A brand new and significant safety risk, PerfektBlue, has emerged, concentrating on OpenSynergy’s BlueSDK Bluetooth framework and posing an unprecedented danger to the automotive trade.
This subtle assault vector allows distant code execution (RCE) on hundreds of thousands of units throughout automotive and different industries by way of a sequence of reminiscence corruption and logical vulnerabilities.
Key Takeaways1. 4 chained vulnerabilities in BlueSDK allow one-click distant code execution by way of Bluetooth.2. Hundreds of thousands of Mercedes-Benz, Volkswagen, and Škoda autos affected by way of compromised infotainment techniques.3. Attackers achieve GPS monitoring, audio recording, private information entry, and potential car ECU management.4. Regardless of September 2024 fixes, automotive provide chain delays left some producers unpatched till June 2025.
The exploit chain requires minimal person interplay and poses extreme dangers to in-vehicle infotainment (IVI) techniques, doubtlessly permitting attackers to entry GPS coordinates, audio recordings, private information, and carry out lateral motion to crucial car digital management items (ECUs).
Vital Flaws in OpenSynergy’s BlueSDK Bluetooth Framework
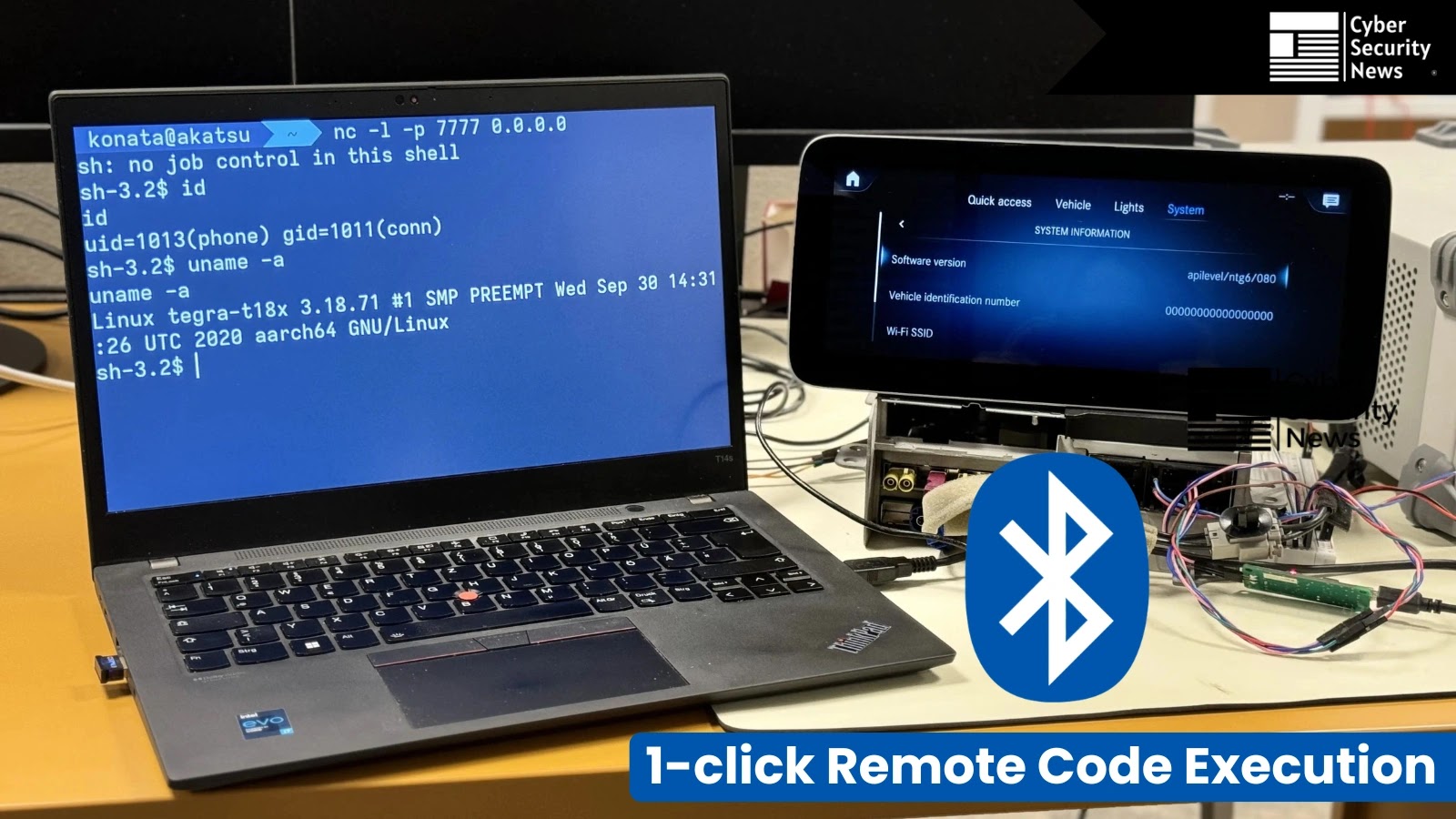
PCA Cyber Safety has reported to Cyber Safety Information that the assault makes use of a complicated exploitation chain, which mixes 4 distinct vulnerabilities that may be executed with minimal person interplay, necessitating at most a single click on from the focused person.
The assault methodology exploits the framework nature of BlueSDK, the place totally different distributors implement various safety configurations and pairing mechanisms.
The exploitation course of begins with establishing a Bluetooth connection to the goal system, sometimes requiring pairing to attain applicable safety communication ranges.
Nevertheless, the particular pairing necessities range considerably between implementations as a result of BlueSDK’s framework structure.
Some units might have limitless pairing requests, others require person interplay, and sure configurations may disable pairing completely. This variability creates a fancy assault floor the place exploitation necessities differ throughout producers and system sorts.
The assault’s efficiency lies in its potential to attain distant code execution by way of Bluetooth communication protocols, particularly concentrating on AVRCP (Audio/Video Distant Management Profile), L2CAP (Logical Hyperlink Management and Adaptation Protocol), and RFCOMM (Radio Frequency Communication) layers.
As soon as profitable, attackers achieve user-level privileges throughout the goal system, enabling additional exploitation and lateral motion.
The PerfektBlue assault chain consists of 4 crucial vulnerabilities, every assigned particular CVE identifiers.
CVE-2024-45434 represents probably the most extreme vulnerability, a Use-After-Free (UAF) situation within the AVRCP service, with a CVSS rating of 8.0.
This reminiscence corruption vulnerability happens when the system fails to validate object existence earlier than performing operations, permitting attackers to govern freed reminiscence areas and execute arbitrary code.
CVE-2024-45431 includes improper validation of L2CAP channel distant Channel Identifiers (CID), scoring 3.5 on the CVSS scale.
This vulnerability permits attackers to create L2CAP channels with null identifiers as distant CIDs, doubtlessly bypassing safety mechanisms.
CVE-2024-45433 and CVE-2024-45432 each goal the RFCOMM protocol implementation, scoring 5.7 every.
The previous includes incorrect operate termination, missing correct return management circulation after detecting uncommon circumstances, whereas the latter stems from operate calls with incorrect parameters utilizing the unsuitable variables as arguments.
The technical exploitation requires a deep understanding of Bluetooth protocol stacks, reminiscence administration, and embedded system architectures.
Attackers should chain these vulnerabilities sequentially, exploiting the UAF situation in AVRCP after establishing compromised L2CAP and RFCOMM connections by way of the opposite vulnerabilities.
CVE IDDescriptionCVSS 3.1 ScoreSeverityCVE-2024-45434Use-After-Free in AVRCP service8.0CriticalCVE-2024-45431Improper validation of an L2CAP channel’s distant CID3.5LowCVE-2024-45433Incorrect operate termination in RFCOMM5.7MediumCVE-2024-45432Function name with incorrect parameter in RFCOMM5.7Medium
Mitigations
The scope of PerfektBlue’s affect extends throughout main automotive producers, with confirmed vulnerabilities in Mercedes-Benz, Volkswagen, and Škoda autos.
Proof-of-concept exploits have been efficiently demonstrated on Mercedes-Benz NTG6/NTG7 head items, Volkswagen MEB ICAS3 infotainment techniques (ID.4 mannequin line), and Škoda MIB3 head items (Very good mannequin line).
Every exploitation grants attackers user-level privileges corresponding to cellphone or sint_sec_btapp permissions inside IVI techniques.
The automotive trade’s advanced provide chain has sophisticated patch deployment, with some producers not receiving patches till June 2025, regardless of OpenSynergy releasing fixes in September 2024.
This delay highlights crucial vulnerabilities within the automotive cybersecurity provide chain administration.
Mitigation methods embrace quick firmware updates for affected units, disabling Bluetooth performance when not required, and implementing community segmentation to forestall lateral motion from IVI techniques to crucial car parts.
Producers ought to prioritize safety validation in Bluetooth stack implementations and set up strong vulnerability disclosure processes.
Examine stay malware conduct, hint each step of an assault, and make quicker, smarter safety selections -> Attempt ANY.RUN now