A classy wave of Linux malware campaigns is concentrating on cloud environments with rising frequency and complexity, posing vital threats to trendy infrastructure safety.
The emergence of specialised Executable and Linkable Format (ELF) binaries designed particularly for cloud exploitation represents a regarding evolution in menace actor capabilities, as attackers adapt conventional Linux malware for cloud-native environments.
Latest menace intelligence reveals that cloud-based safety alerts have surged by a mean of 388% throughout 2024, whereas 45% of organizations report experiencing elevated superior persistent menace (APT) assaults.
This dramatic escalation coincides with the widespread adoption of cloud infrastructure, the place an estimated 70% to 90% of computational situations function on Linux-based programs, creating an expansive assault floor for malicious actors.
Palo Alto Networks analysts recognized 5 major malware households actively concentrating on cloud environments: NoodleRAT, Winnti, SSHdInjector, Pygmy Goat, and AcidPour.
These refined instruments display steady growth and deployment, with every household receiving at the very least two vital code updates throughout the previous yr and producing over 20 distinctive samples in lively circulation.
The malware strains embody various assault capabilities, together with backdoors, distant entry trojans, knowledge wipers, and vulnerability exploitation binaries particularly engineered for cloud infrastructure compromise.
The menace actors behind these campaigns have demonstrated outstanding adaptability, remodeling present Linux-targeting instruments to use cloud-specific vulnerabilities and infrastructure parts.
Their operations span a number of geographic areas, with documented assaults affecting entities throughout the Asia-Pacific area, together with Thailand, India, Japan, Malaysia, and Taiwan, whereas additionally concentrating on authorities establishments, telecommunications organizations, and significant infrastructure suppliers.
Superior Persistence Via Dynamic Linker Manipulation
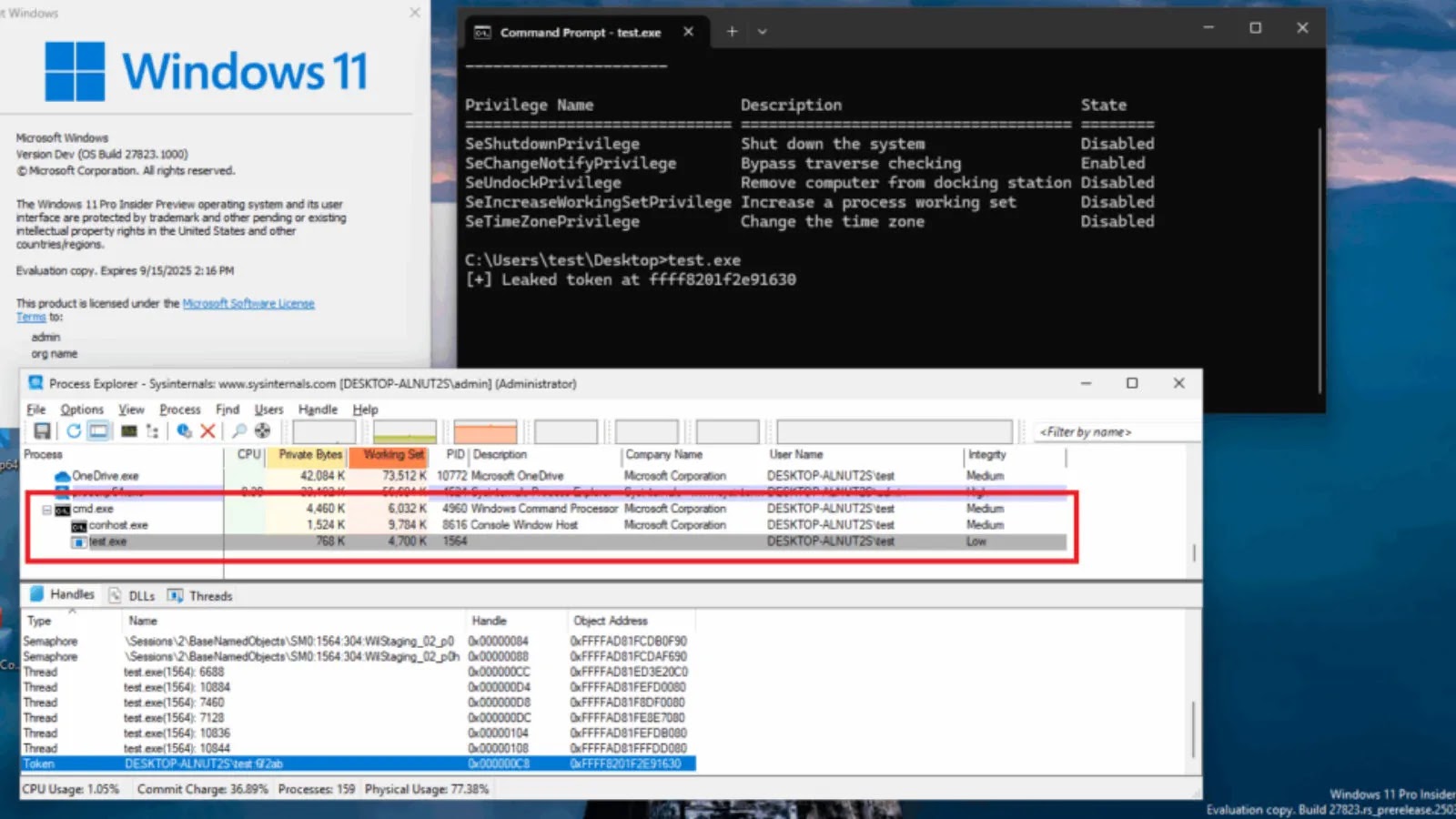
Probably the most regarding facet of those evolving threats lies of their refined persistence mechanisms, significantly the abuse of the LD_PRELOAD surroundings variable for dynamic linker hijacking.
This method permits malware to inject malicious code into reputable system processes with out modifying system binaries, creating practically invisible backdoor entry.
The LD_PRELOAD mechanism permits attackers to specify customized shared libraries that load earlier than customary system libraries.
When exploited, malware like Winnti and SSHdInjector leverage this performance by means of code much like:-
export LD_PRELOAD=”/path/to/malicious/libxselinux.so”
This strategy permits the malware to hook into essential Linux providers, significantly the SSH daemon (sshd), intercepting communications and sustaining persistent entry.
Pygmy Goat exemplifies this method by injecting itself into the SSH daemon and establishing command channels by means of specifically crafted ICMP packets or magic bytes embedded in SSH site visitors.
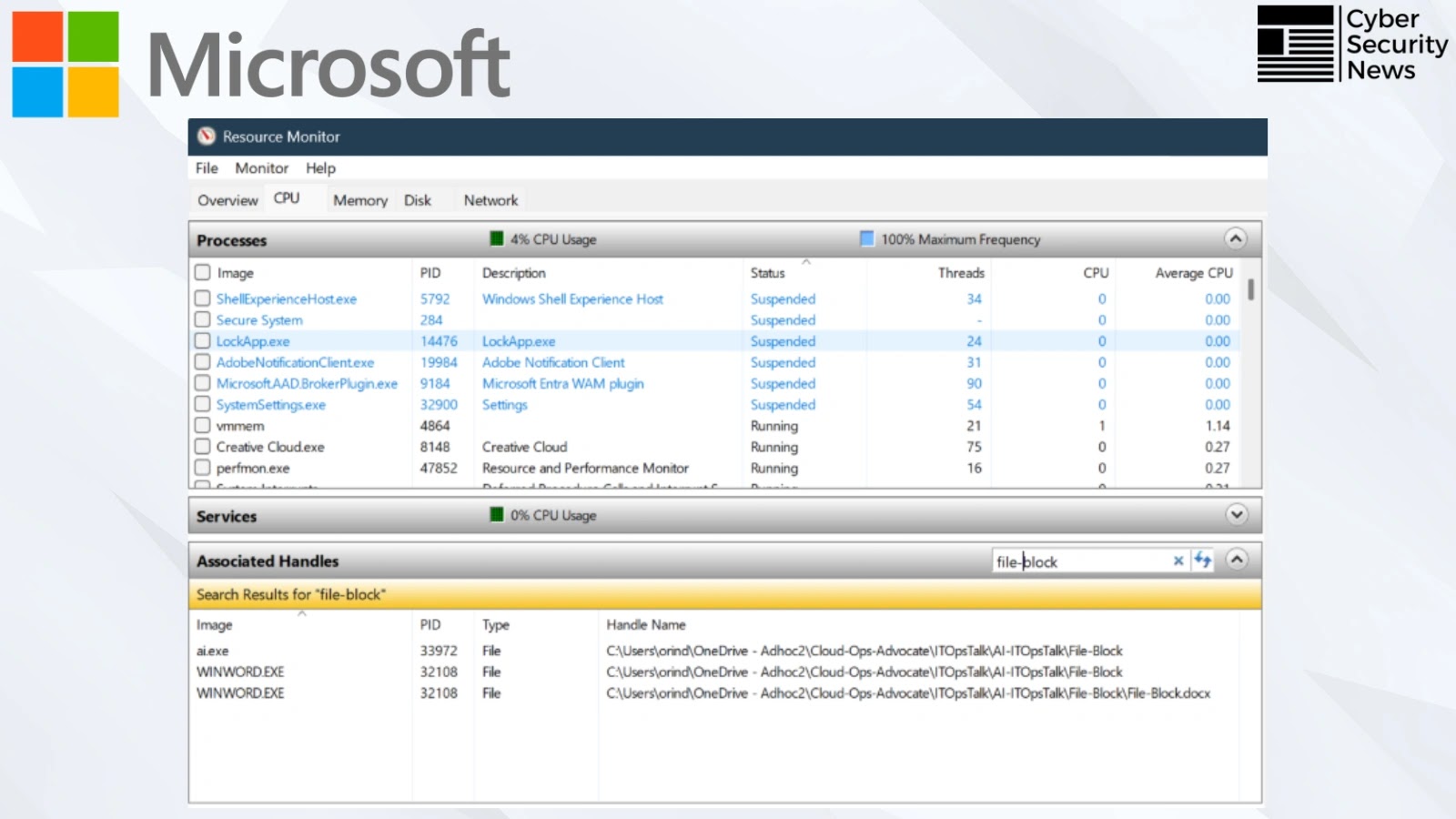
Cortex Cloud ELF Machine Studying execution alert (Supply – Palo Alto Networks)
Machine studying detection programs have confirmed efficient towards these threats, with Palo Alto Networks’ Cortex Cloud reaching 92% accuracy in figuring out malicious ELF binaries throughout all 5 malware households.
ELF machine studying testing scores by share of benign, suspicious or malicious (Supply – Palo Alto Networks)
The Cortex Machine Studying alert system efficiently flagged beforehand unknown ELF binaries, whereas this demonstrates that 61% of examined samples scored above the 0.85 malicious threshold.
Pace up and enrich menace investigations with Risk Intelligence Lookup! -> 50 trial search requests