A classy malware marketing campaign concentrating on Technology Z players has emerged, leveraging weaponized variations of fashionable video games to infiltrate gaming communities and steal delicate data.
The marketing campaign, which has recorded over 19 million malware distribution makes an attempt in a single yr, demonstrates how cybercriminals are more and more exploiting the digital native technology’s ardour for gaming to execute large-scale knowledge theft operations.
The first assault vector includes distributing malicious recreation installer recordsdata disguised as authentic variations of fashionable titles together with Grand Theft Auto, Minecraft, and Name of Obligation.
A wonderful background and recognizable characters (Supply – Kaspersky)
These three video games alone accounted for 11.2 million assault makes an attempt, representing practically 60% of all recorded incidents.
The malware operators have strategically chosen these titles as a consequence of their large on-line communities and the fixed demand for modifications, cheats, and cracked variations amongst gamers.
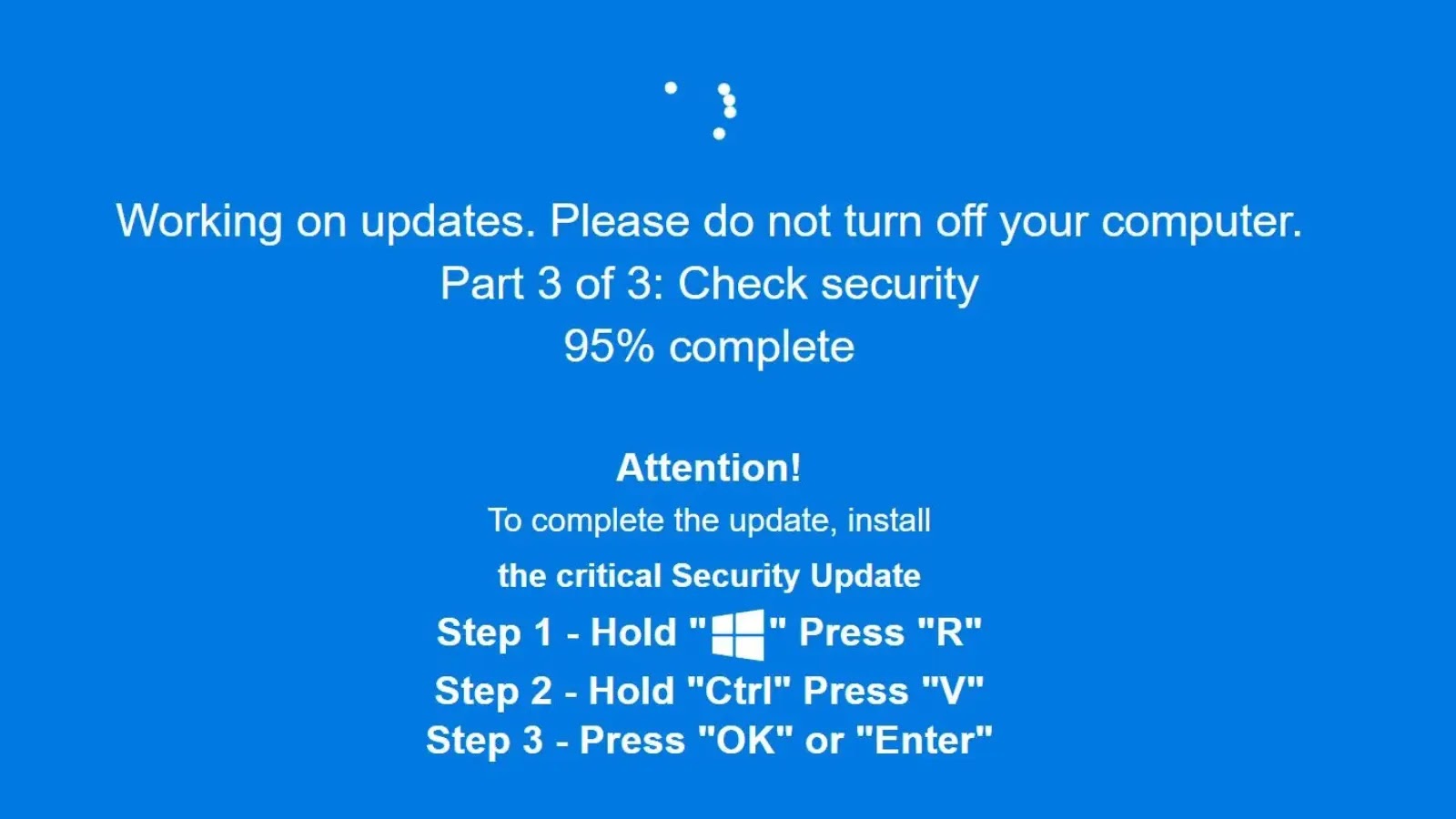
The risk panorama has developed past easy phishing schemes to incorporate refined stealer malware that targets a number of platforms concurrently.
Kaspersky analysts recognized the Hexon stealer as a major risk in November 2024, distributed via gaming boards, Discord channels, and file-sharing websites.
Attackers’ message in a Discord channel (Supply – Kaspersky)
This malware demonstrates superior capabilities, extracting consumer knowledge from Steam gaming platforms whereas concurrently concentrating on messaging purposes together with Telegram, WhatsApp, and social media platforms reminiscent of TikTok, YouTube, Instagram, and Discord.
The cybercriminals behind this marketing campaign function below a malware-as-a-service mannequin, the place technically expert actors present malware instruments to much less skilled criminals for a price.
This enterprise mannequin has accelerated the marketing campaign’s attain and class, enabling fast deployment throughout a number of distribution channels.
Superior Evasion and Persistence Mechanisms
The malware’s most regarding facet lies in its refined detection evasion capabilities.
Following its preliminary discovery, the Hexon stealer underwent a strategic rebrand to “Leet,” incorporating enhanced anti-analysis options that characterize a big evolution in malware design.
The up to date model implements a multi-layered sandbox bypass mechanism that begins with systematic verification of the contaminated gadget’s public IP handle and complete system specification evaluation.
When executed, the malware performs real-time environmental checks to find out whether it is working inside a digital machine or sandbox surroundings.
The detection algorithm analyzes system {hardware} configurations, community parameters, and operating processes to establish telltale indicators of research environments.
Upon detecting virtualization indicators, the malware instantly terminates its execution, successfully stopping safety researchers from analyzing its habits in managed laboratory settings.
This self-preservation mechanism ensures the malware stays operational in real sufferer environments whereas avoiding detection by automated safety methods and handbook evaluation makes an attempt.
Detect malware in a reside surroundings Analyze suspicious recordsdata & URLs in ANY.RUN’s Sandbox -> Strive for Free