The Iranian cyber threat group Infy, also known as the Prince of Persia, has taken steps to conceal their operations by modifying their command-and-control (C2) infrastructure. This move comes on the heels of the Iranian government’s decision to end a significant internet blackout, which began earlier in the month.
Strategic Changes in Cyber Operations
According to Tomer Bar, vice president of security research at SafeBreach, Infy ceased maintaining their C2 servers on January 8, coinciding with Iran’s nationwide internet shutdown. This action suggests that even state-aligned cyber units were temporarily inactive during the blackout.
However, activity resumed on January 26, as new C2 servers were established just before the Iranian authorities lifted the internet restrictions. This timing indicates a strong likelihood of state sponsorship for the group, aligning with Iran’s strategic interests.
Infy’s Evolving Tactics
Infy is among the numerous state-sponsored hacker groups in Iran, known for espionage and influence campaigns. Despite being active since 2004, Infy has remained less visible compared to its counterparts. Their operations have been described as ‘laser-focused’ on intelligence gathering from targeted individuals.
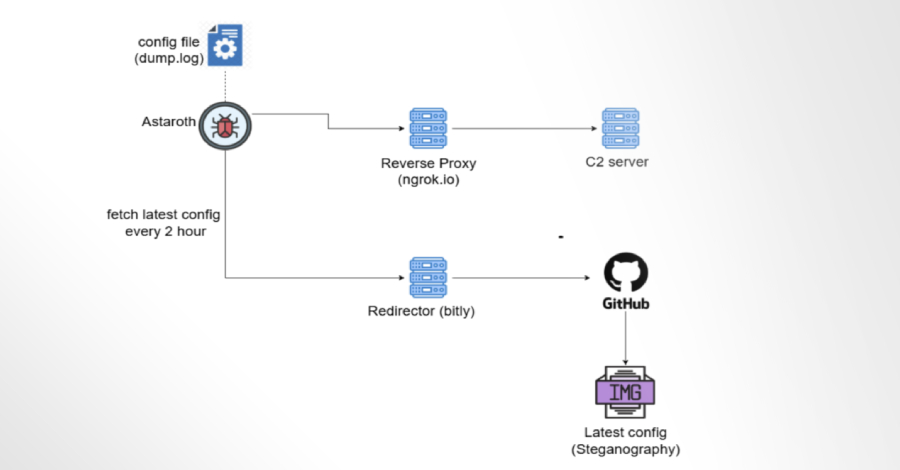
Recent findings by SafeBreach reveal that the group has adopted updated versions of their tools, namely Foudre and Tonnerre. Notably, Tonnerre’s latest iteration, dubbed Tornado, utilizes both HTTP and Telegram for C2 communication, incorporating a unique domain generation algorithm and blockchain data techniques for enhanced flexibility.
Exploiting Security Vulnerabilities
In a strategic shift, Infy has leveraged a one-day security flaw in WinRAR, identified as either CVE-2025-8088 or CVE‑2025‑6218, to deploy the Tornado payload. This tactic aims to increase the success rate of their cyber campaigns. The RAR files containing the payload were detected on the VirusTotal platform in December 2025.
Within these files, a self-extracting archive includes two components: the main Tornado DLL and an installer that ensures persistence by checking for Avast antivirus presence before executing the malware. Tornado communicates with its C2 server through HTTP to gather system data and execute commands.
Future Implications and Correlations
Infy’s use of Telegram for C2 purposes continues, with changes in user handles and group configurations noted in the latest version. SafeBreach’s analysis of messages extracted from private Telegram groups unveiled crucial insights into Infy’s operations, including the deployment of ZZ Stealer malware.
This malware is linked to a broader campaign targeting the Python Package Index repository. The data also suggests potential ties between Infy and other Iranian groups like Charming Kitten, based on shared techniques and tools.
As Infy adapts its strategies, cybersecurity experts remain vigilant in monitoring their activities, emphasizing the need for robust defenses against state-sponsored cyber threats.