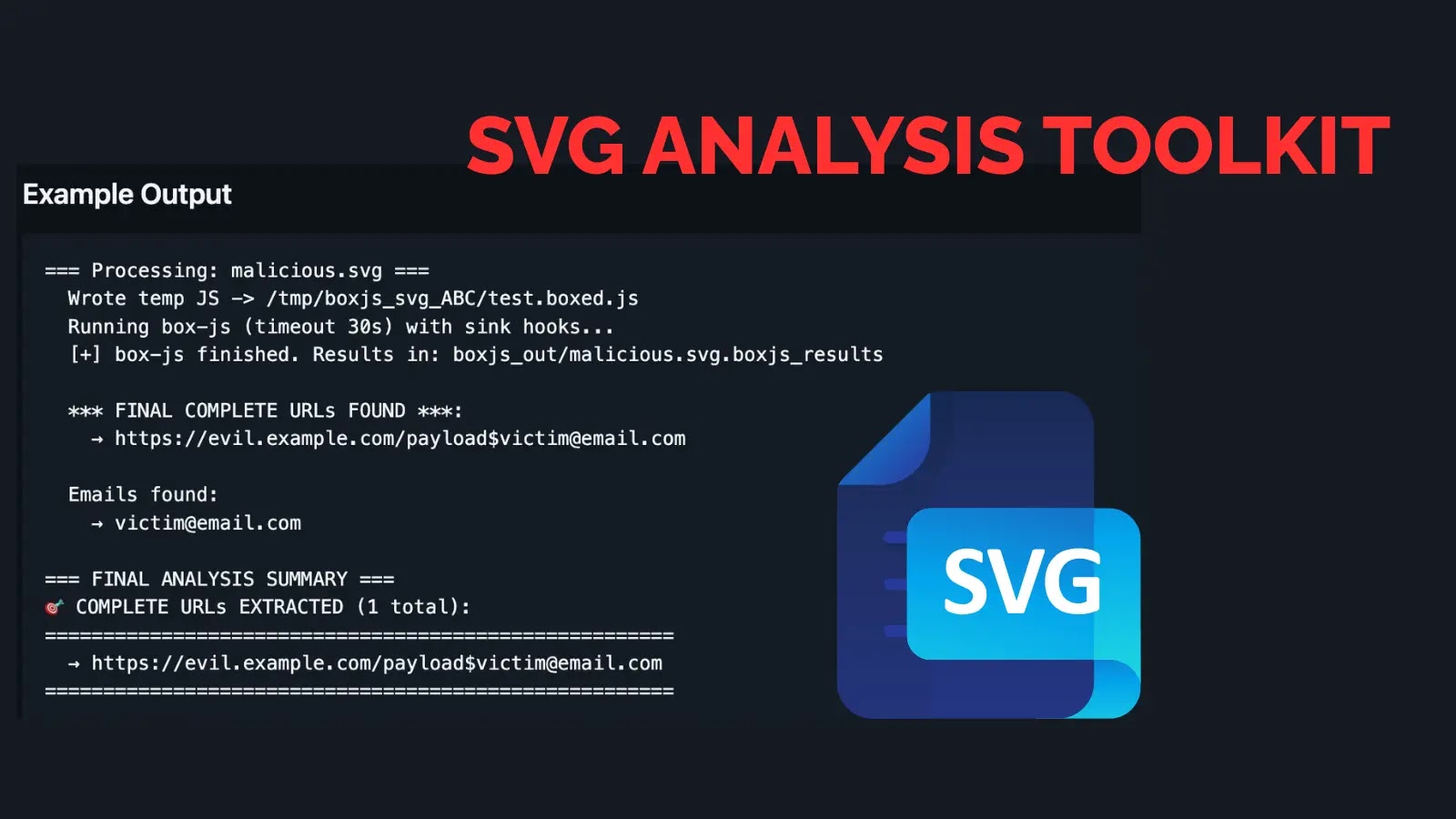
Safe code evaluate represents a vital safety observe that systematically examines software program supply code to establish and remediate safety vulnerabilities earlier than they attain manufacturing environments.
This complete examination serves as a proactive protection mechanism, enabling improvement groups to detect safety flaws early within the software program improvement lifecycle (SDLC) and forestall potential breaches that would compromise delicate information or system integrity.
Not like reactive safety measures comparable to penetration testing, safe code evaluate operates on the supply code degree, offering contextual understanding of vulnerabilities and enabling simpler remediation methods.
Understanding Safe Code Evaluate Fundamentals
Safe code evaluate differs basically from conventional code evaluate by focusing particularly on safety implications fairly than basic code high quality or performance.
The method entails each automated and guide examination methods, with the first goal of making certain software program complies with safety finest practices and trade requirements.
Guide safe code evaluate offers essential perception into the “actual threat” related to insecure code, providing contextual understanding that automated instruments typically miss.
The systematic method encompasses analyzing architectural design, algorithms, information constructions, and coding patterns that would introduce safety vulnerabilities.
This complete analysis helps builders perceive not simply the presence of safety flaws but additionally the underlying patterns and practices that created them, enabling extra knowledgeable decision-making in future improvement efforts.
Static Utility Safety Testing (SAST) Instruments
SAST instruments kind the spine of automated safety code evaluation, analyzing supply code with out executing the applying.
Main SAST options embrace SonarQube for big codebases, Semgrep for fast, light-weight evaluation throughout 30+ languages, and specialised instruments like Gosec for Go builders.
These instruments combine seamlessly into CI/CD pipelines, offering instant suggestions on safety vulnerabilities.
Configuration instance for Semgrep in GitHub Actions:
textname: Semgrep Safety Scan
on: [push, pull_request]
jobs:
semgrep:
runs-on: ubuntu-latest
steps:
– makes use of: actions/checkout@v3
– makes use of: returntocorp/semgrep-action@v1
with:
config: >-
p/security-audit
p/secrets and techniques
Dynamic Utility Safety Testing (DAST) Instruments
DAST instruments complement SAST by testing operating functions for safety vulnerabilities, significantly efficient for detecting enter validation points, authentication issues, and server configuration errors.
OWASP ZAP stands out as a complete open-source DAST resolution, whereas business choices embrace Acunetix and Netsparker.
OWASP ZAP integration in GitLab CI/CD:
textdast:
stage: safety
picture: owasp/zap2docker-stable
script:
– mkdir -p /zap/wrk/
– zap-baseline.py -t $TARGET_URL -g gen.conf -r zap-report.html
artifacts:
studies:
dast: zap-report.html
Software program Composition Evaluation (SCA) Instruments
SCA instruments analyze third-party parts and dependencies for recognized vulnerabilities, offering visibility into the dangers related to open-source software program.
These instruments scan software program dependencies towards vulnerability databases, producing Software program Invoice of Supplies (SBOM) studies that monitor all parts and their safety standing.
Secret Scanning Instruments
Secret scanning prevents publicity of delicate credentials, API keys, and different secrets and techniques in supply code repositories. Instruments like GitLeaks and detect-secrets use common expressions and entropy evaluation to establish doubtlessly uncovered secrets and techniques.
GitLeaks configuration instance:
text- identify: Run Gitleaks
makes use of: actions/checkout@v3
– makes use of: gitleaks/gitleaks-action@v2
env:
GITHUB_TOKEN: ${{ secrets and techniques.GITHUB_TOKEN }}
GITLEAKS_LICENSE: ${{ secrets and techniques.GITLEAKS_LICENSE }}
Part 1: Preparation and Planning
Start by establishing clear evaluate targets that align together with your challenge’s safety necessities. Assemble a various evaluate workforce together with builders, safety specialists, and QA engineers to make sure complete protection.
Put together the evaluate surroundings with applicable entry controls and needed instruments.
Important preparation guidelines:
Outline scope and targets
Safe evaluate surroundings
Set up and configure scanning instruments
Set up communication protocols
Put together evaluate pointers and checklists
Part 2: Automated Evaluation
Execute static evaluation utilizing SAST instruments to establish widespread vulnerabilities and code high quality points. This preliminary automated scan offers a basis for a extra detailed guide evaluate by highlighting areas that require consideration.
Instance C/C++ SAST scan utilizing Flawfinder:
bash# Set up Flawfinder
pip set up flawfinder
# Run safety scan
flawfinder –html –context ./src/ > security-report.html
Part 3: Guide Code Examination
Conduct a scientific guide evaluate specializing in security-critical areas that automated instruments would possibly miss. Pay explicit consideration to authentication mechanisms, enter validation, error dealing with, and information safety implementations.
Key areas for guide evaluate embrace:
Enter Validation: Confirm all exterior inputs are appropriately validated, sanitized, and escaped. Examine for SQL injection vulnerabilities by analyzing dynamic question building:
java// Susceptible code
String question = “SELECT * FROM customers WHERE id = ” + userId;
// Safe various utilizing ready statements
String question = “SELECT * FROM customers WHERE id = ?”;
PreparedStatement stmt = connection.prepareStatement(question);
stmt.setString(1, userId);
Authentication and Authorization: Evaluate session administration, password insurance policies, and entry management mechanisms. Guarantee failure messages don’t leak delicate info and that invalid login makes an attempt are accurately dealt with with charge limiting.
Error Dealing with: Confirm error messages don’t expose system internals or delicate info. Implement complete logging with out disclosing delicate safety information.
Part 4: Vulnerability Evaluation
Systematically categorize recognized vulnerabilities utilizing established frameworks like OWASP Prime 10. Deal with vital points together with:
SQL Injection: Use parameterized queries and saved procedures
Cross-Website Scripting (XSS): Implement output encoding and enter validation
Insecure Direct Object References: Validate authorization for all object entry
Safety Misconfiguration: Evaluate server and utility configurations
Instance of safe enter validation:
pythonimport re
def validate_email(electronic mail):
sample = r’^[a-zA-Z0-9._%+-]+@[a-zA-Z0-9.-]+.[a-zA-Z]{2,}$’
if re.match(sample, electronic mail) and len(electronic mail) <= 254:
return True
return False
def validate_alphanumeric(input_string):
sample = r’^[a-zA-Z0-9]+$’
return bool(re.match(sample, input_string))
Part 5: Third-Get together Part Evaluation
Consider all exterior dependencies utilizing SCA instruments to establish vulnerabilities in third-party libraries and parts. Evaluate licensing compliance and assess the safety posture of exterior dependencies.
Part 6: Testing and Validation
Validate recognized vulnerabilities by means of focused testing, confirming each the presence of safety points and the effectiveness of proposed remediation measures—doc findings with clear remediation steering and precedence ranges.
Integration with Growth Workflow
Implement safe code evaluate as an integral a part of your improvement course of by integrating safety instruments into CI/CD pipelines. Configure automated scans to set off on code commits and pull requests, making certain steady safety evaluation all through the event course of.
Instance GitHub Actions workflow combining a number of safety instruments:
textname: Safety Pipeline
on: [push, pull_request]
jobs:
security-scan:
runs-on: ubuntu-latest
steps:
– makes use of: actions/checkout@v3
– identify: Run SAST
makes use of: github/super-linter@v4
– identify: Secret Scanning
makes use of: trufflesecurity/[email protected]
– identify: Dependency Examine
makes use of: dependency-check/Dependency-Check_Action@foremost
Conclusion
Efficient safe code evaluate requires a mixture of automated instruments and guide experience, supported by clear processes and workforce alignment.
By implementing complete evaluate practices that embody SAST, DAST, SCA, and secret scanning instruments, improvement groups can considerably cut back safety dangers whereas sustaining improvement velocity.
The important thing to success lies in treating safety as an integral a part of the event course of, fairly than an afterthought, making certain that safety concerns are embedded all through the Software program Growth Life Cycle (SDLC).
Common observe of those methods, mixed with steady studying about rising threats and safety finest practices, allows groups to construct extra resilient and safe software program programs.
Discover this Information Fascinating! Comply with us on Google Information, LinkedIn, & X to Get Instantaneous Updates!