Microsoft right now introduced the rollout of a revamped buyer dashboard in Microsoft Defender for Workplace 365, designed to ship unprecedented insights throughout a broad spectrum of assault vectors.
The brand new interface offers safety groups real-time visibility into threats blocked earlier than supply, malicious content material remediated post-delivery, and even “missed” incidents, all with out sacrificing privateness or efficiency.
By exposing granular metrics on options akin to Secure Hyperlinks, Secure Attachments, and Zero-hour Auto Purge, the dashboard empowers CISOs and safety architects to make data-driven choices in an surroundings the place transparency is the brand new forex of belief.
Key Takeaways1. Microsoft Defender for Workplace 365 launches enhanced risk visibility dashboard.2. Actual-world efficiency comparisons of e mail safety options launched.3. Ongoing clear reporting for data-driven safety choices.
Superior Menace Visibility
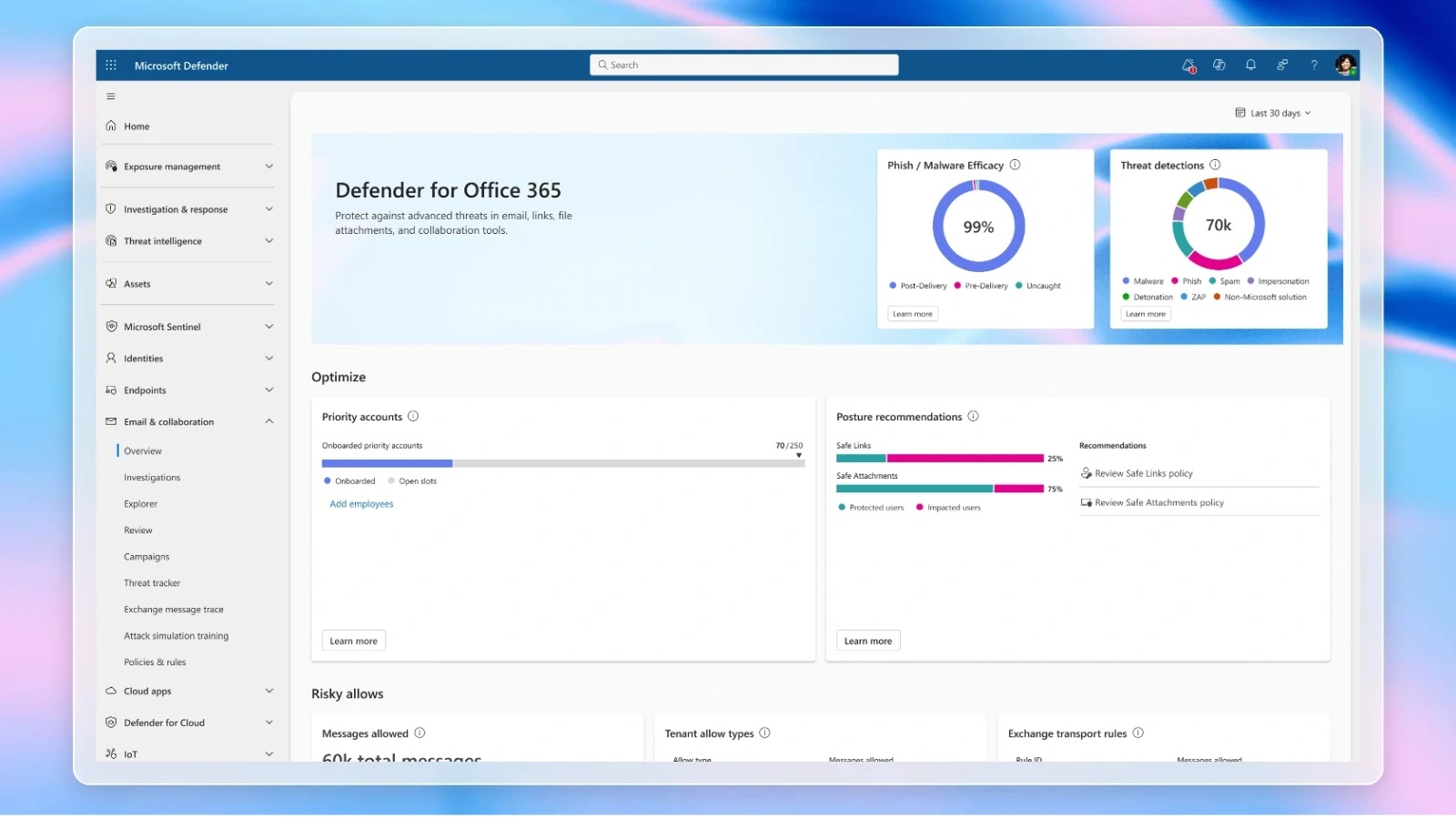
The centerpiece of the announcement is the Overview Dashboard, which unifies a number of risk streams right into a single view.
Safety operations groups can monitor the quantity of phishing URLs neutralized by Secure Hyperlinks, the depend of malicious information quarantined via Secure Attachments, and the variety of messages auto-purged at zero-hour actions taken earlier than customers even see suspicious content material.
Past merely tallying blocked occasions, the dashboard surfaces dwell instances for post-delivery threats, flagging delayed detections in order that groups can tune their insurance policies and workflow integrations.
By charting exercise throughout Trade On-line, Microsoft Groups, SharePoint, and OneDrive, defenders can now correlate spikes in BEC makes an attempt or malware campaigns with broader collaboration developments.
A companion pane breaks down risk classes, Bulk, Spam, and Malicious, and exhibits how every Defender functionality contributes to total safety.
Safety architects can pivot from high-level statistics into detailed drill-downs, viewing the highest sender domains leveraged in current phishing waves or the file varieties mostly weaponized in malware outbreaks.
The consequence is not only a dashboard, however a residing intelligence middle that turns uncooked telemetry into actionable operational insights.
Benchmarking Stories
Recognizing that many organizations function layered e mail defenses, Microsoft additionally printed two benchmarking reviews evaluating Safe Electronic mail Gateways (SEGs) and Built-in Cloud Electronic mail Safety (ICES) distributors in opposition to Defender for Workplace 365.
Not like artificial evaluations, these research use real-world risk knowledge aggregated throughout tens of millions of mailboxes.
In a single state of affairs, SEGs positioned in entrance of Defender have been measured for pre-delivery misses versus Defender’s personal pre- and post-delivery requirements.
In one other, ICES merchandise invoked through the Microsoft Graph API after Defender for Workplace 365 scanned messages have been assessed for his or her incremental catch charges.
As an example how clients can extract dashboard metrics programmatically, Microsoft supplied this PowerShell instance utilizing the Microsoft Graph Safety API:
The JSON response contains fields akin to safeLinks, safeAttachments, and zeroHourAutoPurge, enabling integration with SIEM and SOAR platforms.
The mixed energy of the brand new dashboard and ecosystem benchmarks presents a rigorous, clear foundation for evaluating not solely Microsoft’s native defenses but additionally the worth added by third-party SEGs and ICES options.
Quarterly updates to each the dashboard metrics and benchmarking reviews will preserve clients apprised of rising assault strategies and vendor efficiency developments.
Increase detection, cut back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Attempt ANY.RUN Now