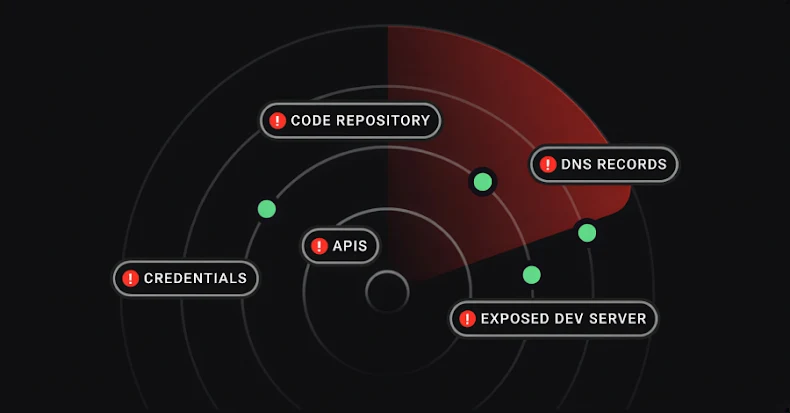
Assault Floor Administration (ASM) instruments promise decreased threat. What they often ship is extra info.
Safety groups deploy ASM, asset inventories develop, alerts begin flowing, and dashboards refill. There’s seen exercise and measurable output. However when management asks a easy query, “Is that this lowering incidents?” the reply is usually unclear.
This hole between effort and consequence is the core ROI downside in assault floor administration, particularly when ROI is measured primarily via asset counts as a substitute of threat discount.
The Promise vs. The Proof
Most ASM applications are constructed round an inexpensive thought: you may’t shield what you do not know exists. Because of this, groups give attention to discovery: domains and subdomains, IPs and cloud assets, third-party infrastructure, and transient or short-lived belongings.
Over time, counts enhance. Dashboards are trending upward. Protection improves.
However none of these metrics immediately reply whether or not the group is definitely safer. In lots of circumstances, groups find yourself busier with out feeling much less uncovered.
Why ASM Feels Busy however Not Efficient
ASM tends to optimize for protection as a result of protection is straightforward to measure: extra belongings found, extra adjustments detected, and extra alerts generated. Every of these looks like progress.
However they principally measure inputs, not outcomes.
In follow, groups expertise:
Alert fatigue
Lengthy backlogs of “identified however unresolved” belongings
Repeated possession confusion
Publicity that lingers for months
The work is actual. The chance discount is more durable to see.
The Measurement Hole
One purpose ASM ROI is tough to show is that almost all assault floor metrics give attention to what the system can see, not what the group really improves.
Widespread assault floor administration metrics embrace:
Variety of belongings
Variety of adjustments
Extra significant assault floor metrics are not often tracked:
How briskly dangerous belongings get owned
How lengthy harmful publicity persists
Whether or not assault paths really shrink over time
Asset stock stays foundational to measuring the exterior assault floor. With out broad discovery, it is unattainable to know publicity in any respect. The hole seems when discovery metrics aren’t paired with measurements that present whether or not threat is definitely being decreased.
With out outcome-oriented measurements, ASM turns into troublesome to defend throughout price range evaluations, even when everybody agrees that asset visibility is critical.
What Would Significant ROI Look Like?
As an alternative of asking, “What number of belongings did we uncover?” a extra helpful query is, “How a lot sooner and safer did we get at dealing with publicity?”
That reframing shifts ROI from visibility to response high quality and publicity length. Issues that correlate way more intently with real-world threat.
Three Final result Metrics That Really Matter
1. Imply Time to Asset Possession
How lengthy does it take to reply the essential query: “Who owns this?”
Belongings with out clear possession:
Linger longer
Get patched later
Usually tend to be forgotten fully
Lowering time-to-ownership shortens the window the place publicity exists with out accountability. It is one of many clearest indicators that ASM findings are turning into motion.
2. Discount in Unauthenticated, State-Altering Endpoints
Not all belongings matter equally.
Monitoring what number of exterior endpoints can change state, what number of require authentication, and the way these numbers change over time supplies a a lot stronger sign of whether or not the assault floor is shrinking the place it counts.
An surroundings with 1000’s of static belongings however few unauthenticated, state-changing paths is meaningfully safer than one with fewer belongings however many dangerous entry factors.
3. Time to Decommission After Possession Loss
Publicity typically persists after:
Staff adjustments
Utility deprecation
Vendor migrations
Reorgs
Measuring how shortly belongings are retired as soon as possession disappears is without doubt one of the strongest indicators of long-term hygiene and one of many least generally tracked.
If deserted belongings stick round indefinitely, discovery alone is not lowering threat.
What This Appears to be like Like in Follow
Summary metrics are straightforward to agree with and onerous to operationalize. The objective is not a brand new dashboard or a unique set of alerts, however a shift in what’s made seen: possession gaps, publicity length, and unresolved threat that might in any other case mix into asset counts.
Quite than emphasizing complete asset rely, this view surfaces:
Which belongings are owned
That are unresolved
How lengthy possession has been unclear
The objective is not extra alerts however sooner decision.
Turning ASM right into a Management
ASM would not battle as a result of groups aren’t working onerous sufficient. It struggles as a result of effort is not persistently tied to outcomes that management cares about.
Reframing ROI round velocity, possession, and publicity length makes it doable to indicate actual progress. Even when the uncooked asset rely by no means adjustments. In lots of circumstances, probably the most significant wins come from making the assault floor boring once more.
A Concrete Beginning Level
One approach to pressure-test outcome-based ASM metrics is to make asset visibility broadly accessible throughout groups, not gated behind tooling silos. We have discovered that when engineering, safety, and infrastructure groups can all see possession gaps and publicity length, decision hastens with out including extra alerts.
That pondering led us to launch a neighborhood version of our ASM platform that exposes asset discovery and possession visibility with out price or limits. The objective is not to switch present instruments, however to present groups a approach to measure whether or not publicity is definitely shrinking over time.
If you wish to pressure-test the ROI of your ASM program, do that: Ignore what number of belongings you could have.
As an alternative, ask:
How lengthy do dangerous belongings keep unowned?
What number of unauthenticated, state-changing paths exist immediately vs final quarter?
How shortly do deserted belongings disappear?
If these solutions aren’t bettering, extra discovery will not change the end result.
Conclusion: Measure What Really Adjustments Threat
Assault floor administration turns into defensible when it is measured by what adjustments, not simply what accumulates. Discovery will all the time matter. Visibility will all the time matter when measuring the assault floor. However neither ensures that publicity is being decreased, solely that it is being noticed.
Assault floor administration ROI exhibits up when dangerous belongings get confirmed as owned sooner, when harmful paths disappear sooner, and when deserted infrastructure would not linger indefinitely. Asset stock supplies the required breadth; outcome-oriented metrics present the depth wanted to know actual threat discount.
At Sprocket Safety, we attempt to consider assault floor administration not solely when it comes to what number of belongings exist, but additionally how lengthy significant publicity persists and the way shortly it will get resolved. What issues most is that assault floor metrics make progress seen, not simply stock development.
If an assault floor administration program cannot reply whether or not publicity is shrinking over time, it is onerous to argue that it is doing greater than reporting the issue.Observe: This text was expertly written and contributed by Topher Lyons, Options Engineer at Sprocket Safety.
Discovered this text fascinating? This text is a contributed piece from certainly one of our valued companions. Observe us on Google Information, Twitter and LinkedIn to learn extra unique content material we publish.