Key Points
- A new PDFly malware variant employs modified PyInstaller to evade detection.
- Security analysts need to reverse-engineer multiple encryption layers.
- Shared techniques with PDFClick suggest a coordinated threat campaign.
A sophisticated version of the PDFly malware has surfaced, presenting new challenges for cybersecurity experts. This variant uses a custom-modified PyInstaller executable, rendering standard analysis tools ineffective and compelling researchers to engage in manual reverse-engineering to decipher its encryption.
The Challenge of Advanced Encryption
Security specialists are facing significant hurdles in examining the latest PDFly malware due to its customized PyInstaller format. This adaptation alters key identifiers and encodes Python bytecode under multiple protective layers. As a result, traditional methods of extraction are rendered futile, obligating analysts to manually decode the malware’s intricate decryption process.
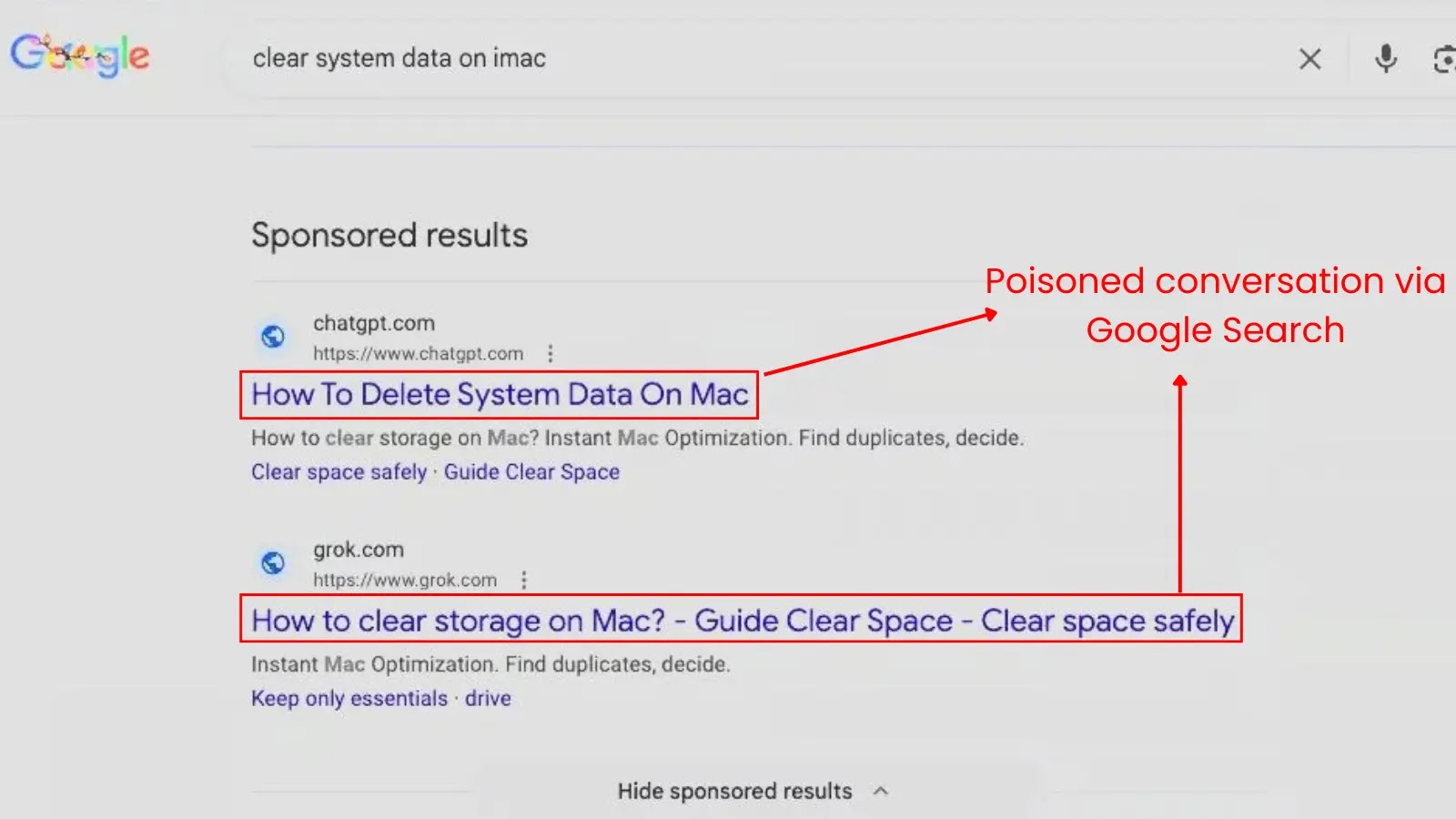
The initial PDFly incident came to light when security researcher Luke Acha highlighted the application online. Subsequently, another sample known as PDFClick was identified, indicating that cybercriminals are actively refining this evasion technique. Both samples exhibit a consistent modification strategy, suggesting their inclusion in a larger campaign aimed at bypassing security measures.
Decoding the PyInstaller Modifications
In-depth analysis by Samplepedia’s researchers unveiled the encryption mechanisms embedded within the malware’s components. Despite the failure of standard tools to process the executable, researchers employed disassemblers to uncover the modified attributes. They discovered that the encryption wasn’t housed in the PyInstaller stub itself but rather within separate bootstrap files responsible for runtime archive extraction.
The developers of the malware have devised a sophisticated encryption algorithm to safeguard the PYZ archive contents against scrutiny. By adapting the PyInstxtractor script to identify the custom magic cookie and bypass validation checks, investigators found that the decrypted files remained inaccessible.
Reversing the Complex Decryption Process
The decryption involves a meticulous sequence essential for accessing the malicious code. Initially, the archived data undergoes XOR decryption using a 13-byte key named SCbZtkeMKAvyU. This is followed by zlib decompression to restore the file’s structure. A subsequent XOR operation with a 7-byte key, KYFrLmy, further obscures the data, before the bytes are reversed and processed into executable code objects using Python’s marshal module.
In response, security researchers have developed a versatile extractor tool capable of managing multiple variants with differing encryption keys. The tool autonomously locates legitimate cookie structures within the PE overlay, confirming them by assessing package length, table-of-contents offset, and Python version fields. Once identified, the extractor analyzes the pyimod01_archive.pyc bytecode to retrieve XOR keys from generator expressions in the ZlibArchiveReader class, facilitating the decryption of future samples.
Conclusion
The emergence of this advanced PDFly malware variant underscores the evolving tactics of cybercriminals and the need for robust security measures. As threat actors continue to innovate, it becomes imperative for security teams to refine their tools and techniques to effectively counteract such sophisticated threats.