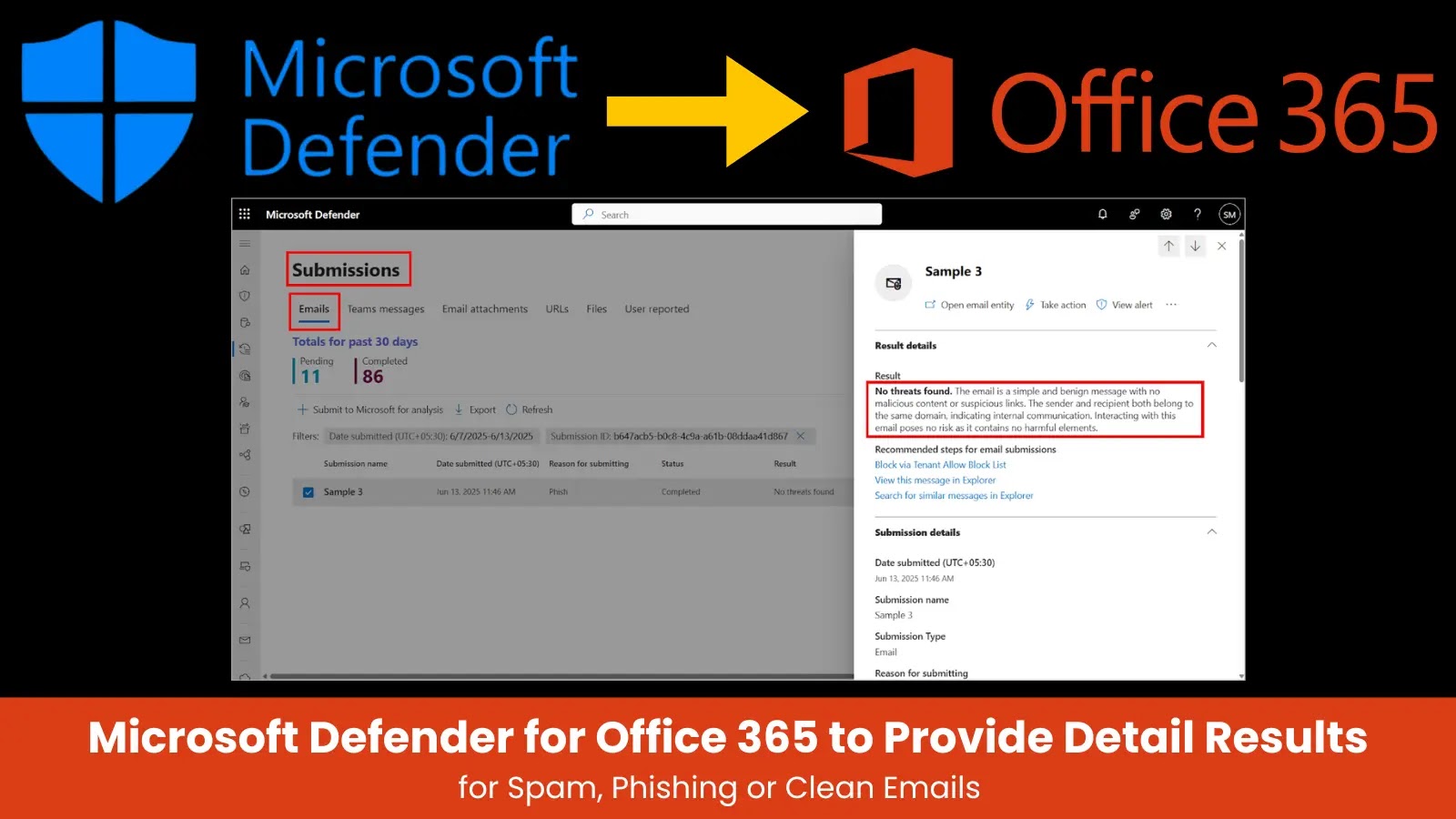
Apache SeaTunnel, the extensively used distributed information integration platform, has disclosed a major safety vulnerability that permits unauthorized customers to execute arbitrary file learn operations and deserialization assaults via its RESTful API interface.
The vulnerability, tracked as CVE-2025-32896 and reported on April 12, 2025, impacts a number of variations of the platform and has been labeled with reasonable severity.
Apache SeaTunnel RCE Vulnerability
The safety flaw impacts Apache SeaTunnel variations 2.3.1 via 2.3.10, creating a considerable publicity window for organizations using these variations in manufacturing environments.
The vulnerability stems from inadequate entry controls within the platform’s RESTful API-v1 implementation, particularly focusing on the /hazelcast/relaxation/maps/submit-job endpoint.
This endpoint, designed for job submission performance, lacks correct authentication mechanisms, permitting malicious actors to use the system with out legitimate credentials.
Safety researcher Owen Amadeus found and reported this vulnerability, highlighting how unauthorized customers can bypass safety controls to entry delicate system sources.
The technical nature of this flaw includes the manipulation of MySQL connection parameters, the place attackers can inject malicious payloads via URL parameters to realize their aims.
This assault vector is especially regarding as a result of it combines two vital safety dangers: arbitrary file entry and deserialization vulnerabilities, which may result in distant code execution eventualities.
The exploitation mechanism facilities across the manipulation of database connection strings throughout the SeaTunnel job submission course of.
Attackers can craft specifically designed MySQL URLs containing further parameters that set off each arbitrary file learn operations and Java deserialization assaults. The susceptible endpoint /hazelcast/relaxation/maps/submit-job processes these malicious requests with out correct validation or authentication checks.
The deserialization part of this assault is especially harmful, as it will possibly permit attackers to execute arbitrary code on the goal system.
By submitting crafted serialized objects via the job submission interface, malicious actors can probably achieve full management over the affected SeaTunnel occasion.
Any such vulnerability exploits Java’s object serialization mechanism, the place untrusted information may be deserialized into executable code, bypassing conventional safety boundaries.
Danger FactorsDetailsAffected ProductsApache SeaTunnel variations 2.3.1 via 2.3.10ImpactRemote Code Execution (RCE)Exploit Stipulations– Community entry to SeaTunnel instance- API-v1 enabled (default)- Absence of HTTPS two-way authenticationCVSS 3.1 Score8.2 (Excessive)
Remediation Steps
The Apache SeaTunnel improvement crew has addressed this vulnerability in model 2.3.11, implementing complete safety enhancements to stop unauthorized entry.
Organizations working affected variations ought to instantly improve to the newest launch to mitigate potential safety dangers. The repair consists of enhanced authentication mechanisms and enter validation procedures.
Past model upgrades, directors are strongly suggested to implement further safety measures.
The Apache crew recommends enabling RESTful API-v2 performance, which incorporates improved safety controls and authentication frameworks.
Moreover, implementing HTTPS two-way authentication gives a further safety layer by making certain mutual certificates validation between shoppers and servers.
Are you from SOC/DFIR Groups! – Work together with malware within the sandbox and discover associated IOCs. – Request 14-day free trial