Safety researcher TwoSevenOneT, recognized for EDR evasion instruments like EDR-Freeze and EDR-Redir, unveiled EDRStartupHinder this week.
The instrument blocks antivirus and EDR providers at startup by redirecting vital System32 DLLs by way of Home windows Bindlink, demonstrated on Home windows Defender in Home windows 11 25H2.
Antivirus and EDR providers function like commonplace Home windows providers however with enhanced safety from kernel drivers.
They run below SYSTEM privileges, auto-start on boot, and use Protected Course of Gentle (PPL) to forestall user-mode tampering. Configuration adjustments in consumer mode fail, and processes resist modification with out superior methods equivalent to EDR-Freeze.
Bindlink Startup Disruption
Earlier methods, like EDR-Redir, redirected EDR folders post-startup, however distributors hardened towards them. EDRStartupHinder preempts this by focusing on System32, which is important for all processes, together with EDRs.
EDRStartupHinder Instrument
Steps embody making a higher-priority service, Bindlinking a core DLL to an unsigned “corrupted” copy, leveraging PPL to crash the EDR on load failure, and cleansing up post-termination.
Service precedence attracts from BYOVD analysis, checking HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlServiceGroupOrder. The DLL should keep away from the KnownDLLs preload record, identifiable by way of Course of Monitor.
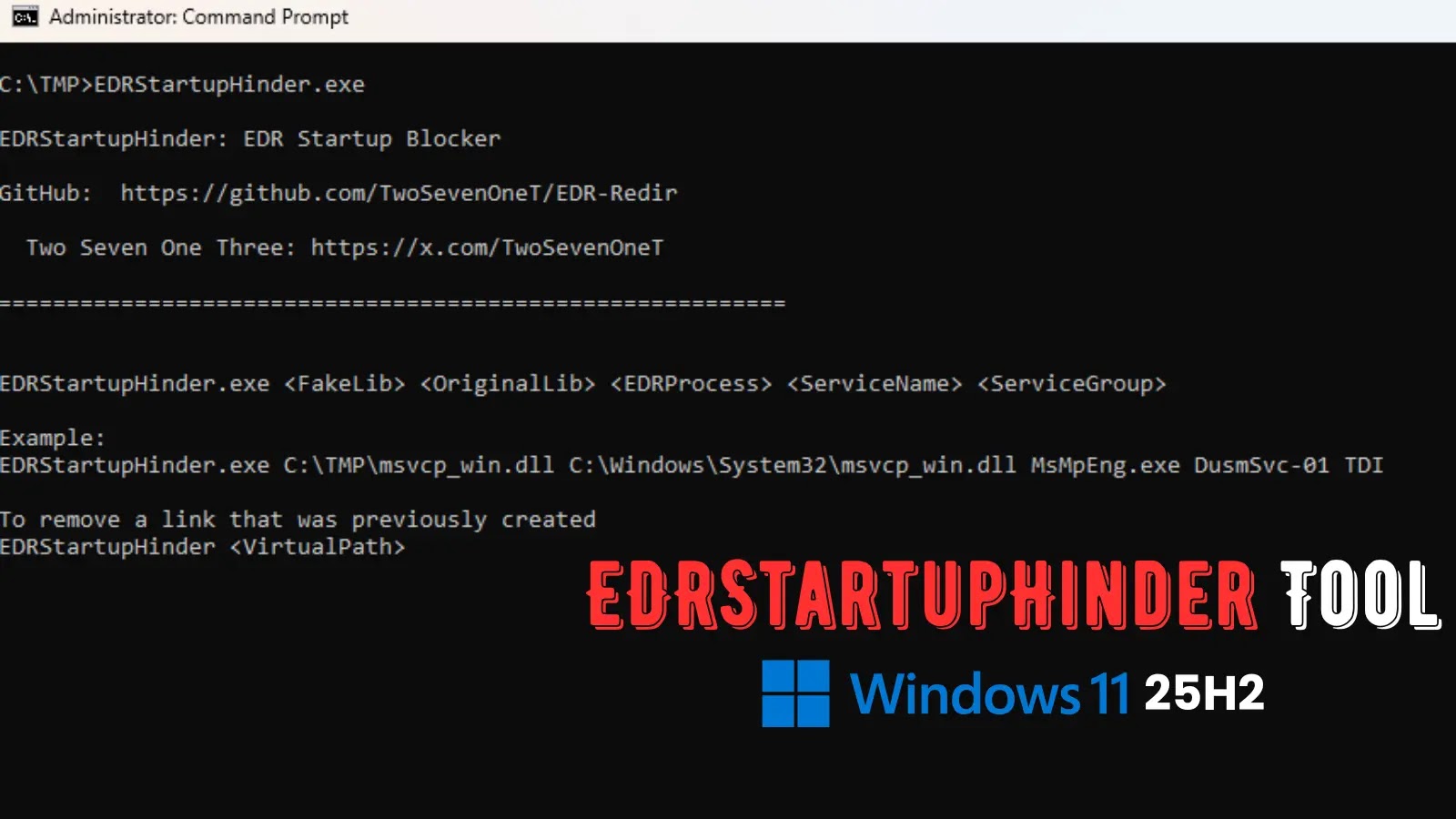
Accessible on GitHub, EDRStartupHinder takes parameters: OriginalLib (System32 DLL), FakeLib (copy location), ServiceName/Group (precedence), EDRProcess (goal like MsMpEng.exe).
It corrupts the PE header signature on FakeLib, registers as service, displays for EDR launch, applies/removes Bindlink dynamically. Customers should analysis EDR-specific DLLs and teams utilizing Course of Explorer boot logs.
On a lab Home windows 11 25H2 system, focusing on MsMpEng.exe (Defender engine) and msvcp_win.dll (loaded at startup), with TDI service group precedence. Command: EDRStartupHinder.exe msvcp_win.dll C:TMPFakeLib DusmSVC-01 TDI MsMpEng.exe.
EDRStartupHinder startup
Put up-reboot, the service prompts first, redirects DLL; PPL-protected MsMpEng rejects the unsigned DLL and self-terminates.
Sysadmins ought to monitor bindlink.dll utilization, suspicious providers in high-priority teams, and System32 anomalies. Protection-in-depth contains KnownDLL expansions, signature enforcement audits, and minifilter logging. Distributors should harden DLL dependencies and startup sequencing.
This method underscores Home windows mechanisms as double-edged swords for purple groups, efficient towards Defender and unnamed industrial EDRs/AVs in labs.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to characteristic your tales.