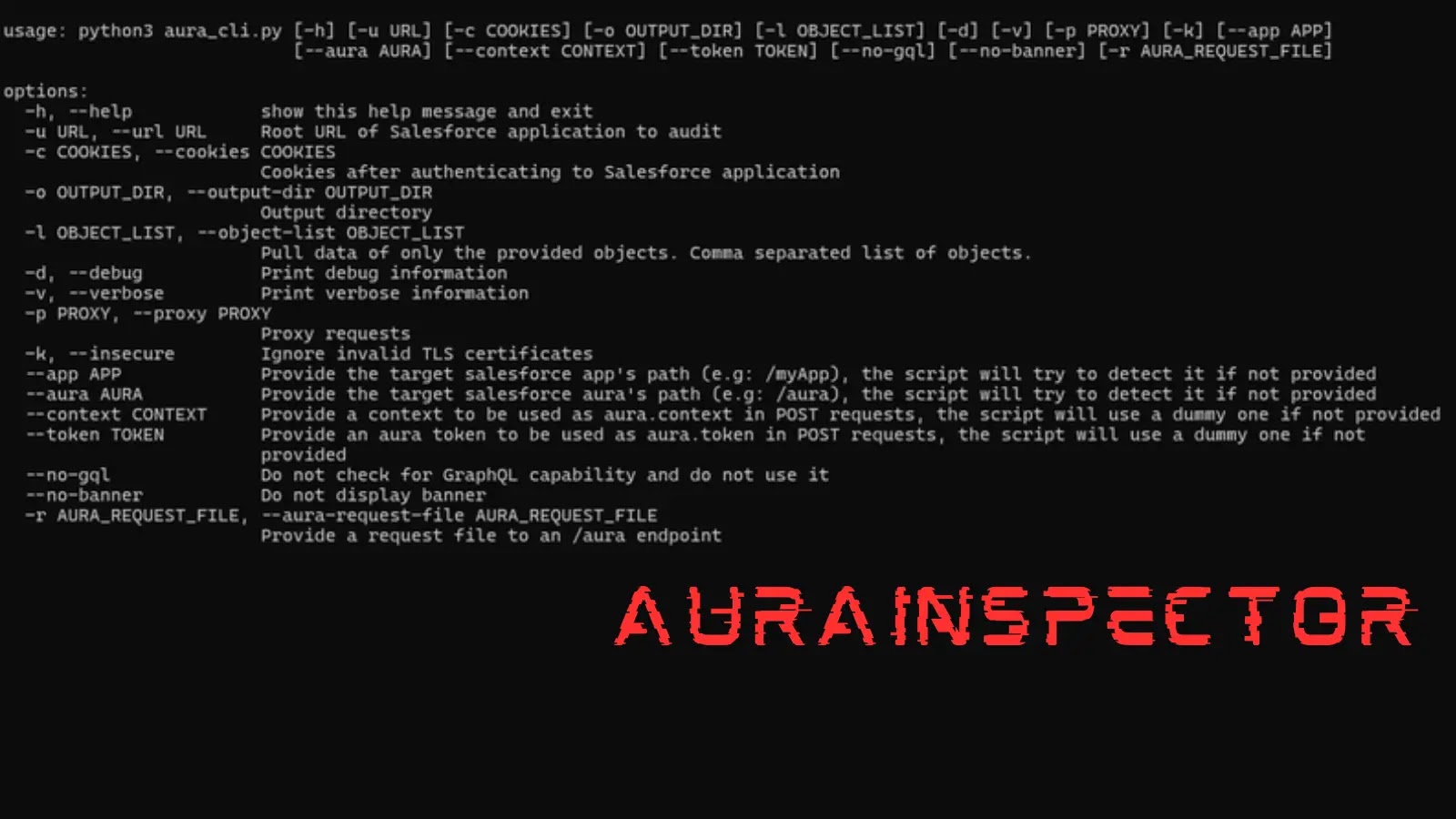
Mandiant has launched AuraInspector, an open-source command-line software that helps safety defenders establish and audit access-control misconfigurations within the Salesforce Aura framework.
The software addresses a crucial safety hole in Salesforce Expertise Cloud deployments, the place misconfigurations incessantly expose delicate information, together with bank card numbers, id paperwork, and well being data.
The Aura endpoint, a basic element of Salesforce’s Lightning Expertise interface, is without doubt one of the mostly focused assault surfaces in Expertise Cloud purposes.
Salesforce’s object sharing guidelines span a number of configuration ranges, making it difficult for directors to establish potential access-control misconfigurations from an exterior perspective.
AuraInspector automates the detection of those exposures and gives actionable remediation insights.
The software leverages a number of assault methods beforehand documented by Mandiant’s Offensive Safety Companies workforce.
FeatureDescriptionAutomatic Aura DetectionFinds the Aura endpoint automaticallyObject Entry ScanChecks which objects and information are accessibleRecord Listing DiscoveryFinds uncovered file lists and their URLsSelf-Registration CheckChecks if self-signup is enabled and will get signup linksURL DiscoveryFinds house and admin URLs automaticallyGraphQL BypassUses a GraphQL methodology to fetch greater than 2,000 recordsAction BulkingSends a number of actions in a single requestRead-Solely ModeOnly reads information, makes no changesCommand-Line ToolSimple CLI for scanning and reportsOpen SourceAvailable on GitHub
It identifies accessible objects through Aura strategies resembling getItems and getConfigData, which might expose delicate information when entry controls are improperly configured.
AuraInspector additionally checks for uncovered File Lists, that are Salesforce parts that present direct entry to object information when permissions are misconfigured.
A major function is the software’s potential to detect enabled self-registration endpoints.
Mandiant noticed situations during which self-registration hyperlinks have been faraway from login pages. But, the performance remained enabled, permitting unauthorized account creation.
Breakthrough: GraphQL Integration
AuraInspector introduces a beforehand undocumented approach utilizing Salesforce’s GraphQL Aura controller to bypass the usual 2,000-record retrieval restrict.
utilizing the GraphQL Aura Controller
This enables a complete evaluation of misconfiguration impression with out guide sorting workarounds.
The software automates the development of GraphQL queries to retrieve full datasets when entry controls fail.
The software routinely discovers crucial contextual data, together with Aura endpoints, house and file checklist URLs, self-registration standing, and accessible administration panels.
It performs strictly read-only operations, guaranteeing examined situations stay unmodified. Mandiant recommends directors audit visitor person permissions utilizing the precept of least privilege.
Assist message of the AuraInspector software
Evaluate sharing guidelines and organization-wide defaults, flip off pointless self-registration, and implement Salesforce safety greatest practices.
The Safety Well being Verify software and the excellent Salesforce Safety Information present extra steering for hardening.
AuraInspector is accessible now on GitHub, enabling safety groups to establish and remediate Aura-related exposures earlier than adversaries exploit them proactively.
Comply with us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.