Phishing stays one of the crucial efficient methods attackers infiltrate company environments. At the moment’s phishing campaigns are not simply poorly written emails with apparent purple flags.
They’re refined, well-disguised, and tailor-made to use belief in on a regular basis instruments your groups use.
From fileless redirections to abuse of collaboration platforms like Notion, these new ways are designed to bypass electronic mail gateways, evade conventional detection instruments, and attain your workers the place they’re most susceptible.
Listed here are 5 rising phishing methods companies ought to watch carefully in 2025 and how one can detect them sooner.
1. SVG Attachments That Look Innocent
One of many latest tips within the phishing playbook: malicious SVG information. These light-weight vector photos could be embedded with JavaScript and designed to appear to be icons or logos.
When opened, they usually lead customers to phishing portals or mechanically redirect them to credential harvesting pages.
As a result of SVGs don’t at all times elevate purple flags throughout electronic mail filtering or antivirus scans, they’re a intelligent method to bypass conventional detection.
Nonetheless, interactive sandboxes like ANY.RUN enable safety groups to open SVG attachments in a protected, remoted surroundings and observe the complete assault chain.
View evaluation session with malicious SVG attachment
SVG attachment analyzed inside ANY.RUN sandbox
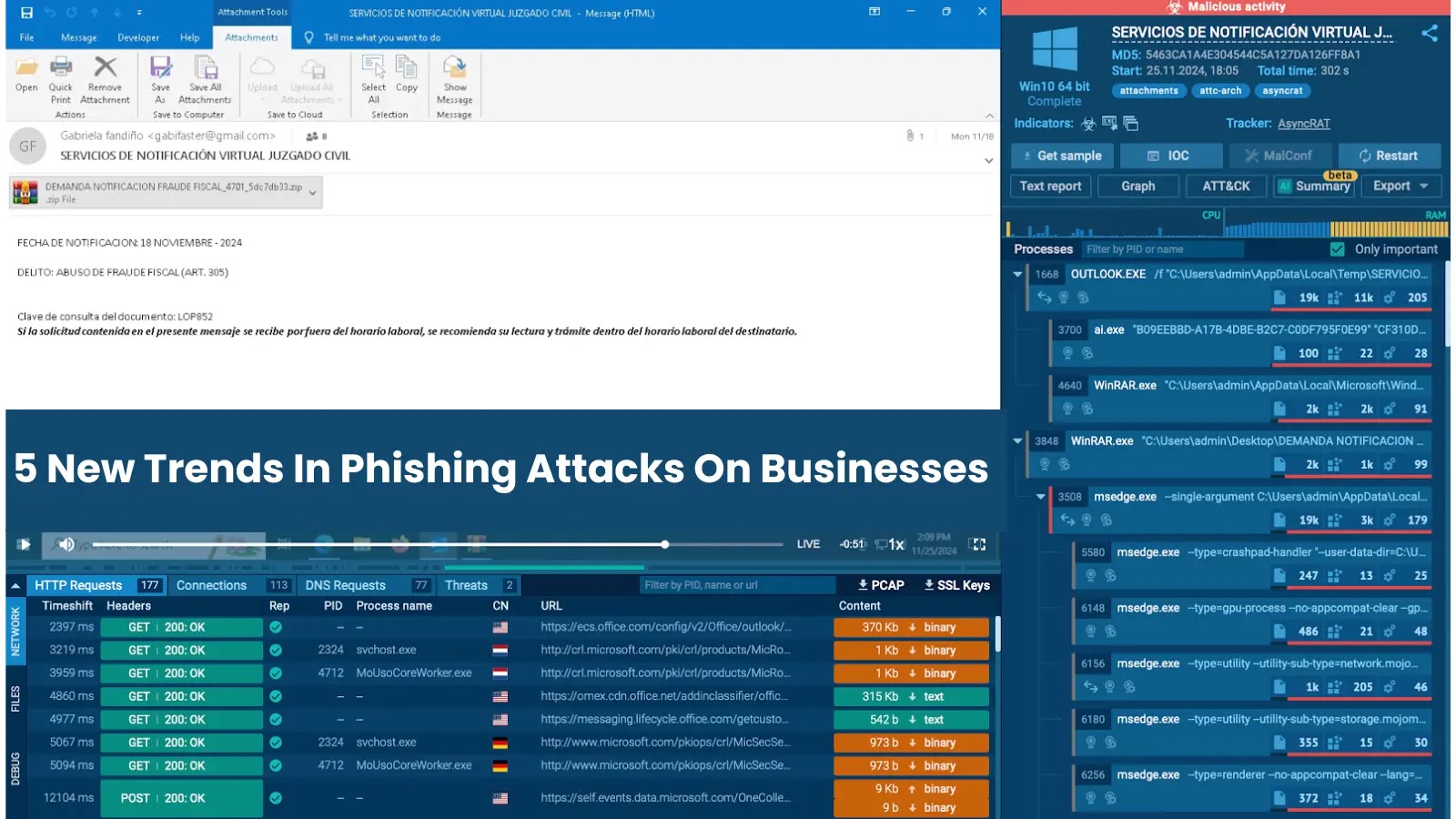
Within the following evaluation session, a phishing electronic mail contained an SVG attachment. Opening the SVG revealed a obtain hyperlink to a malicious PDF file.
As soon as downloaded and opened utilizing a password offered within the electronic mail, the PDF dropped an AsyncRAT payload onto the system.
AsyncRAT detected by interactive sandbox
This type of deep behavioural visibility is what makes sandboxes like ANY.RUN essential for safety groups: it replicates real-world person actions and exposes threats that static instruments miss, serving to you detect and perceive assaults earlier than they escalate into breaches.
Lower investigation time, enhance detection accuracy, and provides your group the visibility they should cease phishing threats quick – -> Attempt ANY.RUN now
2. HTML Recordsdata That Act Like Legit Internet Pages
Phishing actors are more and more utilizing HTML attachments to impersonate login portals, invoices, or authorized paperwork.
These information open domestically within the person’s browser, permitting them to bypass net filters and reputation-based detections, making them a stealthy alternative for attackers.
On this ANY.RUN evaluation session, we see precisely how this tactic performs out:
PDF file posing as an official summons from the South African Judiciary uncovered inside ANY.RUN sandbox
The sufferer receives a PDF file posing as an official summons from the South African Judiciary.
Contained in the PDF, there’s a call-to-action button labeled “PREVIEW YOUR SUMMON DOCUMENT HERE.”
Clicking it opens an embedded HTML file disguised as a Microsoft 365 login web page; a faux kind constructed to steal company electronic mail credentials.
Malicious HTML file to steal Microsoft 365 credentials
These assaults don’t want a stay malicious area; they exploit person belief, file habits, and urgency, usually with out ever touching a flagged IP or URL.
You possibly can see how sandboxes like ANY.RUN give safety groups the context they want, not simply to see that an HTML file is suspicious, however to know precisely the way it tips customers and what it’s making an attempt to steal.
That stage of perception turns reactive alerts into knowledgeable motion.
3. Redirect Chains That Adapt To The Sufferer
A few of the most harmful phishing campaigns don’t depend on apparent lures or instant traps.
As an alternative, they use conditional redirection; a stealthy method the place the phishing web site decides in actual time whether or not or to not expose its malicious content material.
The concept is easy however efficient: profile the customer first and solely serve the phishing payload in the event that they meet sure standards.
If not, ship them someplace fully innocent, like a brand-name web site or a generic touchdown web page.
This enables the phishing infrastructure to stay operational longer, keep away from automated scanners, and scale back the chance of takedowns.
We noticed this tactic in motion throughout a latest Tycoon2FA phishing marketing campaign:
The person visits a web page like kempigd[.]com, which runs a fingerprinting script within the background.
It gathers system knowledge, like browser kind, display decision, time zone, and GPU particulars to find out whether or not the customer matches the attacker’s goal profile.
If there’s no match, the person is quietly redirected to a respectable web site (on this case, Tesla’s official web site) to throw off suspicion.
View Tesla web site rediraction in ANY.RUN
Redirection to Tesla.com inside ANY.RUN sandbox
If the system fingerprint does match, the web page redirects to a faux Microsoft 365 login portal constructed to steal company credentials.
View evaluation with Microsoft phishing web page
Redirection to a faux Microsoft login web page
With options like ANY.RUN’s interactive sandbox, it turns into simple to hint each stage of complicated phishing assaults, from profiling scripts to closing payload supply.
Analysts can alter VM settings like IP, language, and placement to duplicate the precise situations attackers are focusing on.
This stage of management is very priceless for SOC groups underneath stress to reply quick.
As an alternative of spending hours making an attempt to breed suspicious habits, they get clear, instant visibility into how the assault works; what’s triggered, what’s downloaded, and what occurs subsequent.
4. LinkedIn Web site Spoofing
LinkedIn has change into a key goal in phishing campaigns not simply due to its person base, however due to the belief it carries.
Attackers know {that a} LinkedIn login web page doesn’t often elevate suspicion. That makes it the proper disguise for credential theft.
On this evaluation session, attackers created a pixel-perfect clone of LinkedIn’s login web page and hosted it on a compromised Brazilian area (megarapidaambiental[.]com[.]br).
View evaluation session with spoofed LinkedIn web page
A spoofed LinkedIn login web page inside ANY.RUN’s sandbox surroundings
At a look, the web page appears to be like respectable, even the “Proceed with Microsoft” and “Check in with Google” buttons are there, together with LinkedIn’s branding and prompts.
What provides it away is the URL, not the content material. However most customers received’t test that. And lots of automated programs received’t flag it, particularly when the web page is hosted on a low-reputation however clean-looking area.
With sandboxes like ANY.RUN, safety groups can safely discover and work together with these spoofed environments, inspecting community habits, kind submissions, and hidden scripts in actual time.
5. Phishing Pages Hosted On Notion
Phishing doesn’t at all times depend on shady domains or poorly constructed pages. The truth is, a few of the most misleading assaults are actually hosted on respectable platforms like Notion.
These providers are designed for collaboration, not safety, which makes them a great cowl for risk actors trying to host malicious content material with out elevating purple flags.
In a single ANY.RUN evaluation session, a Notion-hosted web page, written in Italian, was used to lure victims into clicking a hyperlink to a faux Microsoft OneNote login.
Faux Microsoft OneNote login web page analyzed inside ANY.RUN sandbox
From there, credentials had been harvested by a spoofed login kind, whereas the sufferer’s IP tackle was silently collected and exfiltrated through a Telegram bot embedded within the phishing script.
After submission, the sufferer was redirected to the true OneNote login web page to keep away from suspicion.
With ANY.RUN’s interactive sandbox, SOC groups can safely work together with phishing flows hosted on trusted platforms, hint knowledge exfiltration routes like Telegram bots, and acquire real-time intelligence to enhance detection and response workflows.
Cease Phishing Earlier than It Turns Into A Breach
Phishing assaults aren’t simply hiding in emails anymore. They’re embedded in trusted platforms, disguised as login pages, and triggered solely when the situations are good.
ANY.RUN helps safety groups transfer sooner, reply smarter, and keep forward of threats:
Quicker detection and triage due to real-time, behavior-based evaluation
Fewer false positives by full visibility into how phishing assaults unfold
Stronger collaboration between analysts, risk hunters, and managers with shared classes and reporting
Higher risk intel with IOCs, metadata, and full assault chains captured mechanically
Proactive response by uncovering evasive methods that conventional instruments miss
Begin your 14-day trial and provides your group the readability and velocity they should cease phishing assaults earlier than they unfold.