Ravie LakshmananJan 20, 2026Malware / Risk Intelligence
Cybersecurity researchers have uncovered a brand new phishing marketing campaign that exploits social media personal messages to propagate malicious payloads, seemingly with the intent to deploy a distant entry trojan (RAT).
The exercise delivers “weaponized recordsdata through Dynamic Hyperlink Library (DLL) sideloading, mixed with a reliable, open-source Python pen-testing script,” ReliaQuest mentioned in a report shared with The Hacker Information.
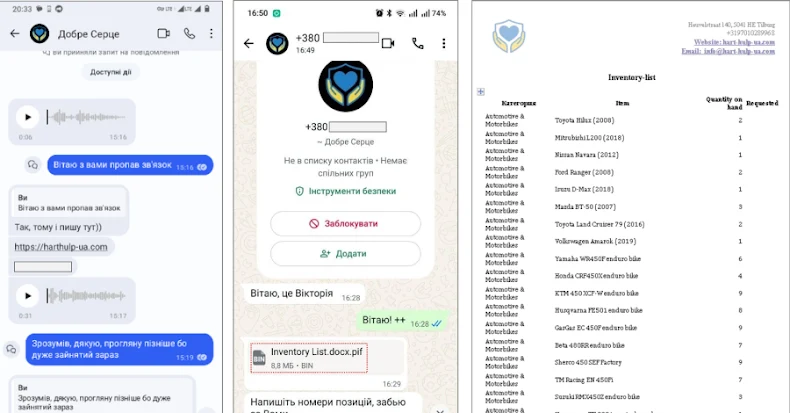
The assault entails approaching high-value people by way of messages despatched on LinkedIn, establishing belief, and deceiving them into downloading a malicious WinRAR self-extracting archive (SFX). As soon as launched, the archive extracts 4 completely different parts –
A reliable open-source PDF reader software
A malicious DLL that is sideloaded by the PDF reader
A conveyable executable (PE) of the Python interpreter
A RAR file that seemingly serves as a decoy
The an infection chain will get activated when the PDF reader software is run, inflicting the rogue DLL to be sideloaded. Using DLL side-loading has turn into an more and more widespread approach adopted by risk actors to evade detection and conceal indicators of malicious exercise by profiting from reliable processes.
Over the previous week, at the very least three documented campaigns have leveraged DLL side-loading to ship malware households tracked as LOTUSLITE and PDFSIDER, together with different commodity trojans and data stealers.
Within the marketing campaign noticed by ReliaQuest, the sideloaded DLL is used to drop the Python interpreter onto the system and create a Home windows Registry Run key that makes certain that the Python interpreter is mechanically executed upon each login. The interpreter’s major duty is to execute a Base64-encoded open-source shellcode that is instantly executed in reminiscence to keep away from leaving forensic artifacts on disk.
The ultimate payload makes an attempt to speak with an exterior server, granting the attackers persistent distant entry to the compromised host and exfiltrating knowledge of curiosity.
The abuse of reliable open-source instruments, coupled with the usage of phishing messages despatched on social media platforms, exhibits that phishing assaults aren’t confined to emails alone and that various supply strategies can exploit safety gaps to extend the chances of success and break into company environments.
ReliaQuest instructed The Hacker Information that the marketing campaign seems to be broad and opportunistic, with exercise spanning varied sectors and areas. “That mentioned, as a result of this exercise performs out in direct messages, and social media platforms are sometimes much less monitored than electronic mail, it is tough to quantify the total scale,” it added.
“This method permits attackers to bypass detection and scale their operations with minimal effort whereas sustaining persistent management over compromised techniques,” the cybersecurity firm mentioned. “As soon as inside, they will escalate privileges, transfer laterally throughout networks, and exfiltrate knowledge.”
This isn’t the primary time LinkedIn has been misused for focused assaults. In recent times, a number of North Korean risk actors, together with these linked to the CryptoCore and Contagious Interview campaigns, have singled out victims by contacting them on LinkedIn underneath the pretext of a job alternative and convincing them to run a malicious mission as a part of a supposed evaluation or code evaluation.
In March 2025, Cofense additionally detailed a LinkedIn-themed phishing marketing campaign that employs lures associated to LinkedIn InMail notifications to get recipients to click on on a “Learn Extra” or “Reply To” button and obtain the distant desktop software program developed by ConnectWise for gaining full management over sufferer hosts.
“Social media platforms generally utilized by companies symbolize a niche in most organizations’ safety posture,” ReliaQuest mentioned. “Not like electronic mail, the place organizations are inclined to have safety monitoring instruments, social media personal messages lack visibility and safety controls, making them a lovely supply channel for phishing campaigns.”
“Organizations should acknowledge social media as a vital assault floor for preliminary entry and prolong their defenses past email-centric controls.”