Enterprise E mail Compromise (BEC) assaults don’t want malware to do injury. All it takes is one convincing message; a pretend login immediate, a cleverly disguised hyperlink, and an worker’s credentials are gone.
From there, attackers can quietly entry inboxes, exfiltrate delicate paperwork, and impersonate executives for monetary fraud.
The worst half is that these assaults are sometimes missed by commonplace e-mail filters and antivirus instruments.
That’s why safety groups are turning to options like interactive sandboxing to catch what automated instruments can’t.
What Makes BEC So Exhausting To Detect?
Enterprise E mail Compromise doesn’t depart apparent digital fingerprints. As an alternative, it hides in plain sight, utilizing clear infrastructure, normal-looking messages, and delicate social engineering.
Right here’s why they usually go unnoticed:
Effectively-hidden intent – No malware, simply hyperlinks disguised as routine enterprise.
Trusted platforms – Hosted on providers like OneDrive or Google Varieties, which hardly ever elevate flags.
Redirect chains – A number of hops earlier than the true phishing web page seems.
CAPTCHAs and blockers – Designed to cease bots and automatic scanners of their tracks.
Human-first ways – Depends on social stress, not code execution.
Context-aware messages – Tailor-made with names, roles, and inside language to keep away from suspicion.
The Quickest Method To Spot A BEC Assault
When time is crucial, ready hours for a verdict simply received’t reduce it. Interactive sandboxes give safety groups the ability to research suspicious information or URLs in minutes, not hours or days.
As an alternative of counting on static scans or logs, analysts can watch the assault unfold in actual time, work together with it like an actual person would, and uncover the complete scope of the menace.
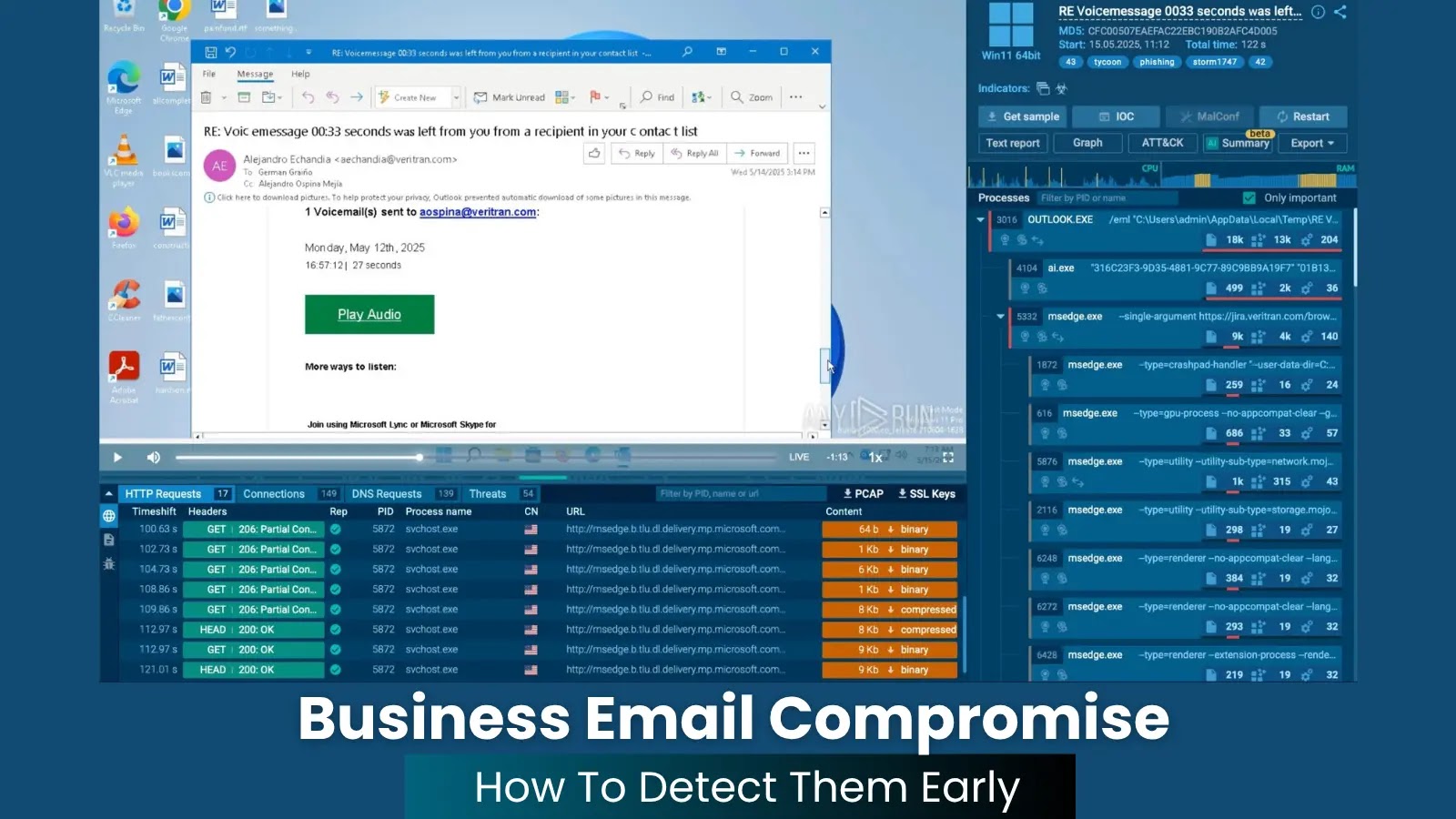
To indicate how this works in apply, let’s check out a real-world phishing assault detonated inside ANY.RUN’s Interactive Sandbox.
View evaluation session with assault
Evaluation of suspicious information inside ANY.RUN sandbox
This assault begins with a seemingly innocent e-mail containing a big inexperienced “Play Audio” button, a standard lure utilized by the Tycoon2FA phishing package, one of the crucial widespread threats in company environments in the present day.
Right here’s how the sandbox reveals the complete chain:
1. Opening The E mail In A Secure VM
The e-mail is uploaded to the sandbox and opened inside a totally remoted Home windows setting. The analyst can safely click on the “Play Audio” button to see what occurs subsequent, no threat to their actual system.
“Play Audio” button displayed inside interactive sandbox
2. Following The Redirect Chain
Earlier than beginning the evaluation, customers can allow Automated Interactivity, a characteristic in ANY.RUN that simulates actual person conduct, like clicking buttons, fixing CAPTCHAs, and navigating redirects.
As soon as turned on, the sandbox takes over these repetitive duties robotically, permitting analysts to look at the complete assault circulate with out handbook enter.
Equip your staff with real-time phishing detection, automated evaluation, and full assault chain visibility — multi functional interactive sandbox.– Be part of ANY.RUN now
In our instance, clicking the “Play Audio” button triggers a sequence of redirects, a traditional evasion method used to obscure the ultimate phishing vacation spot.
Finally, a CAPTCHA problem seems, designed to dam automated scanners.
CAPTCHA problem solved by ANY.RUN sandbox
However with Automated Interactivity enabled, ANY.RUN handles this seamlessly, fixing the CAPTCHA and persevering with the evaluation circulate, saving precious time and decreasing workload.
The sandbox reaches the ultimate phishing web page inside seconds, with none handbook effort, making it superb for quick triage or high-volume alert queues.
3. Reaching The Remaining Phishing Web page
After fixing the CAPTCHA, the sandbox lands on a pretend Microsoft login web page; clear design, acquainted branding, however a suspicious URL filled with random characters and a lacking favicon.
Crimson flags a person would possibly miss however the sandbox doesn’t.
Phishing indicators detected inside ANY.RUN sandbox
4. Exposing The Technical Particulars
Interactive sandboxes like ANY.RUN map out the whole assault chain so your staff can perceive precisely how the menace works and the place to reply.
Listed here are just a few particulars the sandbox revealed on this session with Tycoon assault:
Full Course of Tree On this case, the method tree clearly flagged a suspicious browser course of initiated after clicking the “Play Audio” button. It was labeled as Phishing, with subprocesses exhibiting browser redirects and script execution.
Malicious course of recognized by sandbox
The method tree inside ANY.RUN supplies a step-by-step breakdown of how the phishing web page was reached, giving groups the visibility wanted to hint multi-stage BEC threats that always disguise in person actions.
Community Requests: The sandbox captured each HTTP/HTTPS request, together with redirect URLs and the ultimate phishing area, a pretend Microsoft login web page hosted on a random, non-branded area.
Community requests captured
We see how the sandbox exposes the complete attacker infrastructure behind the Tycoon2FA package, permitting groups to dam malicious endpoints and perceive how the phishing marketing campaign is ready up.
Suricata Alerts :Throughout the session, a Suricata rule fired: “PHISHING [ANY.RUN] Suspected Tycoon2FA’s Phishing-Package Area”.
Suricata rule triggered by Tycoon2FA
This alert immediately validates the menace with a particular detection signature, rushing up the decision-making course of and permitting safety groups to reply with confidence.
Tagged Verdict : ANY.RUN robotically tagged the pattern as linked to the Tycoon2FA phishing package, figuring out the marketing campaign behind the pretend login circulate.
Tycoon detected by ANY.RUN sandbox
Eliminates guesswork and ensures quick triage; even junior analysts can rapidly classify and report on the menace with out deep handbook investigation.
How Interactive Sandbox Helps You Keep Forward Of BEC Threats
Interactive sandboxing offers groups the context, visibility, and pace they should detect and reply to Enterprise E mail Compromise threats earlier than they escalate.
Right here’s how ANY.RUN delivers that benefit:
Reside visibility into menace conduct Watch the complete assault chain unfold, from the preliminary lure to redirects, CAPTCHA challenges, and the ultimate phishing web page, in actual time.
Sooner, extra assured selections Get an preliminary verdict in below 40 seconds, with behavioral proof to help quicker triage and response.
Automated Interactivity to cut back workload Automate frequent person actions like clicking buttons, fixing CAPTCHAs, and following redirects. This protects time and helps analysts concentrate on higher-level decision-making.
Cloud-based, no setup required Analyze information and URLs in a safe digital setting from wherever, no infrastructure upkeep or native configuration wanted.
Centralized IOC assortment Accumulate and export domains, IPs, URLs, file hashes, and different indicators of compromise in a single click on, prepared for blocking, reporting, or enrichment.
Constructed-in menace classification Get speedy context with labeled processes, triggered Suricata guidelines, and campaign-level tagging (e.g., Tycoon2FA) to hurry up identification.
Helps all analyst talent ranges Whether or not it’s a junior SOC analyst or a senior menace hunter, ANY.RUN presents an intuitive interface and detailed reporting to help investigation, studying, and collaboration.
Improves safety workflows Reduces alert fatigue, shortens incident response time, and helps groups prioritize actual threats over false positives.
Equip your staff with the answer to detect subtle phishing threats in actual time, cut back analyst workload, and reply with confidence: Be part of ANY.RUN to expertise its full capabilities for 14 days →