Microsoft has launched RIFT (Rust Identification and Operate Tagging), a groundbreaking open-source software designed to assist cybersecurity analysts determine and analyze malware hid inside Rust binaries.
Abstract
1. RIFT – Microsoft’s open-source software to research Rust-based malware like BlackCat and Hive ransomware.
2. Rust binaries have 10,000+ capabilities, making conventional malware evaluation tough.
3. Three-part system with IDA Professional integration for metadata extraction and signature era.
4. Efficiently examined on actual malware, it helps analysts deal with malicious code solely.
The cybersecurity group has witnessed a major shift towards Rust-based malware growth over the previous 5 years.
Notable examples embody the BlackCat ransomware in December 2021, adopted by Hive ransomware being rewritten in Rust in June 2022.
Extra lately, the AsyncRAT malware household and RALord ransomware have adopted Rust, demonstrating the language’s rising enchantment amongst cybercriminals.
Rust’s reminiscence security, kind security, and concurrency options make it enticing for professional growth, however these similar traits create substantial challenges for malware analysts.
In contrast to conventional programming languages, Rust binaries are usually statically linked, incorporating intensive library code that may bloat executables to over 3MB whereas containing practically 10,000 capabilities, in comparison with C++ applications with fewer than 100 capabilities and sizes below 20KB.
Enhanced Capabilities for Rust Binary Evaluation
RIFT addresses these challenges by way of a classy three-component structure designed for IDA Professional integration.
Overview of Rust developer toolset
The RIFT Static Analyzer serves as an IDA Professional plugin that extracts crucial metadata, together with the Rust compiler commit hash, embedded dependencies, goal structure, and working system info from binary recordsdata.
RIFT static Analyzer
The RIFT Generator part automates probably the most complicated processes, together with FLIRT signature era and binary diffing.
It capabilities as a wrapper round important instruments, together with Cargo (Rust bundle supervisor), Hexray’s FLAIR instruments (sigmake.exe and pcf.exe), IDA’s command-line interface (idat.exe), and the open-source Diaphora software.
This automation permits the extraction and processing of COFF recordsdata and RLIB recordsdata (Rust-specific archive format much like TAR).
Phases of RIFT Generator
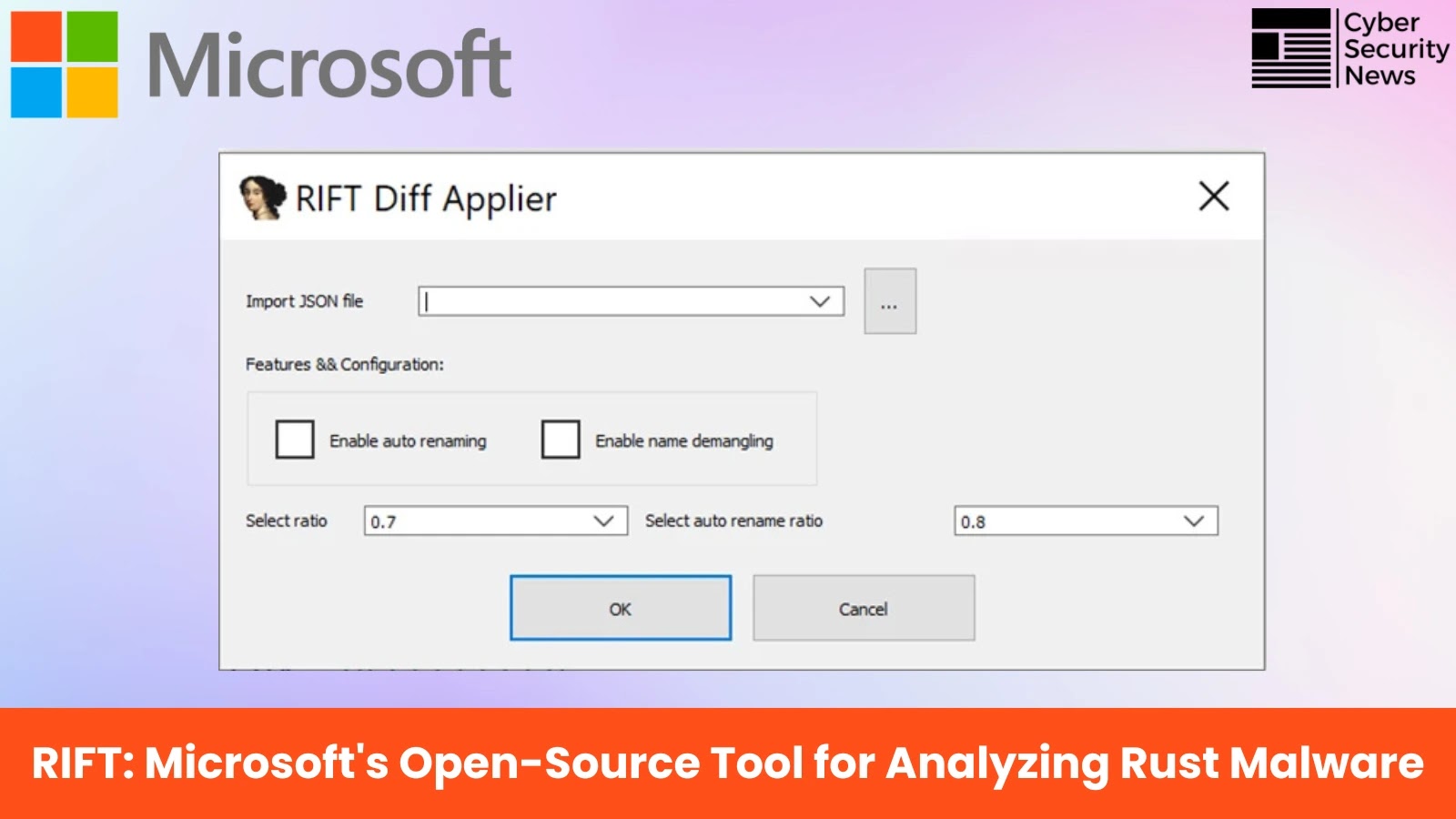
The RIFT Diff Applier supplies analysts with an interactive interface for making use of binary diffing outcomes, working in each interactive and auto-rename modes with configurable similarity thresholds, reads the advisory.
Subject testing of RIFT on real-world threats like RALord ransomware and SPICA backdoor has demonstrated important effectivity enhancements.
The software efficiently distinguishes between attacker-written code and normal library capabilities, permitting analysts to deal with malicious logic fairly than spending time figuring out benign library code.
RIFT’s FLIRT signatures method supplies extremely dependable annotation with low false-positive charges, whereas the binary diffing methodology gives broader protection for circumstances the place strict signature matching fails.
This twin method ensures complete evaluation capabilities throughout totally different malware variants and compilation situations.
By open-sourcing RIFT, Microsoft goals to strengthen international cybersecurity defenses towards the rising menace of Rust-based malware, offering the safety group with important instruments to fight more and more refined cyber threats.
Examine stay malware habits, hint each step of an assault, and make quicker, smarter safety choices -> Strive ANY.RUN now