earlier than the disclosure date, indicating widespread zero-day weaponization.
These statistics reveal that vulnerability administration has basically modified: defenders can not merely defer patching to handy upkeep home windows, as attackers are weaponizing flaws inside hours of disclosure.
Nation-state menace actors proceed main the cost, focusing on enterprise safety infrastructure, authorities programs, and important infrastructure with subtle exploit chains.
The pivot towards focusing on enterprise safety merchandise (VPNs, firewalls, WAFs) displays a strategic shift the place attackers prioritize compromising the protecting infrastructure that guards company networks, enabling lateral motion at scale.
This pattern, alongside rising exploitation of AI/ML frameworks and rising applied sciences, means that organizations should increase vulnerability administration past conventional enterprise software program to incorporate rising applied sciences, infrastructure elements, and provide chain dependencies.
Speedy actions embrace prioritizing patches for all ten vulnerabilities examined right here, implementing compensating controls the place quick patching is just not possible, and establishing steady vulnerability intelligence packages that monitor CISA’s KEV Catalog and vendor advisories in actual time.
The 2025 vulnerability panorama validates that the normal reactive method to patching is now not viable. Organizations that haven’t shifted to proactive, steady vulnerability administration face existential danger from fast exploitation cycles.
Observe us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to characteristic your tales.