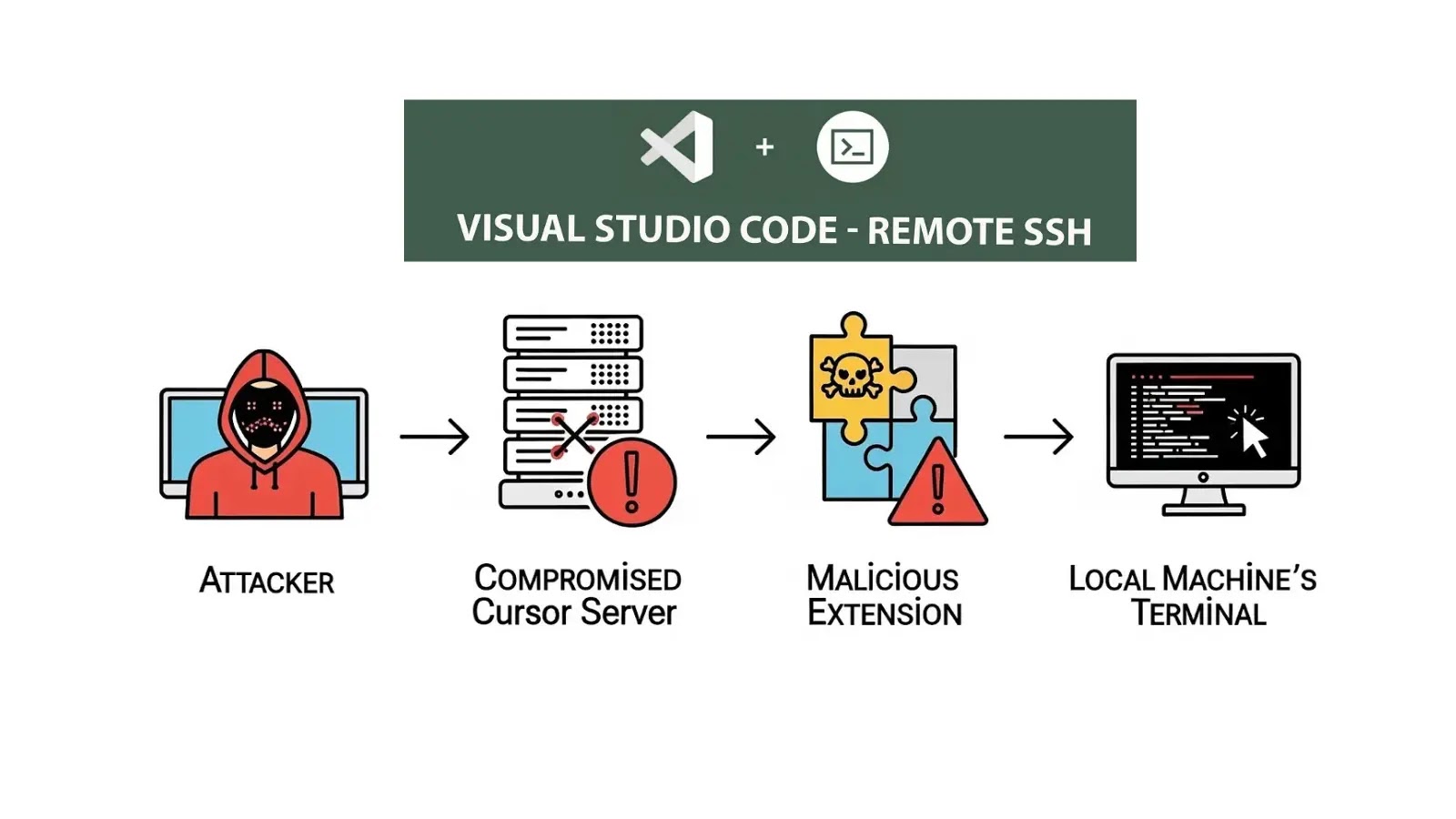
Microsoft launched emergency out-of-band safety updates on January 26, 2026, to handle CVE-2026-21509, a zero-day safety characteristic bypass vulnerability in Microsoft Workplace that attackers are actively exploiting.
The flaw, rated “Necessary” with a CVSS v3.1 base rating of seven.8, depends on untrusted inputs in safety selections to bypass OLE mitigations defending towards weak COM/OLE controls.
CVE-2026-21509 permits native attackers to bypass Workplace protections after tricking customers into opening malicious recordsdata by way of phishing or social engineering.
The assault vector requires low complexity, no privileges, and consumer interplay, however yields excessive impacts on confidentiality, integrity, and availability (C:H/I:H/A:H).
Microsoft Risk Intelligence Middle (MSTIC) confirmed exploitation detection, marking it because the second actively exploited zero-day patched this month after Patch Tuesday’s updates.
Affected Merchandise
The flaw impacts legacy and present Workplace editions; patches rolled out January 26, 2026.
ProductArchitectureKB ArticleBuildOffice 201664-bit500271316.0.5539.1001Office 201632-bit500271316.0.5539.1001Office LTSC 202464/32-bitN/ALatestOffice LTSC 202164/32-bitN/ALatestM365 Apps Enterprise64/32-bitN/ALatestOffice 201964/32-bitN/A16.0.10417.20095
Confirm builds by way of File > Account > About.
Workplace 2021+ customers acquire computerized service-side safety post-restart; 2016/2019 require updates or registry tweaks.
Add DWORD “Compatibility Flags” (worth 400) beneath HKEY_LOCAL_MACHINESOFTWAREMicrosoftOffice16.0CommonCOM Compatibility{EAB22AC3-30C1-11CF-A7EB-0000C05BAE0B} (modify paths for arch/Click on-to-Run). Backup registry first; restart apps after adjustments.
Organizations ought to prioritize patching, allow auto-updates, and monitor phishing IOCs like suspicious Workplace attachments. Risk actors favor this vector for ransomware/APT preliminary entry; deploy EDR for COM/OLE anomalies. No public PoCs or actors named but, however watch CISA KEV for additions.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.