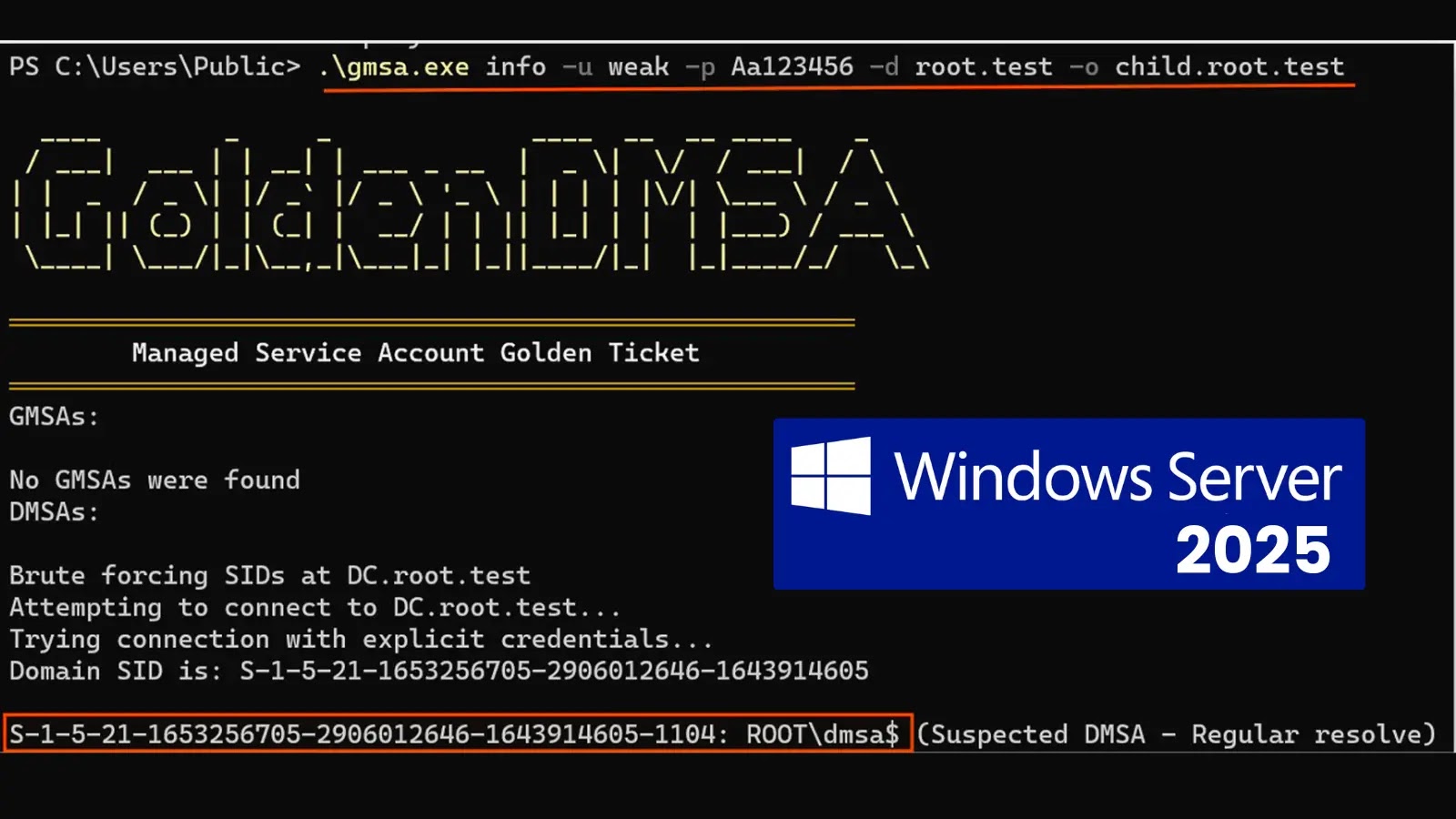
A important design flaw in Microsoft’s newest Home windows Server 2025 allows attackers to bypass authentication and generate passwords for all managed service accounts throughout enterprise networks.
The vulnerability, dubbed “Golden dMSA,” exploits a elementary weak spot within the newly launched delegated Managed Service Accounts (dMSAs) that reduces complicated cryptographic protections to a trivial brute-force assault requiring just one,024 makes an attempt.
Semperis Safety Researcher Adi Malyanker found the vulnerability whereas analyzing the structure of dMSAs, Microsoft’s flagship safety innovation designed to revolutionize service account administration in Home windows Server 2025.
In contrast to conventional service accounts that depend on static passwords susceptible to Kerberoasting assaults, dMSAs have been engineered to bind authentication on to approved machines in Lively Listing, eliminating credential theft by tying authentication to gadget identification quite than user-managed passwords.
The Golden dMSA assault undermines this complete safety mannequin by exploiting a important design flaw within the ManagedPasswordId construction used for password technology.
This construction comprises predictable time-based elements with just one,024 doable combos, making what must be computationally unimaginable into a simple brute-force operation that may be accomplished in minutes.
Home windows Server 2025 Golden dMSA Assault
The assault follows a scientific four-phase method that transforms a single area controller compromise into forest-wide persistent entry.
First, attackers extract cryptographic materials from the Key Distribution Providers (KDS) root key, which serves as the muse for all managed service account passwords.
Subsequent, they enumerate dMSA accounts all through the Lively Listing forest utilizing specialised methods that bypass restrictive Entry Management Lists.
The third section includes figuring out the right ManagedPasswordId attributes by focused guessing, adopted by password technology utilizing specialised instruments.
What makes this vulnerability significantly harmful is its scope and persistence. The assault operates on the forest degree, which means a single profitable KDS root key extraction allows cross-domain lateral motion and compromise of each dMSA account throughout all domains inside that forest.
Since KDS root keys haven’t any expiration date, this entry may theoretically final indefinitely, making a persistent backdoor that survives typical safety rotations and updates.
Semperis charges this vulnerability as reasonable threat as a result of exploitation requires possession of a KDS root key, which is just accessible to essentially the most privileged accounts: Area Admins, Enterprise Admins, and SYSTEM-level entry.
Nevertheless, the researchers emphasize that the affect could be extraordinarily excessive, enabling attackers to bypass trendy protections like Credential Guard and basically problem the assumed safety advantages of machine-bound authentication.
The assault is especially regarding as a result of it utterly circumvents Microsoft’s meant authentication stream.
As a substitute of following regular dMSA authentication procedures that require machine identification validation, the Golden dMSA approach makes use of compromised cryptographic keys to generate legitimate passwords instantly, rendering Credential Guard and comparable protections irrelevant.
Detection of Golden dMSA exercise presents important challenges for enterprise safety groups.
By default, no safety occasions are logged when KDS root keys are compromised, requiring directors to manually configure System Entry Management Lists (SACLs) on KDS root key objects to audit learn entry.
This configuration hole makes the assault significantly stealthy and tough to detect in real-time. The device is offered by way of GitHub.
Organizations can monitor for irregular volumes of authentication requests focusing on service accounts and weird Ticket-Granting Ticket requests for dMSA accounts.
Nevertheless, these indicators require refined log evaluation and should generate false positives in busy enterprise environments.
Microsoft acknowledged the vulnerability report submitted to the Microsoft Safety Response Heart on Could 27, 2025. Of their July 8, 2025, response, the corporate said: “When you’ve got the secrets and techniques used to derive the important thing, you’ll be able to authenticate as that person. These options have by no means been meant to guard towards a compromise of a website controller.”
Examine dwell malware habits, hint each step of an assault, and make sooner, smarter safety selections -> Attempt ANY.RUN now