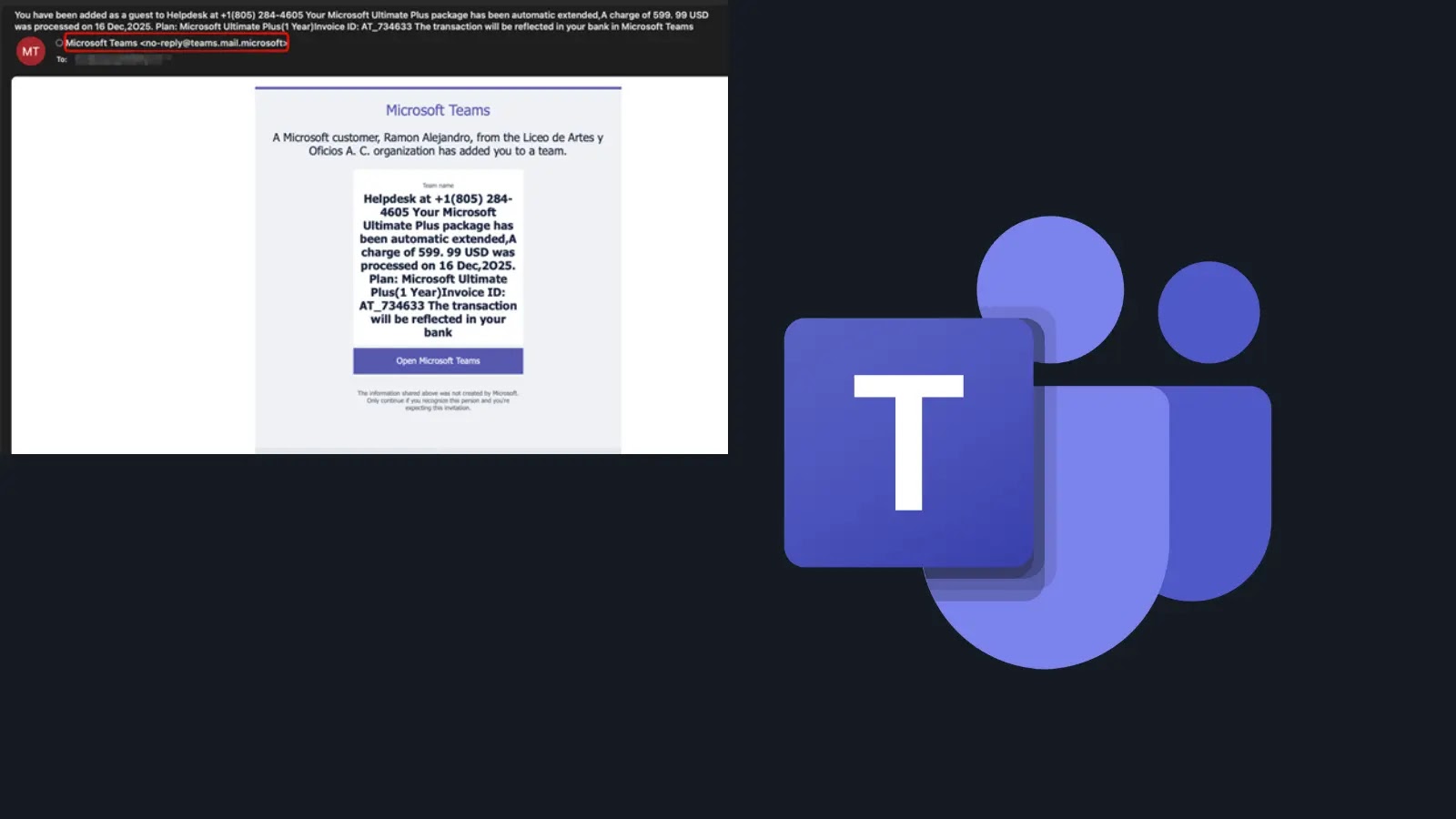
A classy phishing marketing campaign has been recognized by which risk actors are abusing reputable Microsoft Groups performance to distribute malicious content material that seems to originate from trusted Microsoft companies.
By leveraging the platform’s “Invite a Visitor” function and crafting misleading group names, attackers are bypassing conventional electronic mail safety controls to ship fraudulent billing notifications on to victims’ inboxes.
The assault methodology depends on exploiting the belief customers place in automated notifications from collaboration platforms. Reasonably than spoofing electronic mail addresses or injecting malicious URLs, the attackers create new groups inside Microsoft Groups, assigning them names designed to imitate pressing monetary alerts. These names usually reference subscription renewals or auto-pay notices to induce panic.
A particular instance noticed within the wild contains group names resembling: “Subscription Auto-Pay Discover (Ivoice ID: 2025_614632PPOT_SAG Quantity 629. 98 USD). Should you didn’t authorize or full this m0nthly Fee,plese c0ntact our assist group urgently.”
As soon as the group is created, the attacker sends invites to exterior targets utilizing the native “Invite a Visitor” function. The recipient receives an electronic mail instantly from a reputable Microsoft deal with (e.g., noreply@electronic mail.groups.microsoft.com).
Pretend Microsoft Groups Invite (Supply: Checkpoint)
As a result of the e-mail infrastructure is real, it simply passes SPF, DKIM, and DMARC checks. Nevertheless, the physique of the e-mail shows the malicious group title containing the fraudulent billing message and a assist telephone quantity in a big, distinguished font.
This marketing campaign is distinct in its use of phone-based social engineering (vishing). As a substitute of directing customers to a credential-harvesting website, the textual content instructs victims to name a fraudulent assist line to resolve the alleged cost.
To evade automated content material filters, attackers make use of obfuscation strategies inside the group title, using character substitutions, blended Unicode characters, and visually comparable glyphs.
The dimensions of this operation is important, with telemetry indicating a broad, indiscriminate method reasonably than focused espionage. Safety researchers recorded a complete of 12,866 phishing messages distributed in the course of the marketing campaign’s peak, averaging 990 messages each day. These assaults reached roughly 6,135 distinct clients.
The distribution of targets suggests the attackers aimed to take advantage of widespread Microsoft Groups adoption. The manufacturing, engineering, and building sectors bore the brunt of the exercise, accounting for 27.4% of affected organizations.
This was adopted by the Know-how/SaaS/IT sector at 18.6% and the Schooling sector at 14.9%. Different affected verticals included skilled companies, authorities, and finance.
Geographic Distribution of Targets
The marketing campaign demonstrated a world attain, although the first focus remained on North American targets. Organizations in the USA comprised 67.9% of the sufferer pool. European entities accounted for 15.8%, adopted by Asia at 6.4%.
A particular regional breakdown of the Latin American (LATAM) impression exhibits a focus in Brazil and Mexico:
CountryPercentage of LATAM TargetsBrazil44percentMexico31percentArgentina11percentColombia8percentChile4percentPeru2%
This marketing campaign highlights a essential hole in collaboration safety: the reliance on content material inspection inside invites generated by trusted platforms. For the reason that electronic mail supply mechanism is reputable, organizations can’t rely solely on electronic mail authentication protocols to dam these threats.
Safety groups are suggested to coach customers on scrutinizing sudden Groups invites, notably these containing pressing monetary language, telephone numbers, or uncommon character formatting.
Observe us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.