Could 07, 2025Ravie LakshmananVulnerability / IT Service
Cybersecurity researchers have disclosed a number of safety flaw within the on-premise model of SysAid IT assist software program that may very well be exploited to attain pre-authenticated distant code execution with elevated privileges.
The vulnerabilities, tracked as CVE-2025-2775, CVE-2025-2776, and CVE-2025-2777, have all been described as XML Exterior Entity (XXE) injections, which happen when an attacker is ready to efficiently intrude with an software’s parsing of XML enter.
This, in flip, may allow attackers to inject unsafe XML entities into the online software, permitting them to hold out a Server-Aspect Request Forgery (SSRF) assault and in worst instances, distant code execution.
An outline of the three vulnerabilities, in accordance with watchTowr Labs researchers Sina Kheirkhah and Jake Knott, is as follows –
CVE-2025-2775 and CVE-2025-2776 – A pre-authenticated XXE inside the /mdm/checkin endpoint
CVE-2025-2777 – A pre-authenticated XXE inside the /lshw endpoint
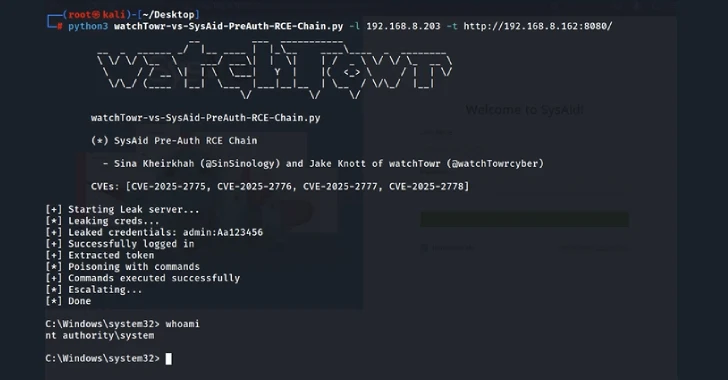
watchTowr Labs described the vulnerabilities as trivial to use via a specifically crafted HTTP POST request to the endpoints in query.
Profitable exploitation of the issues may allow an attacker to retrieve native recordsdata containing delicate info, together with SysAid’s personal “InitAccount.cmd” file, which incorporates details about the administrator account username and plaintext password created throughout set up.
Armed with this info, the attacker may then acquire full administrative entry to SysAid as an administrator-privileged consumer.
To make issues worse, the XXE flaws may very well be chained with one other working system command injection vulnerability – found by a third-party – to attain distant code execution. The command injection problem has been assigned the CVE identifier CVE-2025-2778.
All 4 vulnerabilities have been rectified by SysAid with the discharge of on-premise model 24.4.60 b16 in early March 2025. A proof-of-concept (PoC) exploit combining the 4 vulnerabilities has been made accessible.
With safety flaws in SysAid (CVE-2023-47246) beforehand exploited by ransomware actors like Cl0p in zero-day assaults, it is crucial that customers replace their cases to the newest model.
Discovered this text fascinating? Comply with us on Twitter and LinkedIn to learn extra unique content material we put up.