A vital safety alert relating to an lively phishing marketing campaign that commenced on January 19, 2026. The malicious actors are impersonating LastPass help employees and sending fraudulent emails claiming pressing vault backup necessities to reap grasp passwords from unsuspecting customers.
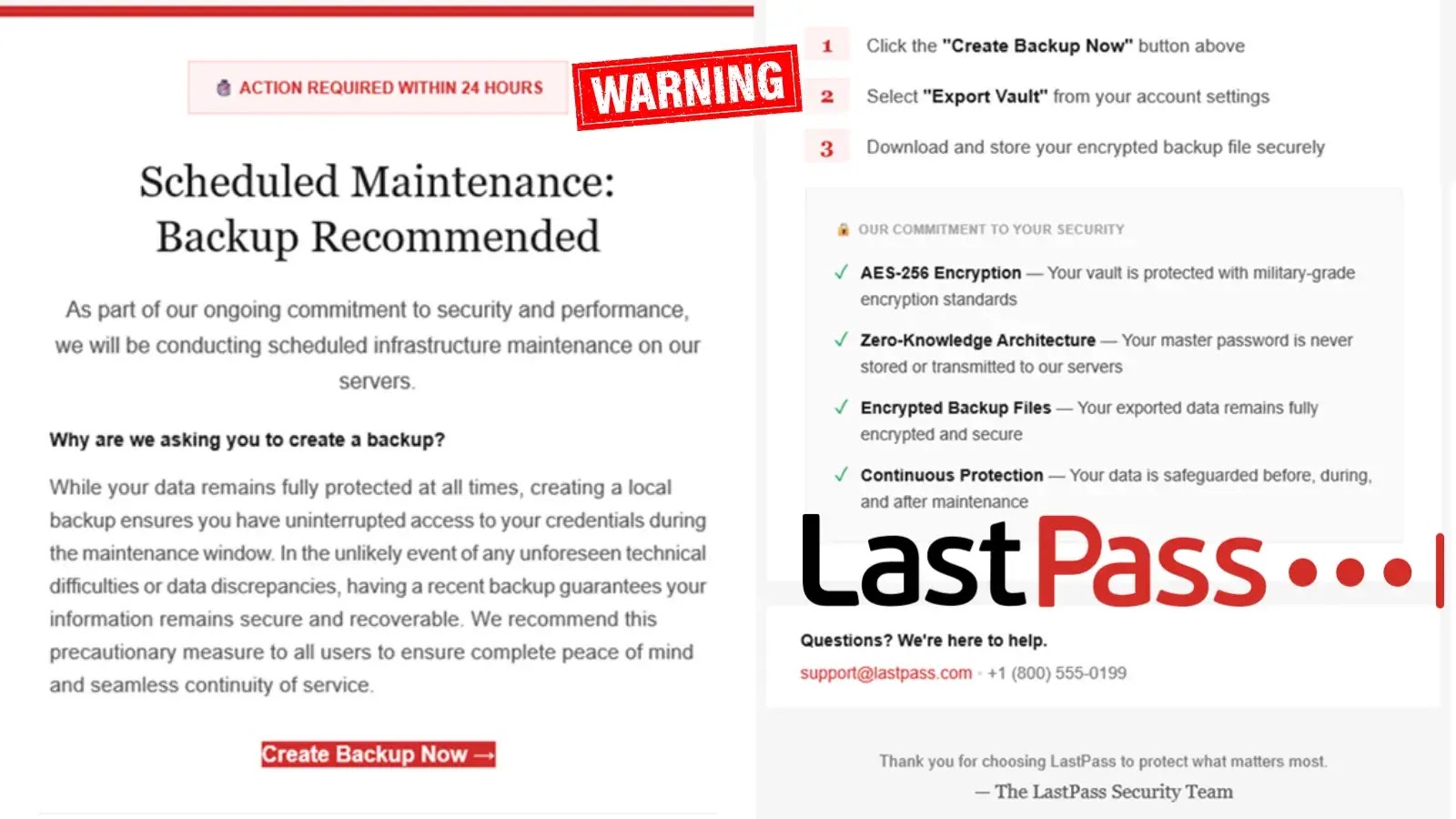
The phishing emails make use of social engineering techniques by creating synthetic urgency, falsely claiming that LastPass upkeep requires prospects to again up their vaults inside 24 hours.
LastPass explicitly confirms it by no means requests buyer grasp passwords or calls for fast vault backups through e-mail.
Faux Upkeep Message (Supply: Lastpass)
The marketing campaign strategically launched over the U.S. vacation weekend, a deliberate timing selection designed to use decreased safety staffing and delayed incident response.
Menace actors generally exploit such home windows to maximise the success fee of compromise earlier than detection.
The phishing infrastructure consists of two main parts: an preliminary redirect hosted on compromised AWS S3 infrastructure and a spoofed area designed to imitate respectable LastPass companies.
Customers ought to instantly delete any emails claiming to require LastPass upkeep.
LastPass confirms that Official communications by no means request grasp passwords, vault backups, or pressing motion through unsolicited emails.
Organizations ought to implement e-mail safety controls to dam messages from the recognized sender addresses and educate employees on phishing indicators, together with artificially pressing language and requests for delicate credentials.
LastPass is coordinating with third-party companions to take down the malicious infrastructure. Customers who obtained these emails are inspired to report them on to [email protected] for evaluation and monitoring.
Comply with us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.