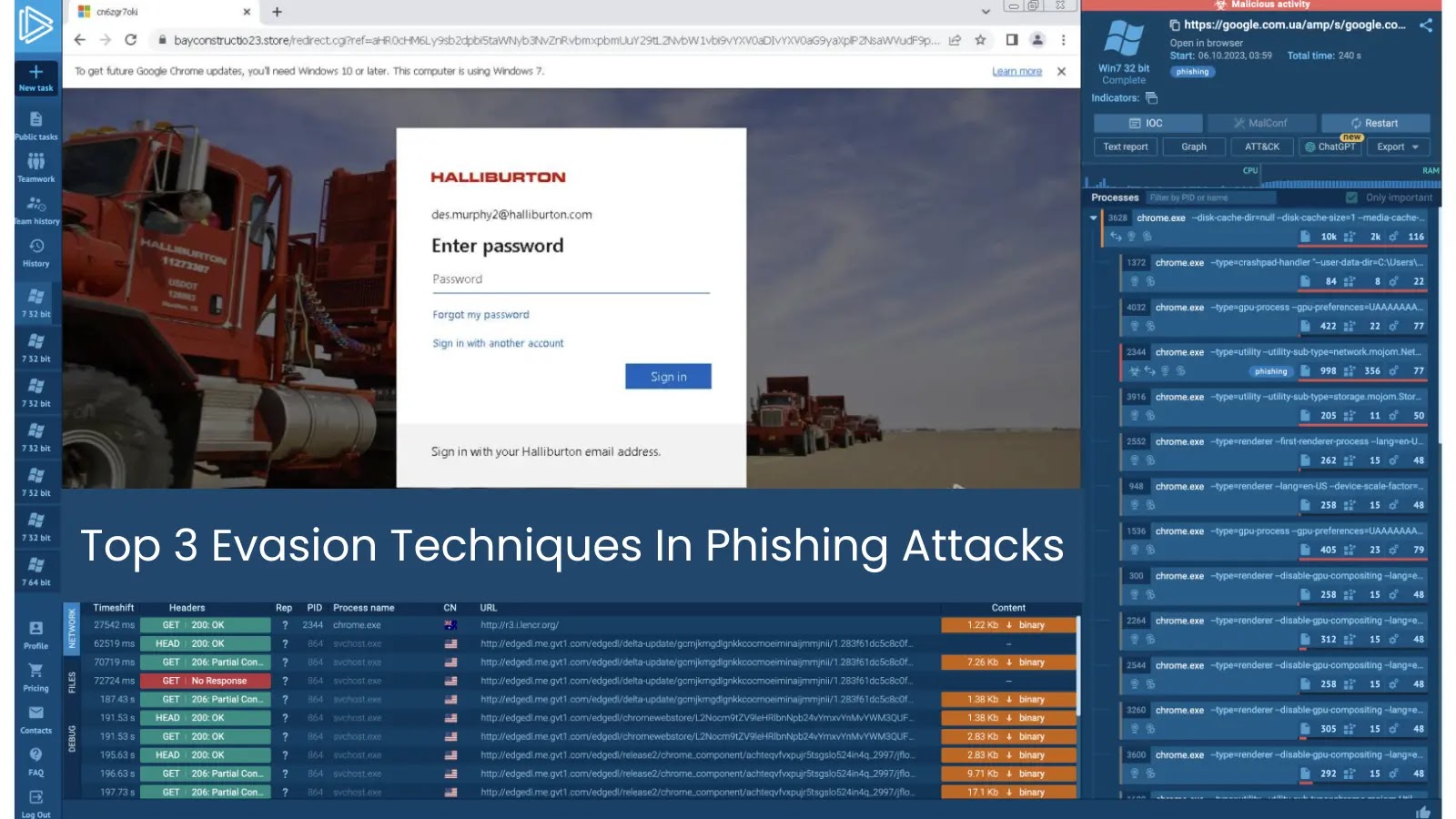
Phishing assaults aren’t what they was once. Hackers now not depend on crude misspellings or sketchy e mail addresses. As an alternative, they use intelligent methods to dodge detection instruments and idiot even cautious customers.
Let’s break down three evasion methods which can be more and more frequent in phishing campaigns with actual examples pulled from latest ANY.RUN sandbox analyses.
1. Hiding Malicious Hyperlinks In QR Codes
As an alternative of sending a direct phishing hyperlink, attackers now embed the hyperlink inside a QR code, sometimes disguised as one thing innocent, like a login immediate, fee discover, or supply replace.
The e-mail would possibly look clear to scanners, however as soon as the consumer scans the code with their telephone, they’re taken straight to a phishing website.
Right here’s why this tactic is so efficient and harmful:
Electronic mail filters don’t “see” the hyperlink – QR codes are photographs, and plenty of scanners don’t decode or analyze their content material. So even when the embedded hyperlink results in a phishing web page, it passes undetected.
Cellular customers are extra weak – Scanning a QR code in your telephone doesn’t present the complete URL like hovering over a hyperlink on a desktop would possibly. Most customers simply faucet and proceed.
The phishing website can look extremely convincing – Victims could also be tricked into getting into credentials, bank card numbers, or 2FA codes, handing attackers entry to enterprise e mail accounts, fee methods, inside networks, private and company information.
Fortunately, there are answers like ANY.RUN sandbox that may deal with precisely this sort of evasive trick.
Whenever you add a phishing e mail or file containing a QR code, the sandbox routinely detects the picture, decodes it, and pulls out the hyperlink.
View evaluation session with QR code
PDF doc with QR code analyzed inside ANY.RUN sandbox
Earlier than beginning the session right here, we enabled the choice “automated interactivity”. This implies the sandbox behaves like an actual consumer.
It scans the QR routinely, opens the embedded hyperlink in a browser and solved CAPTCHA with out your handbook intervention.
ANY.RUN sandbox opening the malicious hyperlink within the browser and fixing CAPTCHA
See via phishing methods in seconds. Entry ANY.RUN together with your 14-day trial and catch what different instruments can’t -> Begin your 14-day trial now
Because of this, the sufferer is redirected to a pretend Microsoft login web page for credentials theft.
Faux Microsoft login web page for credentials theft found inside ANY.RUN
Contained in the sandbox, we will see how your complete assault chain is uncovered inside seconds, from detecting the QR code to opening the phishing web page and labeling the habits.
The decision is evident: malicious exercise is current.
Malicious exercise detected by interactive sandbox
ANY.RUN routinely tags key components of the assault with labels like “QR code,” “phishing,” and even campaign-specific indicators like “Tycoon” when relevant.
This offers analysts immediate context with out the necessity for handbook digging.
By exposing the complete menace movement in actual time, detection time drops from hours to seconds, serving to safety groups:
Rapidly validate suspicious emails or recordsdata
Keep away from chasing false positives
Take motion earlier than a consumer falls for the entice
In brief, what would usually require deep handbook evaluation is now surfaced immediately with proof, labels, and habits insights multi functional place.
2. Geotargeting And Redirect Chains
Some phishing campaigns don’t present their hand straight away. As an alternative of straight exposing malicious content material, they rigorously profile the sufferer first, primarily based on location, browser settings, system particulars, and extra.
If the customer suits the attacker’s goal standards, they’re quietly redirected to a phishing website. If not? They’re despatched some place else, akin to a Tesla web site.
This system, typically utilized in campaigns like Tycoon2FA, helps attackers keep hidden and hyper-targeted.
In a latest Tycoon2FA phishing marketing campaign, this conditional redirection was used to nice impact.
Right here’s the way it labored:
The consumer visits a web page (kempigd[.]com on this case) that quietly runs a fingerprinting script within the background.
It collects particulars like display screen decision, WebGL renderer, plugins, and time zone to find out whether or not the customer matches the attacker’s goal profile.
If the fingerprint doesn’t match, the customer is redirected to a respectable website, on this case, Tesla’s official web site. This helps the phishing web page seem innocent throughout informal or automated inspection.
View Tesla web site rediraction in ANY.RUN
Redirection to a respectable Tesla web site inside ANY.RUN sandbox
If the fingerprint does match, the consumer is silently redirected to a phishing web page designed to steal Microsoft 365 credentials.
View evaluation with Microsoft phishing web page
Redirection to a pretend Microsoft login web page displayed inside ANY.RUN sandbox
ANY.RUN’s Interactive Sandbox lets analysts rapidly change the VM’s IP and different community settings to match the focused geo to detonate the menace.
This type of quick evaluation saves SOC groups hours of handbook investigation by:
Exhibiting precisely how and why a redirect happens
Revealing phishing makes an attempt which can be invisible to straightforward scanning instruments
Confirming the menace with context-specific habits tags
3. CAPTCHA Varieties To Delay Detection
Phishing pages have gotten extra interactive, and never simply to imitate actual websites. Some now use CAPTCHA challenges as a deliberate evasion step.
These types are designed to dam bots, scanners, and automatic safety instruments from reaching the precise malicious content material.
By putting a CAPTCHA on the entrance of the assault chain, menace actors can delay detection and even stop it totally.
Right here’s how this method works:
A phishing e mail or doc results in a seemingly clear hyperlink.
Upon opening, the consumer is introduced with a CAPTCHA problem.
Solely after fixing it does the actual phishing web page load, typically mimicking providers like Microsoft 365.
View the complete sandbox session with CAPTCHA
CAPTCHA problem used to delay entry to the actual phishing website
To simulate the complete movement, we enabled automated interactivity in ANY.RUN. This allowed the sandbox to unravel the CAPTCHA identical to an actual consumer would, uncovering the following stage of the assault with none handbook enter.
As the shape is accomplished, the sufferer is silently redirected to a pretend Microsoft login web page.
Notably, the background picture additionally modifications, a tactic typically used to strengthen the phantasm of authenticity and distract from delicate design flaws.
Faux Microsoft 365 login web page proven after CAPTCHA is bypassed
This kind of superior evaluation is vital as automated instruments often cease at static evaluation. They’ll’t navigate CAPTCHAs, that means they by no means see what comes subsequent. However with ANY.RUN:
The total post-CAPTCHA habits is recorded
Malicious redirects and phishing logic are uncovered
Analysts don’t waste time reproducing the movement manually
With one click on, groups can validate evasive phishing makes an attempt and transfer sooner on response, with out guessing what’s hidden behind that CAPTCHA wall.
Ultimate Ideas: Evasive Techniques, Uncovered In Seconds
As phishing assaults grow to be extra subtle, it’s clear that conventional detection strategies aren’t sufficient.
Methods like QR code obfuscation, geotargeted redirects, and CAPTCHA-based delays are particularly designed to slide previous static scanners and waste analysts’ time.
However with options like ANY.RUN’s interactive sandbox, you don’t should guess or waste hours reproducing complicated assault flows.
Watch evasive phishing techniques unfold in actual time
Routinely extract indicators like malicious hyperlinks, domains, or redirection chains
Detect and tag phishing habits immediately, irrespective of how properly it’s hidden
Cut back investigation time from hours to seconds
Allow your staff to reply sooner, with full confidence within the verdict
Begin your 14-day trial now and expertise what actual visibility into phishing appears to be like like.