Might 09, 2025Ravie LakshmananMalware / Electronic mail Safety
Cybersecurity researchers are warning of a brand new marketing campaign that is focusing on Portuguese-speaking customers in Brazil with trial variations of economic distant monitoring and administration (RMM) software program since January 2025.
“The spam message makes use of the Brazilian digital bill system, NF-e, as a lure to entice customers into clicking hyperlinks and accessing malicious content material hosted in Dropbox,” Cisco Talos researcher Guilherme Venere stated in a Thursday report.
The assault chains start with specifically crafted spam emails that declare to originate from monetary establishments or cellular phone carriers, warning of overdue payments or excellent funds as a way to trick customers into clicking on bogus Dropbox hyperlinks that time to a binary installer for the RMM software.
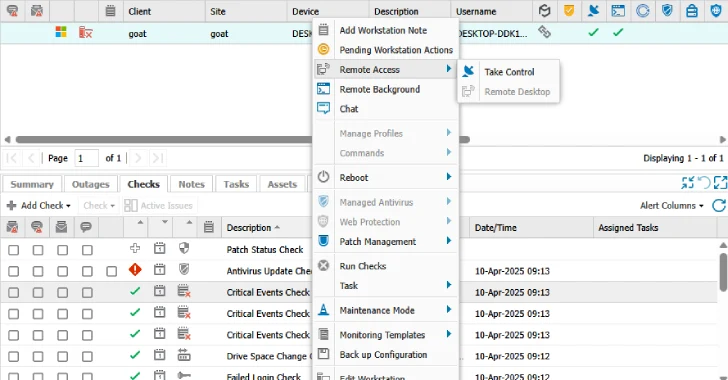
Two notable RMM instruments noticed are N-able RMM Distant Entry and PDQ Join, granting attackers the flexibility to learn and write recordsdata to the distant file system.
In some circumstances, the risk actors then use the distant capabilities of those brokers to obtain and set up a further RMM software program akin to ScreenConnect after the preliminary compromise.
Based mostly on the widespread recipients noticed, the marketing campaign has been discovered to primarily goal C-level executives and monetary and human sources account throughout a number of industries, together with some instructional and authorities establishments.
It has additionally been assessed with excessive confidence that the exercise is the work of an preliminary entry dealer (IAB) that is abusing the free trial intervals related to numerous RMM applications to realize unauthorized entry. N-able has since taken steps to disable the affected trial accounts.
“Adversaries’ abuse of economic RMM instruments has steadily elevated lately,” Venere stated. “These instruments are of curiosity to risk actors as a result of they’re normally digitally signed by acknowledged entities and are a totally featured backdoor.”
“Additionally they have little to no price in software program or infrastructure, as all of that is usually offered by the trial model software.”
The event comes amid the emergence of varied phishing campaigns which might be engineered to sidestep fashionable defenses and propagate a variety of malware households, or acquire victims’ credentials –
A marketing campaign carried out by a South American cybercrime group known as Hive0148 to distribute the Grandoreiro banking trojan to customers in customers in Mexico and Costa Rica.
A marketing campaign that employs a official file-sharing service named GetShared to bypass safety protections and direct customers to hyperlinks internet hosting malware
A marketing campaign that makes use of gross sales order-themed lures to ship the Formbook malware via a Microsoft Phrase doc that is inclined to a years-old flaw in Equation Editor (CVE-2017-11882)
A marketing campaign that has focused organizations in Spain, Italy, and Portugal utilizing invoice-related themes to deploy a Java-based distant entry trojan named Ratty RAT that may execute distant instructions, log keystrokes, seize screenshots, and steal delicate knowledge
A marketing campaign that makes use of a official note-taking software often called Milanote and an adversary-in-the-middle (AitM) phishing equipment dubbed Tycoon 2FA to seize customers’ credentials underneath the guise of viewing a “new settlement”
Campaigns that make the most of encoded JavaScript inside SVG recordsdata, booby-trapped hyperlinks in PDF attachments, dynamic phishing URLs which might be rendered at runtime inside OneDrive-hosted recordsdata, and archived MHT payloads inside OpenXML buildings to direct customers to credential harvesting or phishing pages
Campaigns that abuse Cloudflare’s TryCloudflare tunneling characteristic to deploy malware like AsyncRAT
“Attackers repeatedly evolve techniques to bypass fashionable e mail and endpoint safety options, making detecting and mitigating phishing makes an attempt more and more tough,” Intezer researcher Yuval Guri famous final month. “And regardless of developments in cybersecurity instruments, many phishing campaigns nonetheless efficiently attain customers’ inboxes.”
Discovered this text attention-grabbing? Comply with us on Twitter and LinkedIn to learn extra unique content material we put up.