The UK Authorities has imposed sanctions on Russian navy intelligence models and 18 people following the publicity of a classy cyber espionage marketing campaign focusing on Microsoft cloud providers.
The Nationwide Cyber Safety Centre (NCSC) revealed that the Russian Superior Persistent Risk group APT 28 deployed beforehand unknown malware known as AUTHENTIC ANTICS to steal login credentials and keep persistent entry to sufferer e-mail accounts.
Key Takeaways1. UK sanctions Russian GRU models and 18 people for Microsoft cloud cyber assaults.2. AUTHENTIC ANTICS malware steals login credentials by way of faux login home windows.3. UK boosts protection spending to 2.6% GDP to counter Russian threats.
AUTHENTIC ANTICS Targets Microsoft Cloud Surroundings
The AUTHENTIC ANTICS malware represents a big evolution in Russian cyber capabilities, particularly designed to focus on Microsoft cloud environments by way of refined credential harvesting methods.
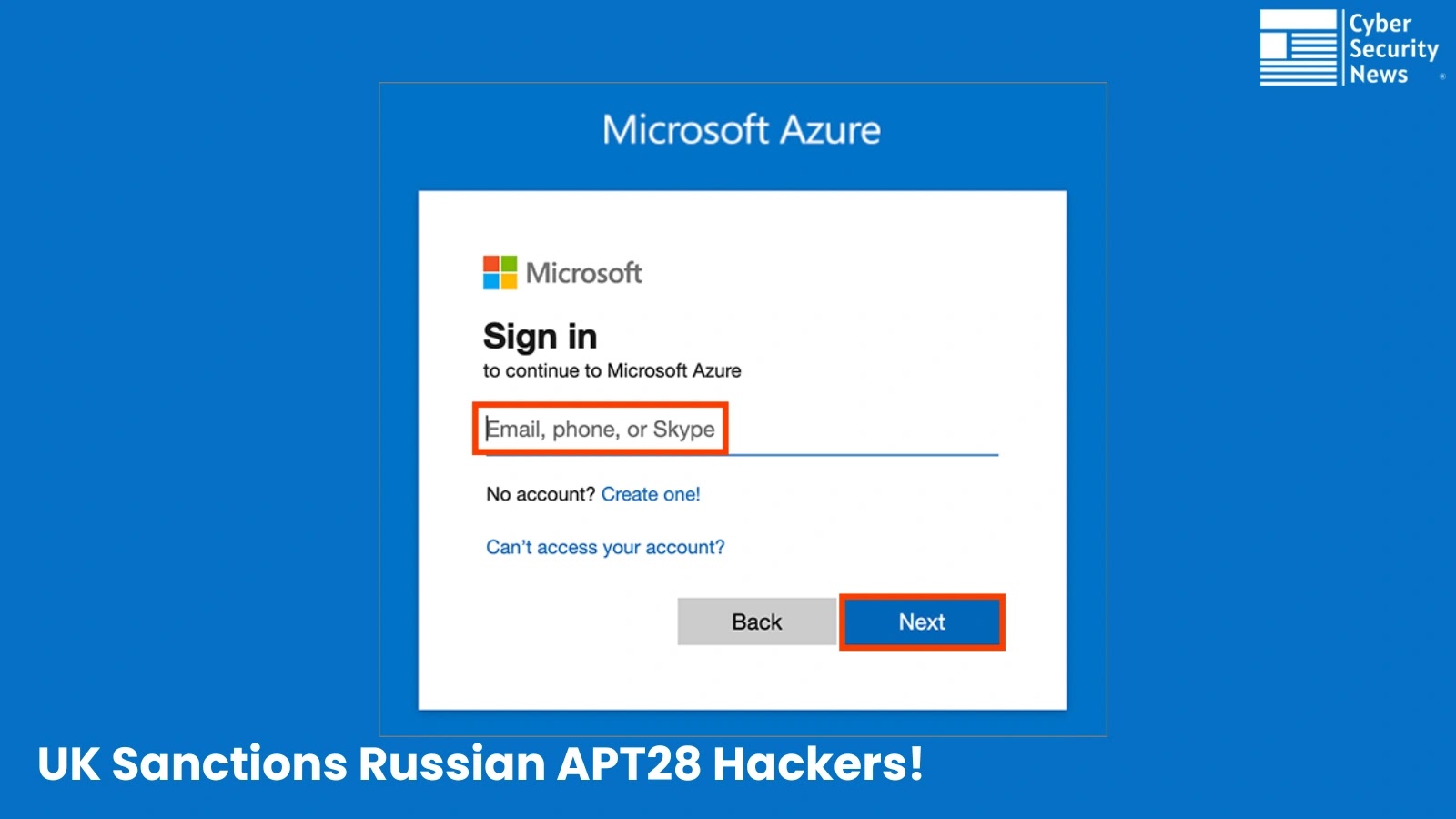
In response to the NCSC’s technical evaluation, the malware operates by periodically displaying legitimate-looking login home windows that immediate customers to enter their credentials.
As soon as captured, these credentials are intercepted alongside OAuth authentication tokens, which give the attackers with prolonged entry to Microsoft providers with out triggering conventional safety alerts.
The malware’s stealth capabilities prolong past easy credential theft. AUTHENTIC ANTICS can exfiltrate delicate knowledge by robotically sending emails from compromised accounts to actor-controlled addresses whereas making certain these messages by no means seem within the sufferer’s despatched folder.
This method permits for covert knowledge extraction that may stay undetected for prolonged intervals, enabling long-term intelligence gathering operations.
The UK’s response consists of complete sanctions towards three GRU models: 26165, 29155, and 74455, together with 18 GRU officers and brokers concerned in world cyber and data interference operations.
Overseas Secretary David Lammy emphasised that these measures reveal the UK’s dedication to countering Russian hybrid threats, stating that “GRU spies are working a marketing campaign to destabilise Europe, undermine Ukraine’s sovereignty and threaten the security of British residents”.
This attribution aligns with the Strategic Defence Assessment’s identification of Russia as essentially the most acute risk going through the UK.
The federal government has introduced the biggest sustained enhance in defence spending for the reason that Chilly Battle, growing to 2.6% of GDP by 2027 as a part of efforts to counter cyber and hybrid threats.
The NCSC’s investigation confirms that APT 28, additionally recognized in open supply communities as Fancy Bear, Forest Blizzard, and Blue Delta, operates as a part of Russia’s GRU eighty fifth Primary Particular Service Centre, Army Unit 26165.
Paul Chichester, NCSC Director of Operations, famous that “the usage of AUTHENTIC ANTICS malware demonstrates the persistence and class of the cyber risk posed by Russia’s GRU”.
The malware discovery emerged from a cyber incident investigated by Microsoft and NCC Group in 2023, highlighting the significance of public-private cybersecurity partnerships.
The UK’s technical attribution has been coordinated with worldwide companions, reinforcing collective protection towards Russian cyber operations focusing on vital infrastructure and democratic establishments throughout Europe and past.
Increase detection, cut back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Strive ANY.RUN Now