Safety Operations Facilities dwell or die by their capability to reply rapidly and precisely to alerts.
On the coronary heart of this course of is alert triage — the preliminary analysis that decides whether or not an alert is an actual incident, a false optimistic, or one thing that wants instant escalation.
When Tier 1 analysts get triage fallacious, detection pace collapses, response sources are misused, and actual assaults slip by means of unnoticed.
This isn’t a technical hygiene difficulty. It’s a management level for danger. Each alert that’s misjudged at Tier 1 both creates pointless prices or permits actual threats to progress additional into the enterprise.
In different phrases, triage high quality determines whether or not your SOC is a defend or a bottleneck.
Enterprise metrics that rely upon triage high quality
Poor triage doesn’t simply frustrate analysts. It distorts the metrics management really cares about:
MTTD and MTTR: Missed or delayed escalation inflates detection and response occasions.
Price per incident: Tier 2 and Tier 3 groups spend time on noise as an alternative of actual threats.
Safety ROI: Costly instruments generate alerts, however worth is misplaced in the event that they aren’t filtered accurately.
Danger publicity: True incidents which are dismissed or parked too lengthy result in breaches, downtime, and regulatory influence.
Analyst retention: Fixed false escalations burn out senior employees and improve turnover.
When triage is weak, the SOC appears to be like busy whereas the enterprise stays uncovered.
The fact of a typical Tier 1 analyst
Most Tier 1 roles are entry-level positions crammed by junior analysts or current graduates. They’re usually enthusiastic however lack deep expertise with real-world assaults.
They work in high-pressure environments with alert queues that by no means empty, strict SLAs, and restricted incident response instruments for fast context.
Anticipating these analysts to persistently make correct, quick choices with out satisfactory assist is unrealistic. The position units them up for frustration and errors quite than success.
This isn’t a expertise drawback. It’s a structural one. Even a motivated, succesful junior analyst can’t persistently make high-quality triage choices with out assist. Three core deficiencies routinely undermine Tier 1 efficiency:
Lack of expertise: New analysts haven’t seen sufficient assault patterns to acknowledge delicate indicators of compromise.
Lack of time: Alert quantity forces snap judgments; there’s not often time for deeper analysis.
Lack of knowledge: Primary alerts usually present solely an IP, hash, or URL with no instant context about popularity, habits, or associated indicators.
The result’s predictable:
Actual incidents are missed or downgraded,
Benign alerts are escalated “simply in case”,
Tier 2 turns into a noise filter as an alternative of an investigation unit,
Budgets are wasted, and danger quietly grows.
The Answer: Actionable Alert Context
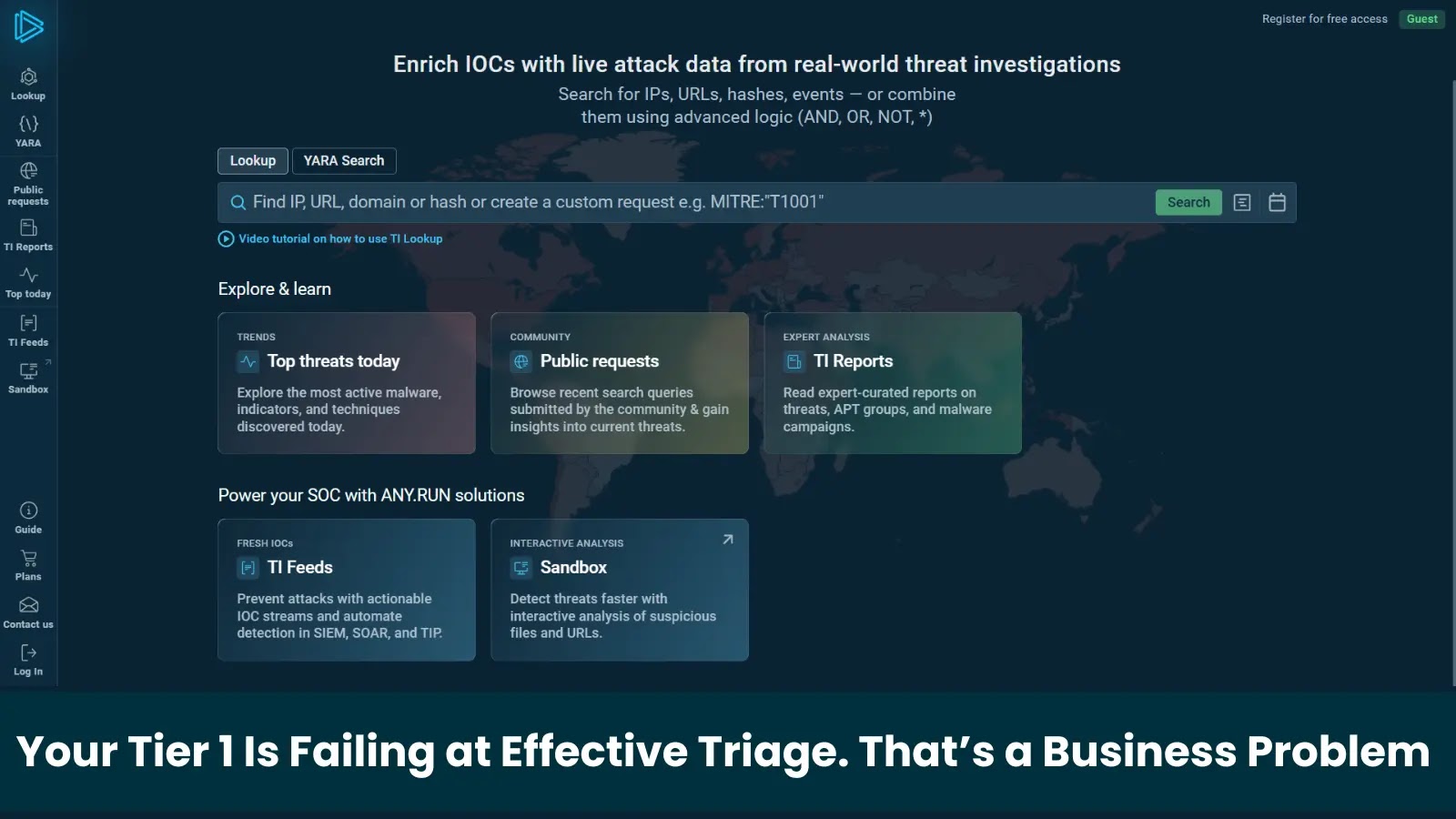
The repair is easy: give Tier 1 analysts wealthy, instant context for each indicator they examine. That is precisely what ANY.RUN’s Menace Intelligence Lookup delivers.
When an analyst encounters an unknown IP, hash, URL, or area, a single lookup immediately returns actionable intelligence drawn from hundreds of thousands of actual malware analyses carried out in ANY.RUN’s Interactive Sandbox by over 15K SOC groups destinationIP:”72.230.113.57″
Fast suspicious IP verify in TI Lookup
A typical lookup for an indicator of compromise (IOC) returns an actionable verdict on the indicator, together with the risk identify and last-seen date.
It additionally highlights lately focused industries and geographic areas and accommodates direct hyperlinks to pattern sandbox analyses displaying the total assault chain.
The outcomes of such content material enrichment influence enterprise targets straight: 1. Extra alerts processed; 2. Fewer incidents omitted; 3. Downtime prevented 4. Tier 2 &3 expensive time not wasted on low-level duties; 5. Prices optimized.
Cut back incident prices by fixing triage. Use TI Lookup to course of extra alerts quicker and minimize response time.and cease losing Tier 2 time on noise.
SOC Experience Progress Via Investigation
Past instant triage choices, TI Lookup offers ongoing schooling for junior analysts. The platform doesn’t simply let you know an indicator is malicious—it exhibits you why by means of hyperlinks to precise sandbox analyses the place that indicator appeared.
An analyst investigating a suspicious file hash can view the entire execution chain from actual assaults. They see how the malware unpacked, what community connections it made, what information it modified, what processes it spawned.
A search by an assault method identify kinds out contemporary samples of such assaults dissected within the Sandbox: threatName:”clickfix”
Lookup for assaults with ClickFix mechanics and see how they work
This transforms triage from rote decision-making into steady studying. Every investigation builds the analyst’s psychological mannequin of how assaults work.
Over time, they develop sample recognition that partially compensates for his or her restricted direct incident response expertise.
Conclusion: The Enterprise Consequence
When Tier 1 triage improves, the influence reaches far past the SOC:
Sooner detection and response,
Decrease investigation prices,
Decreased escalation noise,
Higher use of senior analyst time,
Decrease breach danger and enterprise disruption.
The funding in alert context isn’t about including new functionality. It’s about enabling your current crew to operate at a better stage. Your Tier 1 analysts wish to make good choices.
They merely want the data to make that potential. Offering complete, actionable context turns triage from a guessing recreation into an knowledgeable choice course of.
Improve SOC effectivity with out including headcount. Enhance triage high quality & cut back MTTR.
Your safety operation’s effectiveness is simply as robust as its weakest hyperlink. For many organizations, that hyperlink is Tier 1 triage. Repair triage, and also you don’t simply enhance safety operations.
You shield the enterprise the place it really hurts: time, cash, and danger.