A previously unknown cyber espionage collective, identified as TGR-STA-1030, has reportedly compromised the networks of over 70 governmental and critical infrastructure organizations in 37 countries over the past year. This revelation comes from a report by Palo Alto Networks’ Unit 42, highlighting the pervasive threat this group poses to global security.
Extensive Global Reach
The cyber group has been conducting detailed reconnaissance on government infrastructures linked to 155 countries from November to December 2025. Among the entities breached are five national law enforcement and border control agencies, three ministries of finance, and various other governmental departments involved in economic, trade, natural resources, and diplomatic activities.
Tracked as TGR-STA-1030, where ‘TGR’ denotes temporary threat group and ‘STA’ indicates state-backed intent, the group has been active since January 2024. Although the group’s exact origin is not confirmed, evidence suggests an Asian provenance, based on their operational tools, preferences, and timing.
Intricate Phishing Techniques
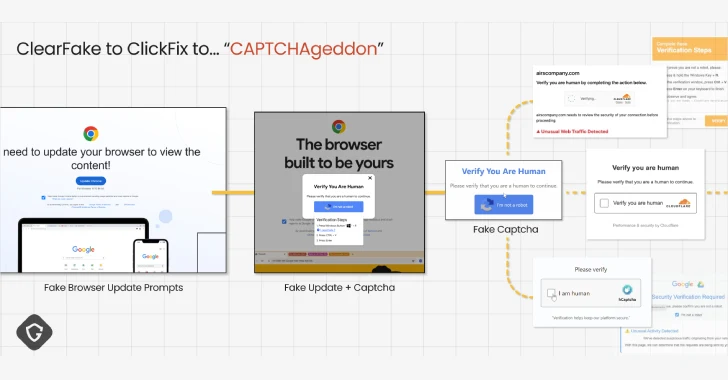
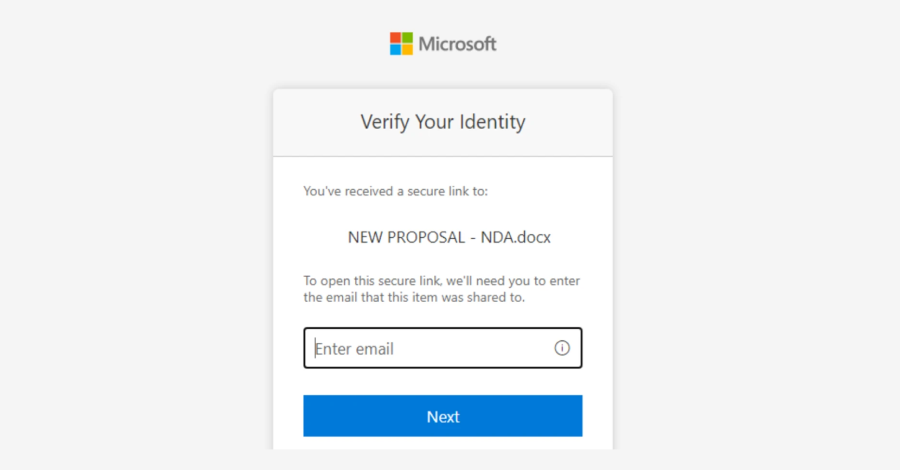
The attack strategy of TGR-STA-1030 primarily involves phishing emails that direct victims to a file hosted on the New Zealand-based service MEGA. This file contains a ZIP archive with an executable named Diaoyu Loader and a zero-byte file titled “pic1.png.” This approach is designed to bypass automated sandbox analysis.
According to Unit 42, the malware execution depends on specific conditions, such as a screen resolution of at least 1440 pixels horizontally and the presence of the “pic1.png” file in the execution directory. The malware then checks for specific cybersecurity programs, including those from Avira, Bitdefender, Kaspersky, Sentinel One, and Symantec.
Exploiting Vulnerabilities
TGR-STA-1030 has also been exploiting known vulnerabilities in software from Microsoft, SAP, Atlassian, Ruijieyi Networks, Commvault, and Eyou Email System. The group uses various tools, such as command-and-control frameworks, web shells, and tunneling utilities, frequently associated with Chinese hackers.
One significant tool used by the group is a Linux kernel rootkit named ShadowGuard, which leverages Extended Berkeley Packet Filter technology to hide processes and files from user-space analysis tools, thereby maintaining stealth.
Impact and Future Implications
The group has managed to sustain access to multiple compromised entities for extended periods, suggesting a focus on prolonged intelligence collection. TGR-STA-1030 targets government ministries and departments primarily for espionage purposes, with a particular interest in countries engaged in specific economic partnerships.
The ongoing operations of TGR-STA-1030 present a significant threat to global government and infrastructure security. Their continued focus on espionage, combined with their sophisticated methods, poses potential long-term risks to national security and critical services worldwide.