Tech assist scammers are leveraging an unsophisticated however environment friendly methodology to trick unsuspecting customers into calling them, by ‘hacking’ the web sites of main firms to show the scammers’ cellphone quantity.
The marketing campaign, analyzed by antimalware agency Malwarebytes, entails the usage of sponsored adverts on Google. The attackers pay for adverts that time individuals who search for 24/7 assist to the websites of firms reminiscent of Apple, Microsoft, HP, Fb, Netflix, Financial institution of America, and PayPal.
Nevertheless, in contrast to in different campaigns involving sponsored adverts, the cybercriminals usually are not attempting to lure customers to pretend web sites set as much as mimic those of the focused firms.
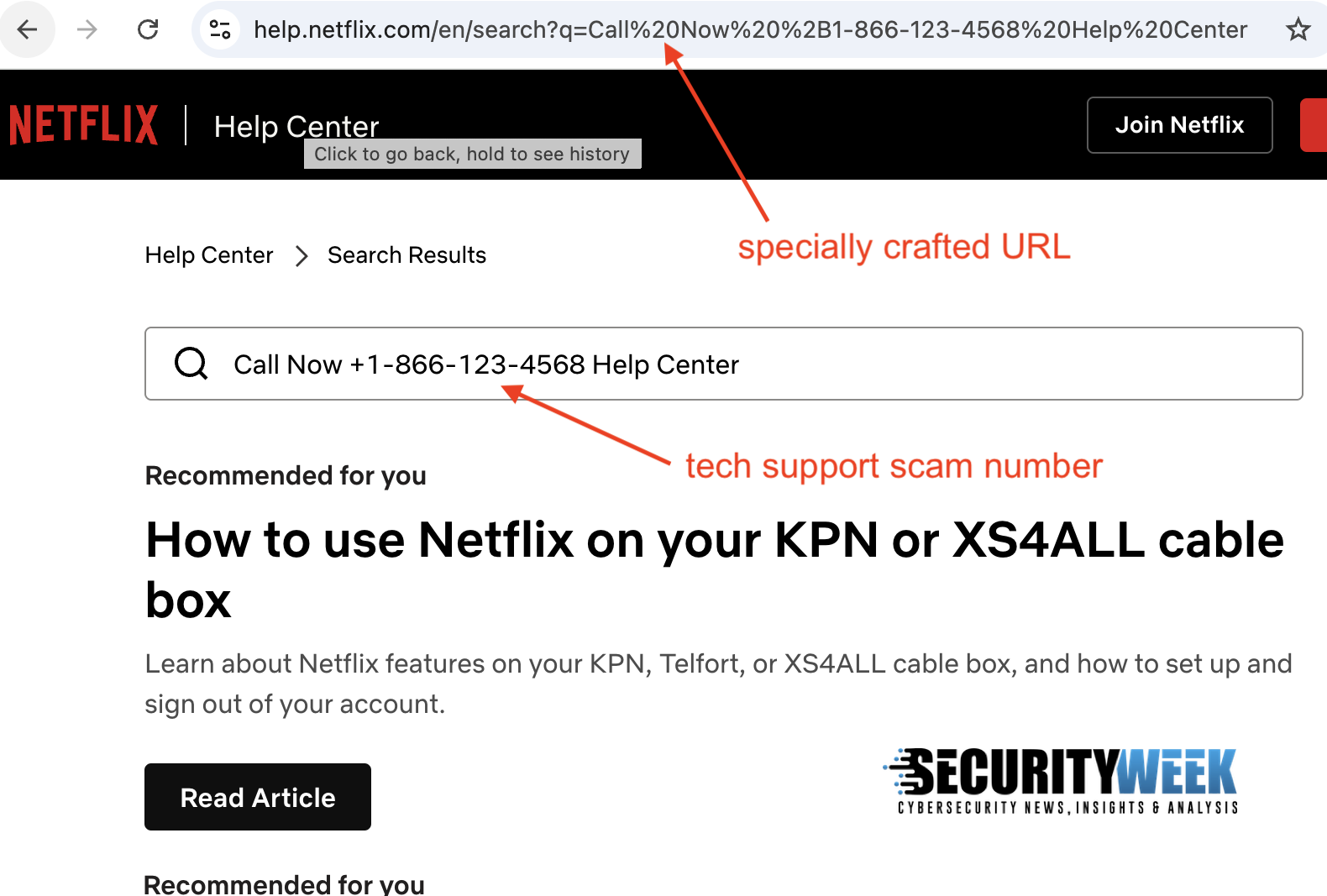
As an alternative, the sponsored hyperlinks level to the professional web site, particularly assist middle, assist or store pages that embrace search performance.
The URLs of those pages have been crafted in a method that triggers what Malwarebytes calls search parameter injection, inflicting the web page to show the tech assist rip-off cellphone quantity within the search bar or search outcomes.
“The browser tackle bar will present that of the professional website and so there’s no purpose for suspicion. Nevertheless, the knowledge the customer sees might be deceptive, as a result of the search outcomes have been poisoned to show the scammer’s quantity prominently in what seems like an official search outcome,” defined Malwarebytes Senior Director of Analysis Jerome Segura.
“As soon as the quantity is named, the scammers will pose because the model with the intention of getting their sufferer at hand over private knowledge or card particulars, and even enable distant entry to their pc. Within the case of Financial institution of America or PayPal, the scammers need entry to their sufferer’s monetary account to allow them to empty it of cash,” Segura added.
In among the examples seen by Malwarebytes, it’s simpler to find out that the scammers’ cellphone quantity is displayed as a search outcome, making it much less seemingly for customers to fall for it. Commercial. Scroll to proceed studying.
Within the case of the web sites of firms reminiscent of Apple and Netflix, it’s much less clear that the tech assist rip-off quantity doesn’t belong on the web page.
Associated: Why Scamming Can’t Be Stopped—However It Can Be Managed
Associated: How Scammers Are Utilizing AI to Steal School Monetary Support
Associated: Tech Help Companies Comply with $26M FTC Settlement Over Faux Providers