Phishing was simple to identify. Dangerous grammar, unusual hyperlinks, apparent scams. That model is gone.
In 2026, phishing is polished, well-written, and infrequently smarter than it has any proper to be thanks to AI.
These assaults appear like actual enterprise emails, slip previous conventional safety instruments, and land straight in entrance of staff who don’t have any cause to be suspicious.
At this level, attempting to identify phishing by appears to be like alone is a shedding recreation.
Main firms have discovered a greater method; one which reveals the actual menace earlier than it reaches the enterprise.
Right here’s how one can cease it too and obtain as much as a 3× enhance in group effectivity.
Static detection instruments have been designed for predictable threats. AI-driven phishing is neither predictable nor static, which is why it so typically slips by means of.
They fail as a result of:
Content material continually modifications, breaking signatures and status checks
Malicious habits is hidden behind redirects that seem solely in actual browsers
Last phishing pages load dynamically, typically after timing or location checks
Visible and structural checks look clear till consumer interplay happens
That is why phishing that appears innocent on the floor can nonetheless trigger severe enterprise influence.
Resolution Discovered: Full AI Phishing Visibility in Underneath a Minute
Main firms aren’t attempting to “out-detect” AI phishing with extra guidelines or stricter filters.
As a substitute, they’ve shifted how phishing is investigated altogether, combining interactivity and automation to reveal assaults precisely as they behave in the actual world.
This mix is delivered by fashionable sandboxes reminiscent of ANY.RUN, which permit safety groups to observe the total phishing chain mechanically, in actual time, and at scale, typically in below 60 seconds.
See Current Enterprise-Focused Assault Totally Uncovered
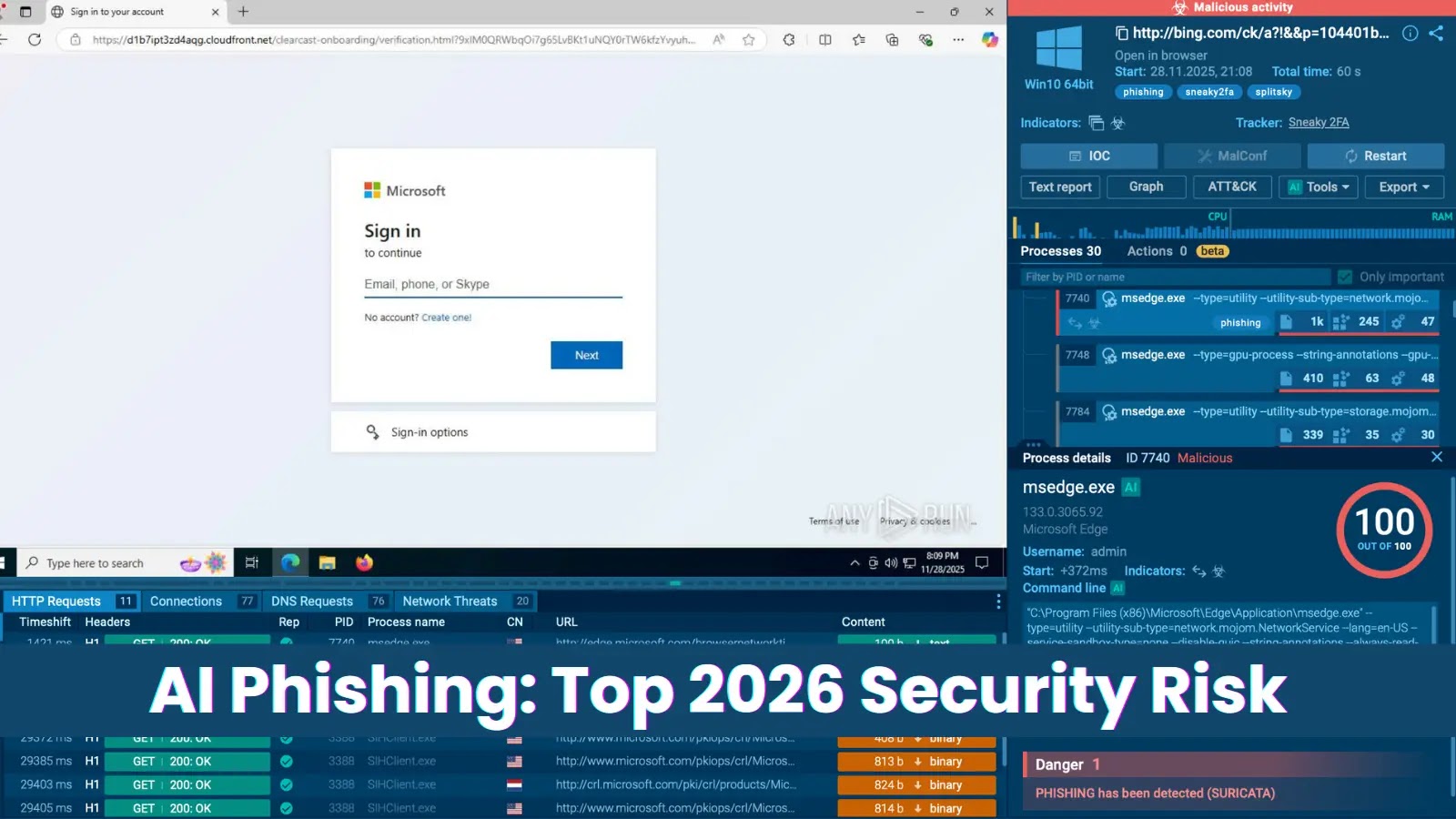
Faux Microsoft 365 login web page uncovered in 60 seconds inside ANY.RUN sandbox
In a current assault, phishing was aimed at firm customers, filtering out free electronic mail domains. The entry level regarded routine, a LinkedIn Drive file hyperlink, and the phishing content material was hosted on AWS CloudFront, a trusted cloud service.
Conventional instruments flagged nothing. As soon as executed within the ANY.RUN sandbox, nonetheless, the total phishing chain was uncovered in below 60 seconds, revealing a pretend Microsoft 365 login web page constructed to steal company credentials.
For organizations dealing with larger phishing quantity and smarter assaults in 2026, this velocity instantly reduces enterprise danger, limits publicity, and offers safety groups the readability they should act earlier than harm is completed.
Uncover how briskly, evidence-driven phishing evaluation can ship 3× quicker triage and 30% fewer escalations on your group. Discuss to ANY.RUN Specialists
Why This Method Works In opposition to Trendy AI Phishing
As a result of it delivers the visibility, velocity, and intelligence wanted to uncover assaults designed to look authentic.
Sooner choices with fewer blind spots: Analysts can safely work together with suspicious hyperlinks and recordsdata contained in the sandbox, clicking by means of pages, triggering redirects, and uncovering hidden logic, with out risking publicity to the actual surroundings.
This reveals habits static instruments by no means see and hastens decision-making.
Clear, closing verdicts in seconds: The sandbox handles the tedious, time-consuming steps analysts usually do manually, fixing CAPTCHAs, navigating multi-step flows, opening hidden hyperlinks, even extracting URLs buried in QR codes.
This turns complicated phishing chains right into a single, dependable verdict, giving Tier 1 analysts extra confidence and releasing senior employees from repetitive work.
Greater group productiveness with out additional hiring: Automation in ANY.RUN detonates hyperlinks, captures habits, and extracts IOCs immediately, turning hours of guide checks into seconds.
Related IOCs gathered in a single tab for comfort inside ANY.RUN sandbox
Smarter investigations powered by international intelligence: Entry to behavioral knowledge from 15,000+ organizations helps groups examine assaults, discover overlaps in infrastructure, and uncover campaigns that reuse the identical patterns.
Stronger, evidence-based choices: Full context, habits timelines, IOC maps, community calls, and attacker infrastructure, offers leaders the proof they should comprise threats early.
Equip Your Workforce with Sooner, Clearer Phishing Protection
AI phishing is tough to detect however with the fitting answer, it turns into quicker to analyze, simpler to confirm, and way more manageable on your group.
Organizations implementing behavior-based sandboxing, reminiscent of ANY.RUN are already seeing measurable enhancements:
MTTR lowered by as much as 21 minutes per case
As much as 20% lower in Tier 1 workload
30% fewer Tier 1 → Tier 2 escalations
94% of customers report quicker triage and clearer choices
The outcomes communicate for themselves: quicker solutions, much less stress on analysts, and clearer choices at each step.
Discuss to ANY.RUN group – See how this method can instantly strengthen your SOC workflow.