Jan 06, 2026Ravie LakshmananThreat Intelligence / Cloud Safety
Well-liked synthetic intelligence (AI)-powered Microsoft Visible Studio Code (VS Code) forks reminiscent of Cursor, Windsurf, Google Antigravity, and Trae have been discovered to advocate extensions which can be non-existent within the Open VSX registry, doubtlessly opening the door to produce chain dangers when unhealthy actors publish malicious packages underneath these names.
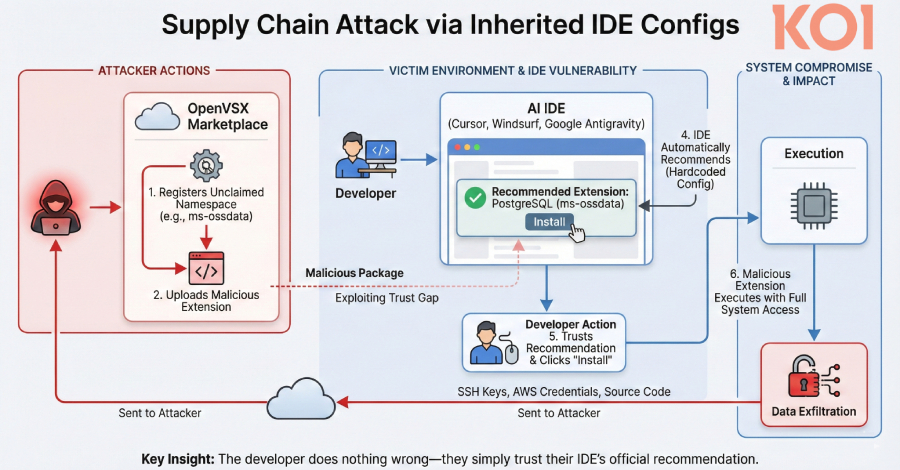
The issue, in response to Koi, is that these built-in growth environments (IDEs) inherit the record of formally really useful extensions from Microsoft’s extensions market. These extensions do not exist in Open VSX.
The VS Code extension suggestions can take two totally different kinds: file-based, that are displayed as toast notifications when customers open a file in particular codecs, or software-based, that are advised when sure packages are already put in on the host.
“The issue: these really useful extensions did not exist on Open VSX,” Koi safety researcher Oren Yomtov stated. “The namespaces had been unclaimed. Anybody may register them and add no matter they needed.”
In different phrases, an attacker may weaponize the absence of those VS Code extensions and the truth that the AI-powered IDEs are VS Code forks to add a malicious extension to the Open VSX registry, reminiscent of ms-ossdata.vscode-postgresql.
In consequence, any time a developer with PostgreSQL put in opens one of many aforementioned IDEs and sees the message “Advisable: PostgreSQL extension,” a trivial set up motion is sufficient to outcome within the deployment of the rogue extension on their system as an alternative.
This straightforward act of belief can have extreme penalties, doubtlessly resulting in the theft of delicate information, together with credentials, secrets and techniques, and supply code. Koi stated its placeholder PostgreSQL extension attracted at least 500 installs, indicating that builders are downloading it just because the IDE advised it as a advice.
The names of a number of the extensions which were claimed by Koi with a placeholder are listed under –
ms-ossdata.vscode-postgresql
ms-azure-devops.azure-pipelines
msazurermtools.azurerm-vscode-tools
usqlextpublisher.usql-vscode-ext
cake-build.cake-vscode
pkosta2005.heroku-command
In response to accountable disclosure, Cursor, Windsurf, and Google have rolled out fixes to deal with the problem. The Eclipse Basis, which oversees Open VSX, has since eliminated non-official contributors and enforced broader registry-level safeguards.
With risk actors more and more specializing in exploiting the safety gaps in extension marketplaces and open-source repositories, it is important that builders train warning previous to downloading any packages or approving installs by verifying they arrive from a trusted writer.