Jun 17, 2025Ravie LakshmananMalware / Cyber Espionage
A now-patched safety flaw in Google Chrome was exploited as a zero-day by a menace actor referred to as TaxOff to deploy a backdoor codenamed Trinper.
The assault, noticed in mid-March 2025 by Optimistic Applied sciences, concerned using a sandbox escape vulnerability tracked as CVE-2025-2783 (CVSS rating: 8.3).
Google addressed the flaw later that month after Kaspersky reported in-the-wild exploitation in a marketing campaign dubbed Operation ForumTroll focusing on numerous Russian organizations.
“The preliminary assault vector was a phishing e-mail containing a malicious hyperlink,” safety researchers Stanislav Pyzhov and Vladislav Lunin mentioned. “When the sufferer clicked the hyperlink, it triggered a one-click exploit (CVE-2025-2783), resulting in the set up of the Trinper backdoor employed by TaxOff.”
The phishing e-mail is claimed to have been disguised as an invite to the Primakov Readings discussion board – the identical lure detailed by Kaspersky – urging customers to click on on a hyperlink that led to a faux web site internet hosting the exploit.
TaxOff is the title assigned to a hacking group that was first documented by the Russian cybersecurity firm in late November 2024 as focusing on home authorities companies utilizing authorized and finance-related phishing emails to ship Trinper.
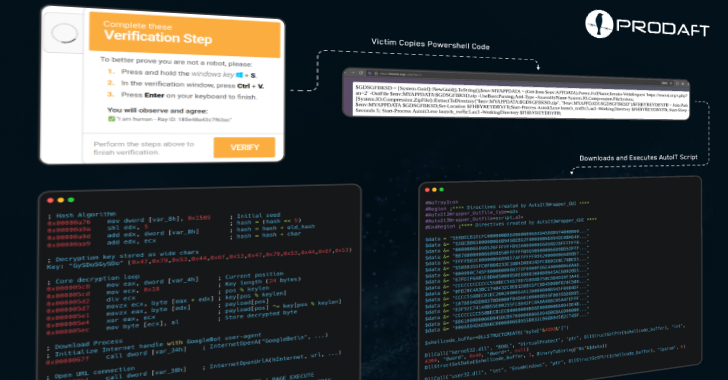
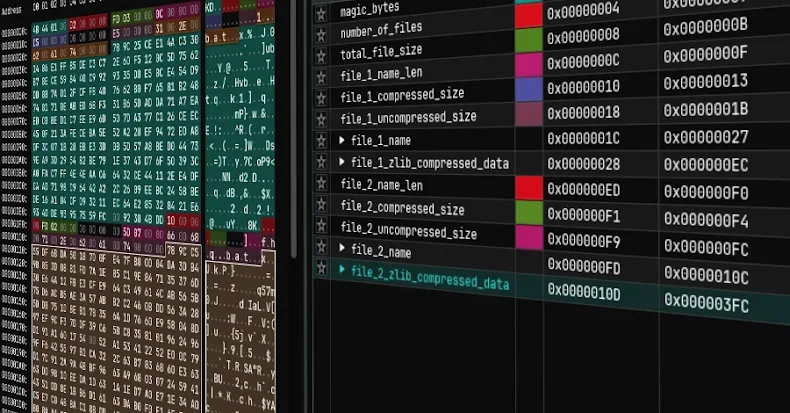
Written in C++, the backdoor makes use of multithreading to seize sufferer host info, file keystrokes, collect information matching particular extensions (.doc, .xls, .ppt, .rtf, and .pdf), and set up a reference to a distant server to obtain instructions and exfiltrate the outcomes of the execution.
The directions despatched from the command-and-control (C2) server lengthen the implant’s performance, permitting it to learn/write information, run instructions utilizing cmd.exe, launch a reverse shell, change listing, and shutdown itself.
“Multithreading supplies a excessive diploma of parallelism to cover the backdoor whereas retaining the flexibility to gather and exfiltrate knowledge, set up extra modules, and preserve communications with C2,” Lunin famous on the time.
Optimistic Applied sciences mentioned its investigation into the mid-March 2025 intrusion led to the invention of one other assault courting again to October 2024 that additionally commenced with a phishing e-mail, which presupposed to be an invite to a world convention known as “Safety of the Union State within the fashionable world.”
The e-mail message additionally contained a hyperlink, which downloaded a ZIP archive file containing a Home windows shortcut that, in flip, launched a PowerShell command to finally serve a decoy doc whereas additionally dropping a loader liable for launching the Trinper backdoor by way of the open-source Donut loader. A variation of the assault has been discovered to swap out the Donut loader in favor of Cobalt Strike.
This assault chain, per the corporate, shares a number of tactical similarities with that of one other hacking group tracked as Team46, elevating the chance that the 2 menace exercise clusters are one and the identical.
Curiously, one other set of phishing emails despatched by the Team46 attackers a month earlier than claimed to be from Moscow-based telecom operator Rostelecom, alerting recipients of supposed upkeep outages final yr.
These emails included a ZIP archive, which embedded a shortcut that launched a PowerShell command to deploy a loader that had been beforehand used to ship one other backdoor in an assault focusing on an unnamed Russian firm within the rail freight trade.
The March 2024 intrusion, detailed by Physician Internet, is notable for the truth that one of many payloads weaponized a DLL hijacking vulnerability within the Yandex Browser (CVE-2024-6473, CVSS rating: 8.4) as a zero-day to obtain and execute unspecified malware. It was resolved in model 24.7.1.380 launched in September 2024.
“This group leverages zero-day exploits, which permits it to penetrate safe infrastructures extra successfully,” the researchers mentioned. “The group additionally creates and makes use of refined malware, implying that it has a long-term technique and intends to take care of persistence on the compromised programs for an prolonged interval.”
Discovered this text fascinating? Observe us on Twitter and LinkedIn to learn extra unique content material we put up.