A vital vulnerability in Microsoft Entra ID permits attackers to escalate privileges to the World Administrator position via the exploitation of first-party functions.
The vulnerability, reported to Microsoft Safety Response Middle (MSRC) in January 2025, impacts organizations utilizing hybrid Energetic Listing environments with federated domains.
Key Takeaways1. Attackers with sure admin or app permissions can hijack the Workplace 365 Alternate On-line service principal.2. Attackers use the Area.ReadWrite.All so as to add a malicious federated area and forge SAML tokens.3. Microsoft categorized this threat as “anticipated habits”.
Microsoft Entra ID Vulnerability
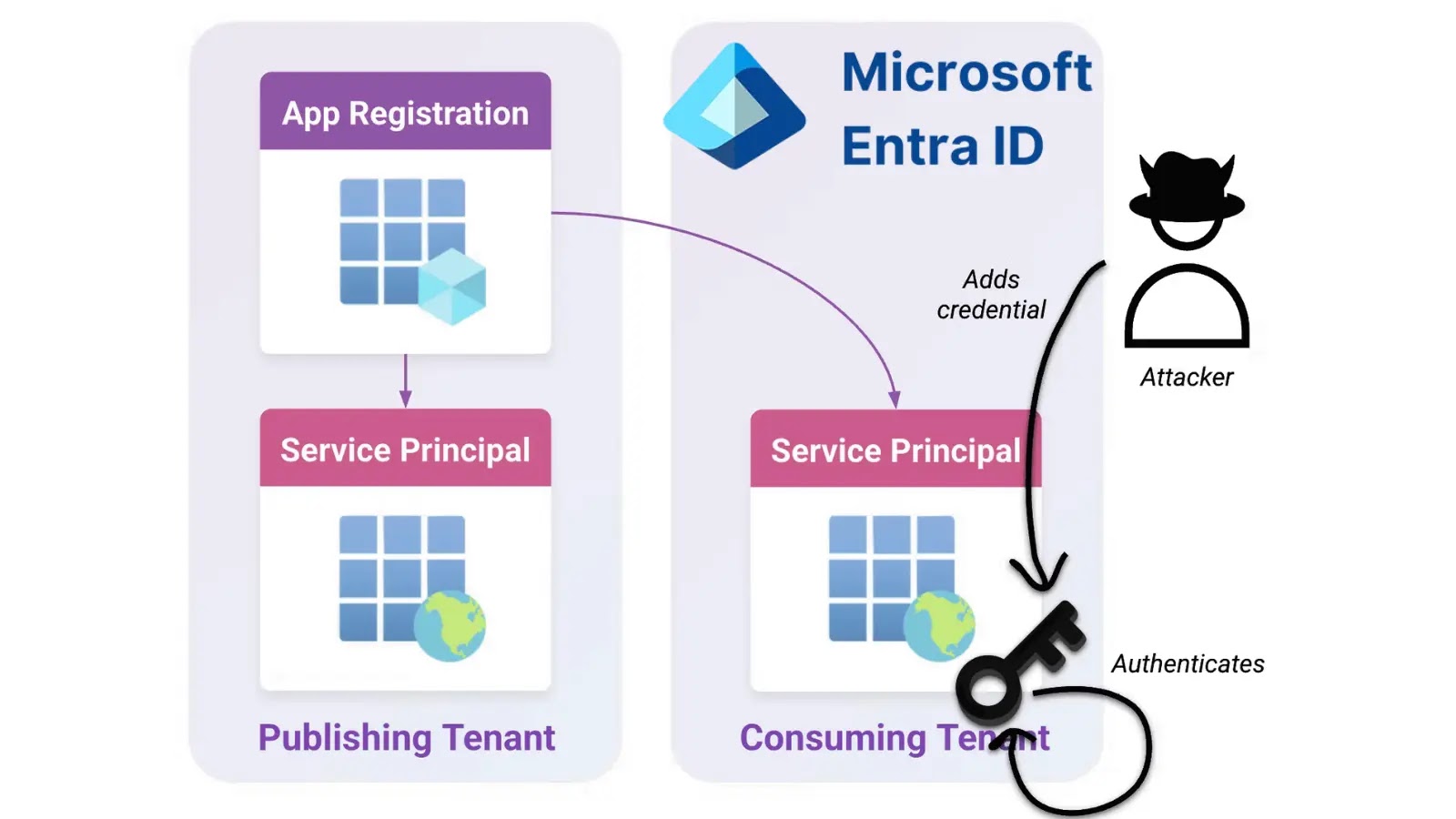
Safety researchers at Datadog found that service principals (SPs) assigned the Cloud Utility Administrator position, Utility Administrator position, or Utility.ReadWrite.All permission can escalate their privileges by hijacking the built-in Workplace 365 Alternate On-line service principal (Shopper ID: 00000002-0000-0ff1-ce00-000000000000).
The vulnerability works by exploiting the Workplace 365 Alternate On-line SP’s Area.ReadWrite.All permission so as to add a brand new federated area to the tenant.
Attackers can then forge SAML tokens as any hybrid tenant person synchronized between on-premises Energetic Listing (AD) and Entra ID, together with customers with World Administrator privileges.
Backdooring SPs
The assault leverages the consumer credentials grant move for authentication:
Federated Area Backdoor Approach
The privilege escalation follows a five-step course of involving federated area manipulation.
Attackers first add a malicious area utilizing the Microsoft Graph API endpoint POST /v1.0/domains, then confirm it via DNS data.
The vital step includes configuring federation settings through POST /v1.0/domains/{area}/federationConfiguration with a malicious certificates:
Malicious area seems as federated in Entra ID
This configuration permits attackers to forge SAML tokens with MFA claims, bypassing multi-factor authentication necessities whereas sustaining the looks of official authentication in sign-in logs.
Signal-in immediate as a World Administrator with solid SAML token
Microsoft’s Response
Datadog reported this vulnerability to the Microsoft Safety Response Middle (MSRC) on January 14, 2025, initiating a months-long disclosure course of.
Nonetheless, on Could 14, 2025, MSRC concluded that this “is just not a safety vulnerability however anticipated habits of the Utility Administrator position and its related permissions”.
Microsoft’s response emphasised that the state of affairs displays misconfiguration fairly than a safety bypass, stating that Utility Administrator roles inherently embody the flexibility to handle utility credentials and impersonate utility identities.
Enhance detection, cut back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Attempt ANY.RUN Now