A brand new malware marketing campaign is exploiting pretend Blue Display of Loss of life warnings and trusted Microsoft construct instruments to ship a harmful distant entry trojan.
The operation, tracked as PHALT#BLYX, targets hospitality companies with misleading reservation cancellation emails that manipulate victims into operating malicious code on their techniques.
The assault begins when unsuspecting workers obtain convincing phishing emails disguised as Reserving[.]com reservation alerts.
These messages show alarming costs exceeding €1,000, creating fast panic and prompting recipients to click on “See Particulars” for verification.
As a substitute of reaching authentic reserving data, victims land on professionally crafted pretend web sites that mirror the genuine Reserving.com interface all the way down to its colours, fonts, and logos.
The psychological manipulation capitalizes on urgency and monetary concern, making targets extra more likely to bypass regular safety warning.
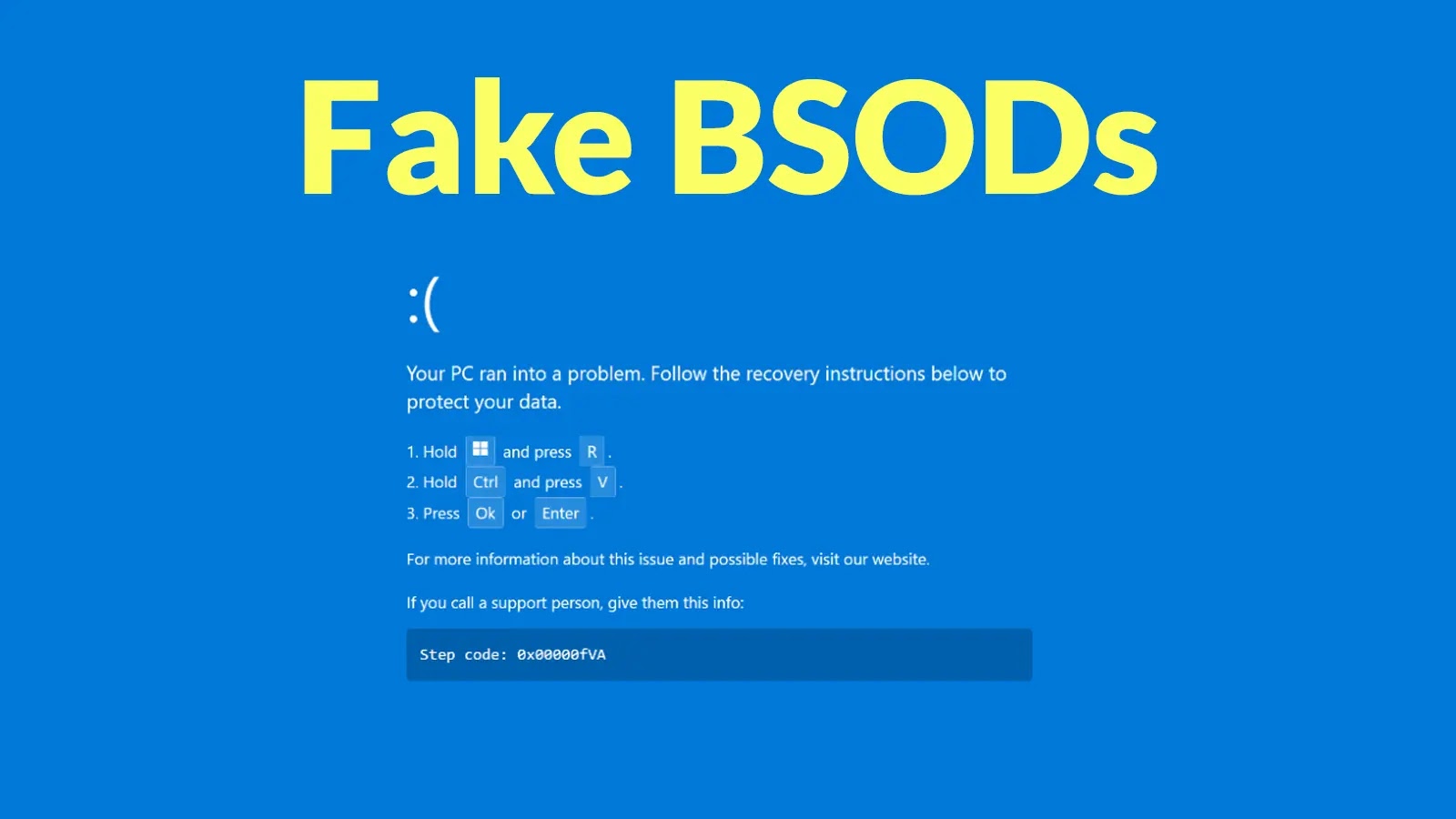
As soon as on the fraudulent web page, victims encounter a pretend browser loading error adopted by a simulated Blue Display of Loss of life that seems alarmingly genuine.
Pretend alert (Supply – Securonix)
The web page instructs customers to “repair” the issue by urgent Home windows key + R, then pasting clipboard content material and urgent Enter.
This ClickFix method methods folks into manually executing PowerShell instructions that obtain malicious mission information and launch them by means of MSBuild.exe, a authentic Microsoft compilation device.
Securonix researchers recognized this marketing campaign after monitoring the evolution of ways from less complicated HTML utility supply strategies to the present subtle MSBuild-based an infection chain.
The shift represents a strategic adaptation towards Dwelling off the Land methods that abuse trusted system utilities to evade conventional antivirus detection.
Evaluation revealed Russian language strings embedded within the malware code, suggesting connections to Russian-speaking menace teams who generally use DCRat in underground boards.
Multi-Stage An infection Course of and Protection Evasion
The malicious PowerShell dropper executes a number of crucial operations concurrently.
It opens the authentic Reserving.com admin web page as a decoy whereas secretly looking out your entire system for MSBuild.exe, downloading a mission file named v.proj from attacker infrastructure, and launching it by means of the Microsoft device.
As a result of MSBuild.exe carries a sound Microsoft signature, utility whitelisting and endpoint safety options typically fail to flag the execution as suspicious.
The v.proj file incorporates embedded PowerShell scripts that instantly goal Home windows Defender by including exclusions for your entire ProgramData listing and particular file extensions together with .exe, .ps1, and .proj.
This preparation ensures the ultimate payload can land on disk with out triggering quarantine alerts.
The malware then makes an attempt privilege escalation by means of UAC spam ways, repeatedly prompting customers to grant administrator rights by means of repetitive pop-ups designed to exhaust their resistance.
After establishing persistence by means of Web Shortcut information within the Startup folder, the malware deploys staxs.exe, a closely obfuscated DCRat variant.
This payload makes use of AES-256 encryption with PBKDF2 key derivation and connects to command-and-control servers at asj77.com, asj88.com, and asj99.com over port 3535.
The trojan injects itself into authentic system processes like aspnet_compiler.exe by means of course of hollowing, successfully masking malicious exercise behind trusted Home windows binaries.
Pretend BSOD (Supply – Securonix)
DCRat capabilities embody keylogging, distant desktop entry, course of injection, and the power to obtain secondary payloads comparable to cryptocurrency miners.
The malware collects complete system fingerprints together with {hardware} identifiers, put in antivirus software program, lively window titles, and area membership standing earlier than sending this intelligence again to operators.
This data permits attackers to evaluate sufferer worth and deploy applicable follow-on instruments for credential theft, lateral motion, or ransomware deployment.
Comply with us on Google Information, LinkedIn, and X to Get Extra Immediate Updates, Set CSN as a Most popular Supply in Google.