Jun 26, 2025Ravie LakshmananThreat Intelligence / Ransomware
Cybersecurity researchers are calling consideration to a collection of cyber assaults focusing on monetary organizations throughout Africa since at the least July 2023 utilizing a mixture of open-source and publicly out there instruments to take care of entry.
Palo Alto Networks Unit 42 is monitoring the exercise below the moniker CL-CRI-1014, the place “CL” refers to “cluster” and “CRI” stands for “legal motivation.”
It is suspected that the tip purpose of the assaults is to acquire preliminary entry after which promote it to different legal actors on underground boards, making the risk actor an preliminary entry dealer (IAB).
“The risk actor copies signatures from respectable purposes to forge file signatures, to disguise their toolset and masks their malicious actions,” researchers Tom Fakterman and Man Levi mentioned. “Risk actors usually spoof respectable merchandise for malicious functions.”
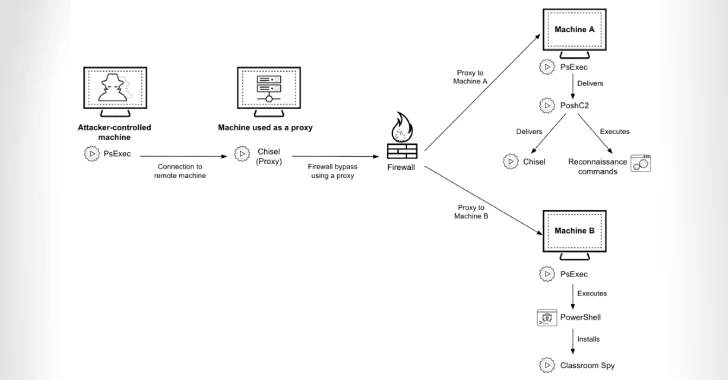
The assaults are characterised by the deployment of instruments like PoshC2 for command-and-control (C2), Chisel for tunneling malicious community visitors, and Classroom Spy for distant administration.
The precise technique the risk actors use to breach goal networks isn’t clear. As soon as a foothold is obtained, the assault chains have been discovered to deploy MeshCentral Agent and later Classroom Spy to commandeer the machines, after which drop Chisel to bypass firewalls and unfold PoshC2 to different Home windows hosts on the compromised community.
To sidestep detection efforts, the payloads are handed off as respectable software program, utilizing the icons of Microsoft Groups, Palo Alto Networks Cortex, and Broadcom VMware Instruments. PoshC2 is persevered on the programs utilizing three completely different strategies –
Establishing a service
Saving a Home windows shortcut (LNK) file to the device within the Startup folder
Utilizing a scheduled activity below the title “Palo Alto Cortex Companies”
In some incidents noticed by the cybersecurity firm, the risk actors are mentioned to have stolen consumer credentials and used them to arrange a proxy utilizing PoshC2.
“PoshC2 can use a proxy to speak with a command-and-control (C2) server, and it seems that the risk actor tailor-made a number of the PoshC2 implants particularly for the focused setting,” the researchers famous.
This isn’t the primary time PoshC2 has been utilized in assaults aimed toward monetary companies in Africa. In September 2022, Test Level detailed a spear-phishing marketing campaign dubbed DangerousSavanna that focused monetary and insurance coverage firms situated in Ivory Coast, Morocco, Cameroon, Senegal, and Togo to ship Metasploit, PoshC2, DWservice, and AsyncRAT.
The disclosure comes as Trustwave SpiderLabs make clear a brand new ransomware group known as Dire Wolf that has already claimed 16 victims throughout the U.S., Thailand, Taiwan, Australia, Bahrain, Canada, India, Italy, Peru, and Singapore since its emergence final month. The highest focused sectors are expertise, manufacturing, and monetary companies.
Evaluation of the Dire Wolf locker has revealed that it is written in Golang, and comes with capabilities to disable system logging, terminate a hard-coded record of 75 companies and 59 purposes, and inhibit restoration efforts by deleting shadow copies.
“Though no preliminary entry, reconnaissance or lateral motion strategies utilized by Dire Wolf are recognized at this level, organizations shall observe good safety practices in addition to allow monitoring for the strategies revealed on this evaluation,” the corporate mentioned.
Discovered this text attention-grabbing? Comply with us on Twitter and LinkedIn to learn extra unique content material we publish.