As we head into 2026, the cybersecurity panorama is evolving in ways in which really favor the defenders.
The menace traits we’re seeing aren’t simply challenges. They’re catalysts pushing SOCs to grow to be smarter, extra environment friendly, and extra aligned with enterprise targets than ever earlier than.
Ahead-thinking leaders are already embracing superior menace intelligence to show potential complications into strategic benefits.
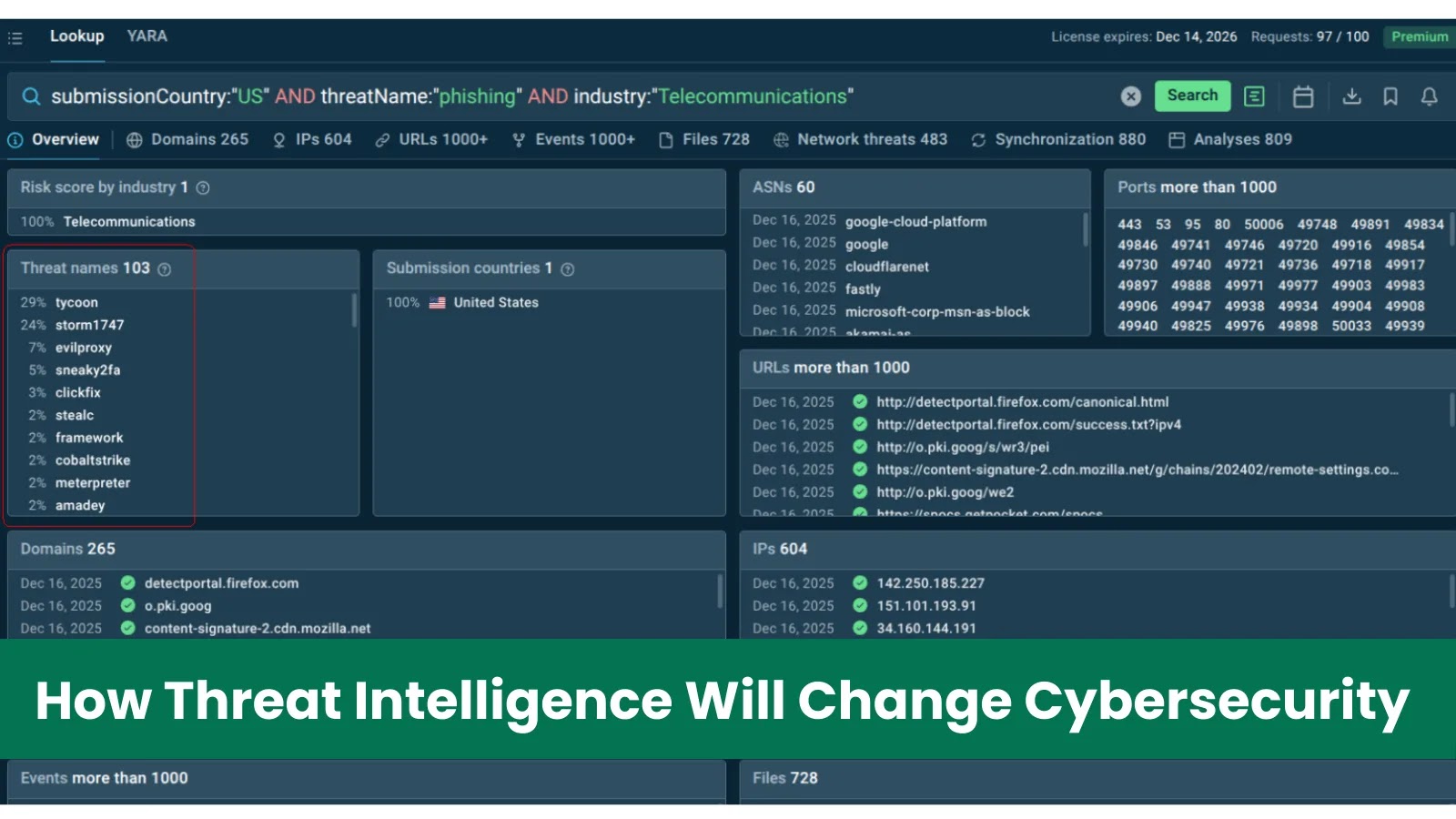
Options like ANY.RUN’s Risk Intelligence Feeds, powered by real-time sandbox evaluation of dwell malware and neighborhood insights from hundreds of organizations, are main the cost.
They ship high-fidelity indicators of compromise, wealthy context, and seamless integrations that assist SOCs keep forward with out breaking a sweat.
Listed here are 5 methods menace intelligence will empower your SOC to thrive in 2026, specializing in effectivity and enterprise worth.
Safeguarding Income with Proactive Early Detection
In 2026, AI-driven threats will make breaches quicker and stealthier. However think about catching them earlier than they even knock on the door.
Excessive-quality menace intelligence shifts SOCs from late-stage response to brisk prevention, slashing incident impacts and conserving income flowing easily. ANY.RUN’s TI Feeds present contemporary, verified IOCs straight from interactive sandbox periods, answering questions like “What’s actively focusing on friends in our trade proper now?”
This implies faster enrichment, decrease breach dangers, and large financial savings, usually stopping thousands and thousands in downtime, fines, and misplaced belief.
TI Feeds: advantages and knowledge sources
The outcome? Your SOC turns into a income protector, delivering peace of thoughts and proving cybersecurity’s direct contribution to the underside line.
Cut back enterprise dangers with actionable menace intel => Combine ANY.RUN’s TI options in your SOC.
Maintaining Operations Operating Easily Amid Disruptive Campaigns
Ransomware and disruption ways are getting smarter in 2026, with attackers eyeing crucial methods for optimum impression.
However with menace intelligence, SOCs can anticipate these strikes and put together effortlessly, minimizing downtime that would value hundreds per minute in industries like e-commerce, finance, or manufacturing.
Powered by world neighborhood submissions, ANY.RUN’s feeds highlight rising campaigns early, shortening detection and response instances whereas serving to correlate alerts with confidence.
This alignment ensures that enterprise continuity turns into a power, letting your group give attention to innovation relatively than restoration.
Risk intelligence helps fast knowledgeable choices impacting KPIs
2026 will demand that each safety funding, from firewalls to EDR and SIEM, carry out at peak effectivity in opposition to real-world dangers. Risk intelligence is the catalyst that transforms your current safety stack from reactive to predictive.
Once you feed present, verified menace knowledge into your SIEM, IDS/IPS, and EDR methods, they cease producing generic alerts and begin catching actual threats early within the assault chain.
ANY.RUN’s Risk Intelligence Feeds combine seamlessly with main safety platforms by way of APIs and customary codecs like STIX.
Your current instruments instantly acquire entry to thousands and thousands of present indicators with out requiring infrastructure modifications or extra licensing complexity.
ANY.RUN integration choices
Turning Alerts into Outcomes
One of many greatest effectivity drains for contemporary SOCs is the deluge of alerts. Analysts could be buried beneath knowledge that lacks actionable context, slowing incident response and elevating burnout.
Fashionable menace intelligence modifications this by enriching alerts with context, linking them to actual adversary conduct, and filtering out the noise.
ANY.RUN’s TI Feeds embody contextual metadata that helps SOC platforms and analysts differentiate between low-priority noise and high-impact threats, boosting detection high quality and lowering investigation drag. Risk Intelligence Lookup is one other decision-enabling service from ANY.RUN.
It’s an on-demand searchable database that gives on the spot entry to detailed menace studies, behavioral insights, direct hyperlinks to sandbox periods, and contextual connections between IOCs and lively campaigns, enabling fast enrichment throughout investigations.
As a substitute of asking “What might occur?”, safety leaders can reply “What’s actively focusing on organizations like ours proper now?”
See what malware is threatening the organizations out of your nation and trade proper now
These providers assist to scale your group’s capability by 50-70% with out including headcount. Say goodbye to burnout and hiya to a motivated, high-performing SOC.
This shift frees your specialists for strategic work, aligning safety efforts with broader enterprise targets like agility and progress.
The Regulatory Bonus: Demonstrating Due Diligence
As we transfer by way of 2026, regulatory frameworks like NIS2, DORA, and evolving GDPR interpretations are more and more anticipating organizations to show proactive menace consciousness.
Merely having safety controls isn’t sufficient—it’s worthwhile to present you’re actively monitoring the menace panorama related to your online business.
Risk intelligence feeds present precisely this: auditable proof of steady monitoring, documented responses to rising threats, and clear processes for staying forward of evolving assault patterns.
When auditors ask “how do you keep present on threats?”, you’ve a complete reply backed by concrete knowledge. This isn’t simply compliance box-checking.
It’s demonstrating real safety maturity in a means that builds stakeholder confidence and positions your group effectively for partnerships, buyer relationships, and regulatory critiques.
Maybe the most vital shift in 2026 is how menace intelligence is lastly bridging the hole between safety operations and enterprise management.
For too lengthy, SOC metrics like “alerts processed” or “vulnerabilities patched” felt disconnected from what executives really care about: income safety, operational continuity, and danger discount.
Risk intelligence modifications this dialog as a result of it connects technical safety work on to enterprise impression. When your SOC can say “we prevented this ransomware marketing campaign that shut down three opponents final week,” management understands the worth instantly.
The menace traits of 2026 make this much more related. With common ransomware downtime hovering round 25 days and assaults more and more focusing on revenue-critical methods, the enterprise case for proactive menace intelligence is apparent.
Risk intelligence anchors safety in tangible enterprise outcomes by:
Preserving income by detecting threats earlier than they breach crucial methods;
Decreasing operational friction by chopping down unnecessary alerts and investigations;
Enhancing danger visibility so management could make assured, data-backed choices
With ANY.RUN’s TI Feeds built-in throughout the safety stack, organizations can measure and show the enterprise impression of safety operations: quicker time-to-detection, lowered incident impression, and stronger alignment with enterprise danger tolerance.
Construct a extra environment friendly, efficient SOC. Get actionable menace intelligence from actual assaults. Request TI Feeds trial.