Abstract
1. Redirection controls disable clipboard, drive, USB, and printer entry by default to forestall information exfiltration and malware injection.
2. Virtualization-based safety permits VBS, Credential Guard, and HVCI on Home windows 11 Cloud PCs to fortify towards credential theft and kernel exploits.
3. Selective implementation requires IT admins to manually override settings through Intune or GPOs for mandatory redirections, with USB mice/keyboards remaining unaffected.
4. Phased administrative deployment begins late 2025 through Intune insurance policies, requiring guide override of defaults for mandatory redirections.
Microsoft unveiled vital safety enhancements for Home windows 365 Cloud PCs on June 18, 2025, introducing new default configurations that prioritize information safety and system integrity.
The updates embody disabling clipboard, drive, USB, and printer redirections by default, whereas enabling superior security measures like virtualization-based safety (VBS), Credential Guard, and hypervisor-protected code integrity (HVCI) for Home windows 11 gallery pictures.
Stricter Redirection Insurance policies to Forestall Information Exfiltration
Essentially the most notable change includes disabling 4 key redirection sorts by default for all newly provisioned and reprovisioned Home windows 365 Cloud PCs.
Clipboard, drive, USB, and printer redirections might be robotically disabled to attenuate the dangers of knowledge exfiltration and malware injection.
This security-first strategy aligns with Microsoft’s Safe Future Initiative (SFI), which emphasizes having safety protections enabled and enforced by default.
The rollout will start steadily within the second half of 2025, with IT directors receiving advance notification by means of banners displayed within the Microsoft Intune Admin Middle.
These banners will seem on provisioning coverage, particular person machine motion, and bulk motion pages, offering hyperlinks to documentation for overriding the default settings by means of Intune machine configuration insurance policies or Group Coverage Objects (GPOs).
IT directors who want to revive redirection capabilities can handle settings by means of two major strategies: the Intune Settings Catalog or conventional GPO configurations.
The system is designed to permit Intune to sync and implement administrator-defined settings after preliminary provisioning, overriding the restrictive defaults when insurance policies are correctly configured.
Superior Virtualization Safety Options
Since Could 2025, Microsoft has been robotically enabling three essential safety applied sciences on new Home windows 365 Cloud PCs working Home windows 11 gallery pictures.
Virtualization-based safety (VBS) creates a safe reminiscence enclave utilizing {hardware} virtualization to guard essential system processes from superior threats and malicious exploits.
Credential Guard leverages VBS infrastructure to safe authentication credentials, considerably decreasing the danger of credential theft and lateral motion assaults inside enterprise networks.
In the meantime, hypervisor-protected code integrity (HVCI), often known as reminiscence integrity, ensures solely verified code can execute on the kernel stage, stopping malicious exploits from compromising system integrity.
The brand new safety defaults will have an effect on person workflows, notably for organizations that beforehand relied on seamless file transfers and machine connectivity between native machines and Cloud PCs.
Microsoft recommends that IT groups talk these adjustments proactively to finish customers and set up clear procedures for requesting redirection enablement when enterprise necessities necessitate particular connectivity choices.
For Home windows 365 Frontline Cloud PCs working in shared mode, the implementation varies relying on the reprovisioning technique used.
Direct reprovisioning from the machine overview web page will keep current coverage configurations, whereas reprovisioning from the provisioning coverage web page will apply the brand new restrictive defaults.
This distinction permits directors to keep up granular management over safety posture throughout totally different deployment situations.
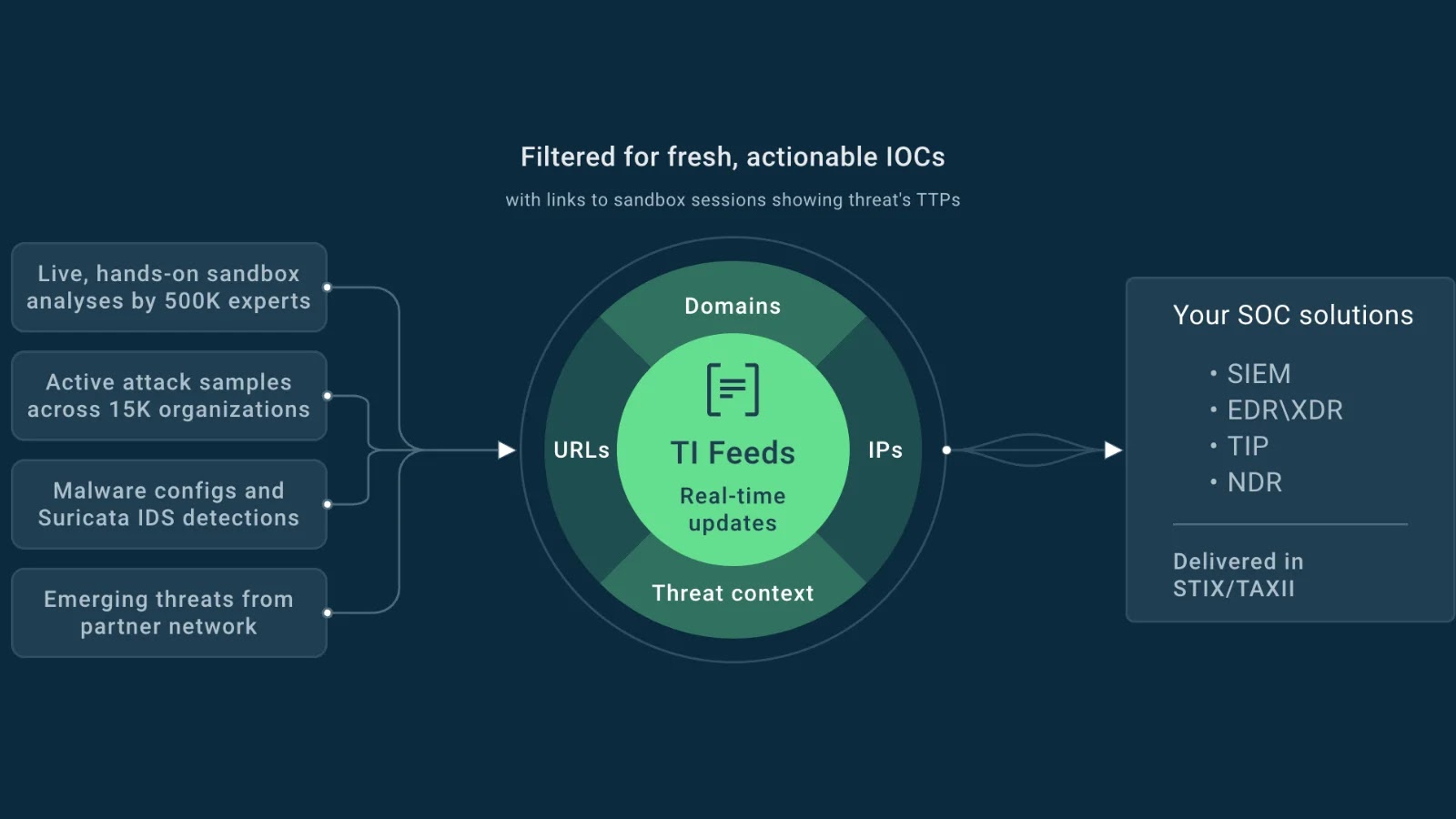
Are you from SOC/DFIR Groups! – Work together with malware within the sandbox and discover associated IOCs. – Request 14-day free trial