OpenClaw has taken a significant step in enhancing security by partnering with VirusTotal to scan skills uploaded to ClawHub, its skill marketplace. This collaboration aims to strengthen the security of the agentic ecosystem, as announced by OpenClaw’s founder Peter Steinberger along with team members Jamieson O’Reilly and Bernardo Quintero.
Integration with VirusTotal
Every skill uploaded to ClawHub is now analyzed using VirusTotal’s threat intelligence, including their new Code Insight feature. This process involves generating a unique SHA-256 hash for each skill and checking it against VirusTotal’s database. If a match is not found, the skill is further analyzed using VirusTotal’s capabilities. Skills marked as benign are automatically approved, while suspicious ones receive a warning and malicious skills are blocked from download.
OpenClaw ensures ongoing protection by re-scanning all active skills daily, addressing cases where previously clean skills might become harmful. However, the company cautions that VirusTotal scanning is not infallible, and some cleverly disguised threats may still evade detection.
Additional Security Measures
Beyond the VirusTotal partnership, OpenClaw plans to release a detailed threat model, a public security roadmap, and a formal security reporting process. This development follows reports of numerous malicious skills on ClawHub, which prompted the addition of a user reporting feature for suspicious activities.
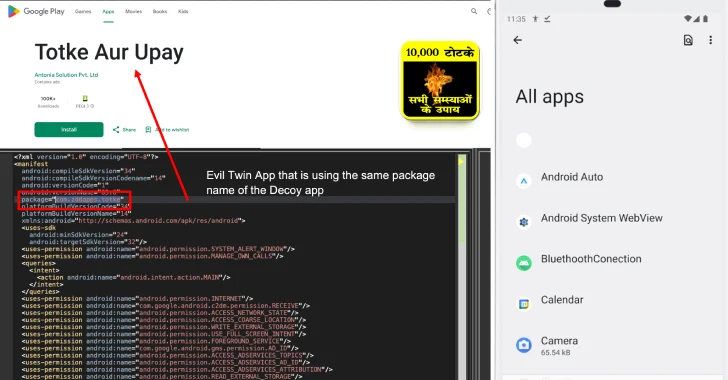
Security analyses have revealed that some skills disguise themselves as legitimate but possess harmful functionalities like data exfiltration and malware installation. This poses a risk as AI agents with system access can bypass traditional security measures, acting as covert channels for data leaks and unauthorized executions.
Challenges and Risks
OpenClaw’s recent popularity has highlighted potential security risks, especially given its role as an automation engine interacting with various online services. The extensive access granted to skills could lead to vulnerabilities such as prompt injection attacks and data exfiltration.
Security experts have pointed out architectural flaws in OpenClaw’s design, including reliance on language models for security decisions and inadequate protections against indirect prompt injections. Moreover, storing credentials in plaintext and lacking explicit user approvals for tool executions pose significant security threats.
These concerns have prompted regulatory attention, with China’s Ministry of Industry and Information Technology issuing alerts about misconfigured instances. Experts emphasize the importance of securing agent platforms to prevent them from becoming unintended tools for attackers.
Looking ahead, OpenClaw’s efforts to bolster security through partnerships and comprehensive measures are crucial in addressing the evolving threats in the AI landscape.