As cyber danger more and more interprets into monetary loss, velocity is all the things. But most Safety Operations Facilities (SOCs) are detecting assaults solely after vital injury has already occurred.
The common information breach prices organizations $4.4 million, with prices escalating the longer attackers stay undetected inside networks.
Delayed detection, usually measured in days or even weeks of dwell time, turns preventable incidents into costly crises.
Why SOCs Lag Behind Trendy Assaults
The foundation trigger? Outdated or incomplete menace intelligence. Public experiences ceaselessly arrive too late, after attackers have pivoted to new infrastructure.
Many business feeds ship indicators with out significant context, forcing analysts to conduct time-consuming guide verification.
This results in alert overload (SOCs resist 11,000 alerts per day, with solely 19% deemed actionable), skyrocketing false positives, analyst burnout, and, critically, missed threats.
With out contemporary, contextual menace information, SOCs waste valuable assets chasing noise whereas actual assaults go unnoticed.
The end result: decrease detection charges, extended imply time to detect (MTTD) and remediate (MTTR), and pointless monetary losses.
The Rotten Roots of Late Detection
Contemplate the each day actuality for most SOC groups:
Low Detection Charges and Blind Spots: Evasion methods enable malware and phishing campaigns to bypass conventional defenses, leaving SOCs reactive fairly than proactive.
Causes and outcomes of low menace detection
Alert Fatigue: Excessive volumes of unprioritized alerts lead to backlogs and escalations, with false positives draining analyst productiveness.
Gradual ResponseTimes: Lack of speedy context round indicators means hours spent on analysis. That’s the time attackers use to transfer laterally.
Useful resource Drain: Overworked groups, rising burnout, and inefficient workflows improve operational prices whereas breach dangers compound.
These challenges aren’t summary. Organizations counting on delayed intelligence see larger publicity, extra profitable assaults, and diminished return on their safety investments.
Why Recent Menace Intel Issues
The repair lies in adopting real-time menace intelligence feeds that ship verified, contextual indicators the second rising threats are recognized.
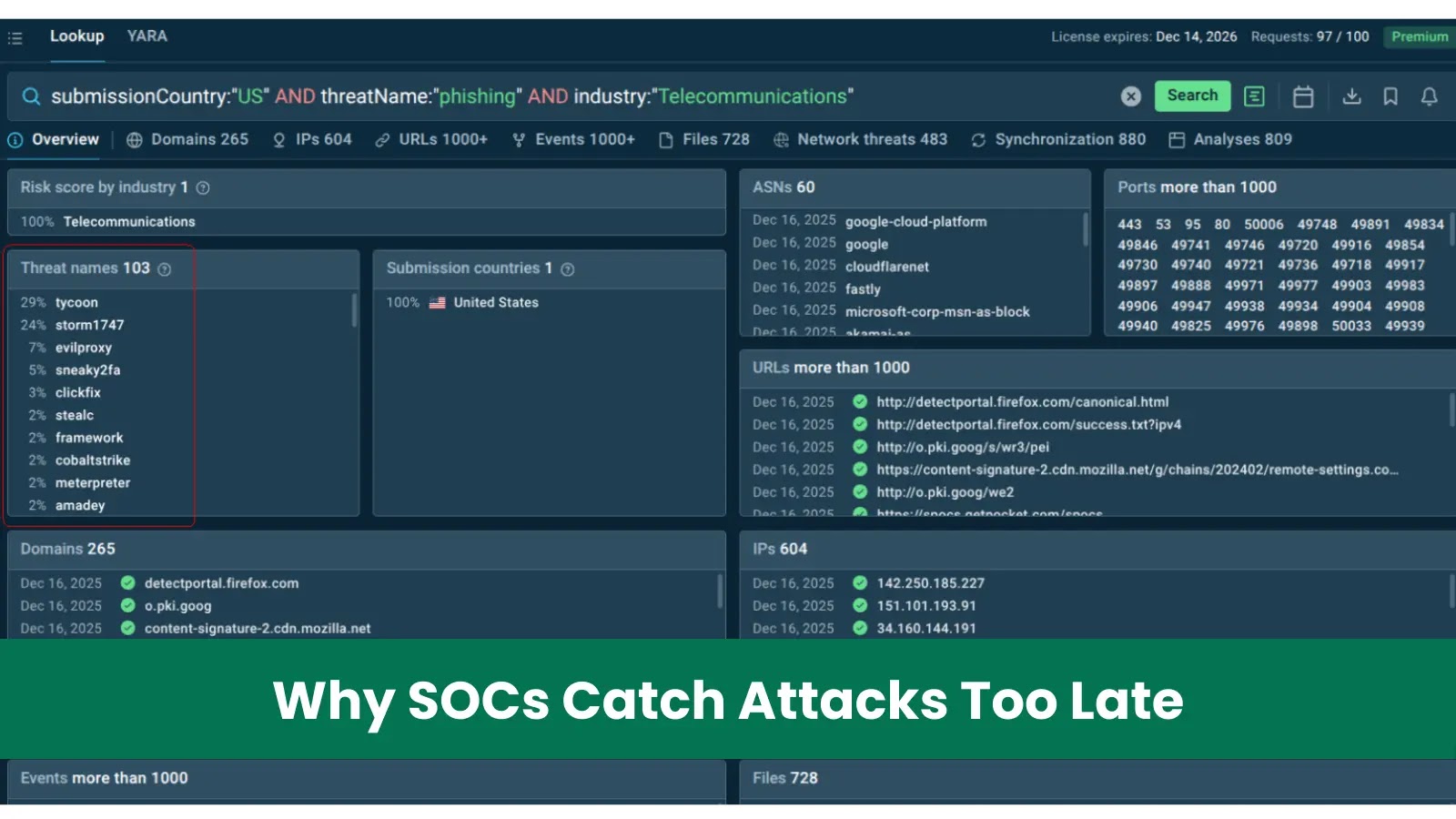
ANY.RUN’s Menace Intelligence Feeds carry present, verified indicators instantly into safety stacks like SIEMs, XDR, EDR, and SOAR. Right here’s what this permits:
1. Early Detection of Rising Assaults
Recent menace intel feeds ship up-to-the-minute IOCs — together with malicious IPs, domains, URLs — sourced from lively assaults and sandbox investigations. This helps SOCs detect threats earlier than they escalate.
ANY.RUN’s Menace Intelligence Feeds draw their information from stay sandbox classes and group contributions from over 15,000 organizations, including 16,000+ new threats each day to their database
Reasonably than ready for weeks or months for signatures, fashionable SOCs profit from practically real-time updates, narrowing the window between menace emergence and detection.
2. Discount in False Positives and Noise
Excessive-quality feeds filter out false positives earlier than reaching analysts. By enriching IOCs with sandbox-verified contextual information, feeds assist SOC groups deal with actual dangers, not guesswork.
This reduces wasted labor, which is a big price driver, as alert triage and false positives can account for hundreds of thousands in labor bills yearly.
3. Quicker Triage and Determination-Making
When a suspicious alert arrives, SOC analysts armed with prime intelligence can validate an IOC immediately and perceive its context: who used it, the way it behaves, and what it’s focusing on.
This dramatically shortens Imply Time to Detect (MTTD) and Imply Time to Reply (MTTR), decreasing publicity and operational influence.
4. Proactive: Keep Forward, Don’t Chase
With real-time feeds built-in into detection techniques, SOCs can shift from reactive protection to proactive menace looking.
Analysts can leverage rising indicators to go looking historic logs for early indicators of intrusion, uncovering tried assaults that may have slipped previous preliminary controls.
Make quicker safety selections with more energizing information. ANY.RUN TI Feeds enhance detection velocity and operational effectivity.
How ANY.RUN Intelligence Adjustments the Sport
ANY.RUN’s Menace Intelligence Feeds symbolize a shift from static to dynamic cybersecurity insights:
Excessive-Constancy, Filtered IOCs: Pre-processed for low false positives and excessive relevance.
Actual-Time Updates: Recent indicators from numerous menace analyses day-after-day.
Contextual Metadata & Sandbox Hyperlinks: Every IOC is tied to detailed sandbox investigation information, serving to analysts rapidly perceive assault ways, methods, and indicators.
Simple Integration: Suitable with SIEM, SOAR, TIP, and different enterprise techniques by way of STIX, TAXII, MISP, API, or SDK.
The end result? Extra assured, quicker, and extra correct menace detection that instantly ties safety operations to enterprise outcomes.
ANY.RUN Feeds: advantages and information sources
Knowledge Is aware of, Knowledge Reveals
Organizations utilizing ANY.RUN’s Feeds report transformative outcomes:
As much as 58% improve in threats detected;
94% quicker alert triage;
21 minutes saved per incident on MTTR;
3x general enchancment in SOC efficiency;
Important reductions in false positives and Tier 1 workload (as much as 20%).
By integrating these feeds, SOCs acquire the boldness to dam threats immediately, prioritize actual incidents, and allocate assets effectively, instantly translating to decrease breach danger and substantial price financial savings.
Integrating TI Feeds with Microsoft Sentinel
Conclusion: Making the Shift
The transition from conventional, reactive safety operations to proactive menace detection doesn’t require wholesale infrastructure substitute. It requires higher information feeding into the techniques you have already got.
ANY.RUN Menace Intelligence Feeds present that higher information.
By incorporating intelligence from the newest assaults analyzed by a worldwide group of specialists, your safety infrastructure features the flexibility to detect rising threats early, when containment continues to be attainable and injury may be minimized.
For decision-makers evaluating safety investments, menace intelligence feeds symbolize one of many highest ROI alternatives out there.
The price of a top quality feed is a small fraction of the price of a single prolonged breach, and the operational advantages — lowered false positives, quicker detection, extra assured decision-making — compound over time.
Reduce noise. Reduce losses. Combine high-fidelity TI Feeds to focus SOC on actual threats and shield enterprise outcomes.