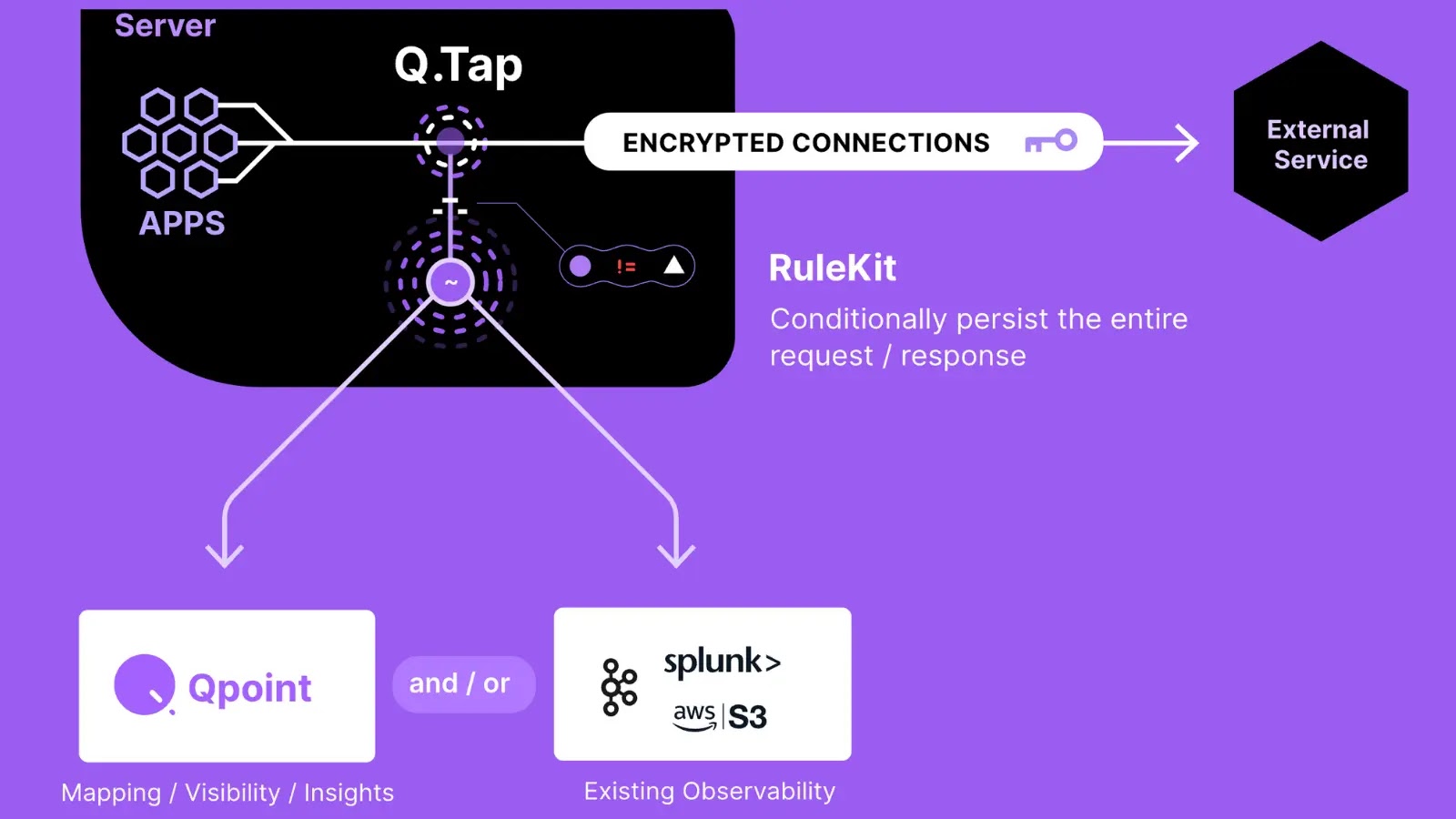
Qpoint has launched Qtap, an open-source eBPF agent for monitoring community visitors in Linux techniques. It hooks into TLS/SSL features to seize knowledge earlier than and after encryption, displaying unencrypted visitors with particulars like course of, container, host, person, and protocol.
Qtap runs out-of-band with low overhead, including no latency or disrupting apps.
Qtap makes it simple to see what’s occurring in your community, particularly for complicated apps, third-party companies, or legacy techniques. It’s light-weight, safe, and works with out invasive setup.
What Qtap Does
Qtap empowers builders, safety professionals, and system directors to achieve deep insights into egress visitors with out modifying functions, putting in proxies, or managing certificates. Whether or not you’re auditing delicate knowledge, debugging community points, or exploring legacy techniques, Qtap gives a transparent view of what’s occurring in your community.
Key Options and Use Circumstances
Qtap’s versatility makes it a foundational part for observability pipelines and customized options like Qpoint. Its key use circumstances embody:
Safety Auditing: Confirm that delicate knowledge isn’t being uncovered in community communications.
Community Debugging: Diagnose API errors, misconfigured parameters, or sudden responses with real-time visitors insights.
API Growth: Guarantee functions ship appropriately formatted requests and deal with responses as anticipated.
Third-Occasion Integrations: Verify knowledge exchanges with exterior companies align with documentation.
Studying & Exploration: Research protocol habits by observing reside visitors.
Legacy Techniques: Acquire insights into poorly documented techniques with out supply code entry.
Validation Testing: Verify software adjustments don’t disrupt community communication patterns.
Find out how to Begin
Attempt Qtap in Demo Mode to see visitors in your terminal:
bash
$ curl -s | sudo sh
To put in and run:
bash
# Set up Qtap
$ curl -s | sudo sh
# Run with defaults
$ sudo qtap
Qtap wants Linux kernel 5.10+ with BTF and eBPF enabled (examine /sys/kernel/btf/vmlinux). It requires elevated permissions: sudo on the host or CAP_BPF and privileged mode in Docker.
Growing Qtap
Qtap is on GitHub. Builders can contribute utilizing:
OS: Linux (kernel 5.10+). MacOS customers can use Lima for a Linux VM.
Instruments: Go 1.24+, make, clang 14 (required), clang-tidy (non-obligatory).
bash
Clone and construct:
$ git clone
$ make construct
Widespread make instructions:
construct: Builds eBPF binaries and Go app.
generate: Creates eBPF binaries.
run: Begins a debug occasion.
ci: Runs CI checks.
Qtap is in early growth. APIs might change, and documentation is likely to be incomplete. Suggestions is welcome through GitHub Points or Discussions. Contributors conform to a Contributor License Settlement for open-source and industrial use.
Automate risk response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs throughout all endpoints -> Request full entry