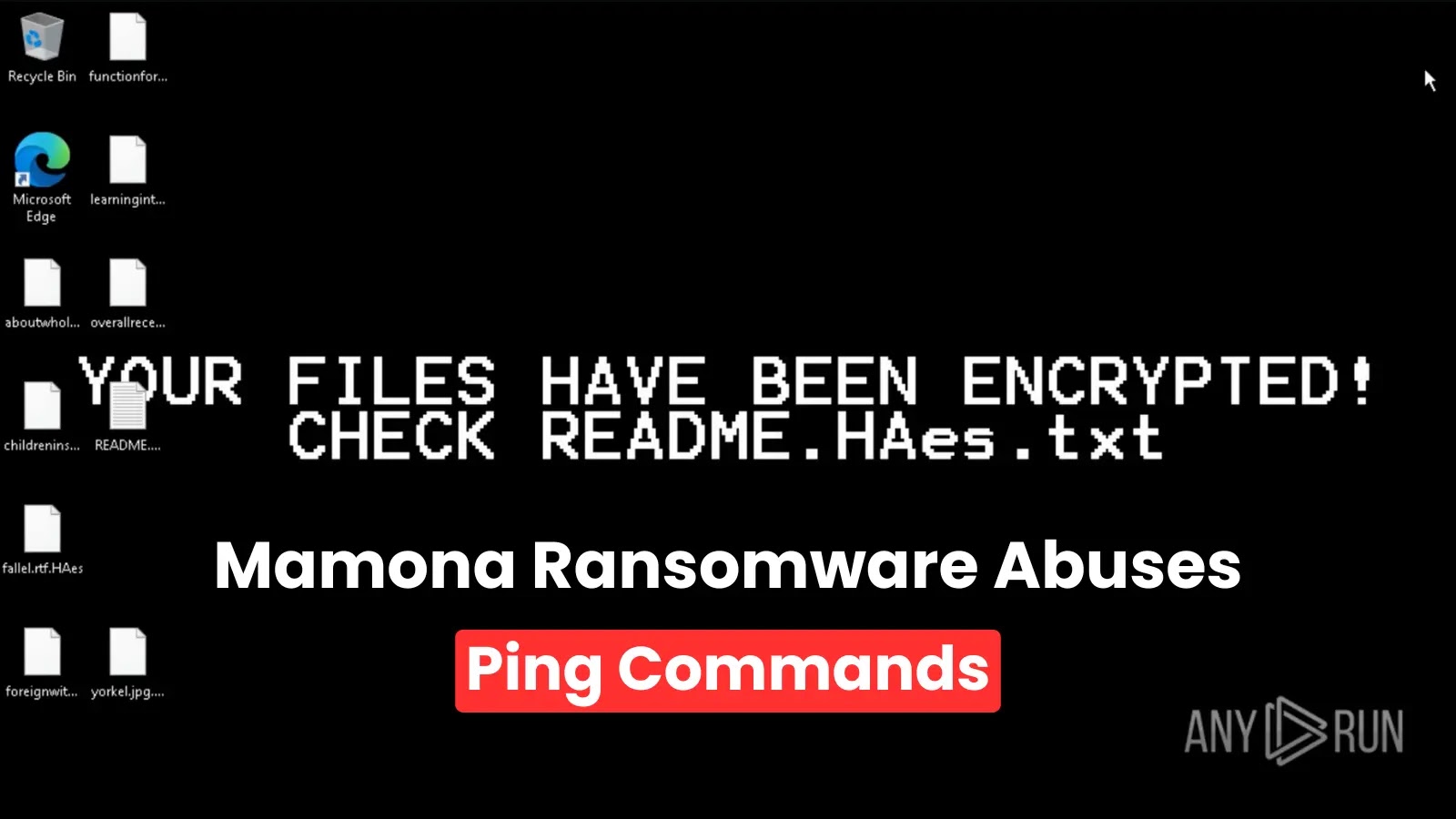
A brand new ransomware pressure dubbed “Mamona” that operates solely offline and leverages a intelligent assault technique that abuses the Home windows ping command.
Not like conventional ransomware that communicates with distant servers, Mamona works fully offline, making it significantly troublesome to detect with typical community monitoring instruments.
“This pressure highlights a rising development: ransomware that trades complexity for accessibility. It’s straightforward to deploy, more durable to detect with conventional instruments, and nonetheless efficient sufficient to encrypt programs and stress victims into paying,” Mauro Eldritch famous.
What makes Mamona distinctive is its “mute” operation – it performs all actions domestically, with no noticed Command and Management channels or knowledge exfiltration.
The ransomware employs a particular delay mechanism by pinging the weird loopback deal with 127.0.0.7 relatively than the usual 127.0.0.1, more likely to evade easy detection guidelines
This pressure highlights a rising development: ransomware that trades complexity for accessibility. It’s straightforward to deploy, more durable to detect with conventional instruments, and nonetheless efficient sufficient to encrypt programs and stress victims into paying.
Mamona Ransomware’s Encryption& Obfuscation
Upon an infection, Mamona executes a sequence of rigorously designed steps. First, it makes use of the ping command as a crude timing mechanism, adopted instantly by a self-deletion command to restrict forensic evaluation.
As soon as the brief delay is full, the second a part of the command makes an attempt to delete the executable from disk utilizing Del /f /q,” defined researcher Mauro Eldritch.
It performs reconnaissance by accumulating fundamental system data equivalent to the pc identify and configured language.
Recordsdata are encrypted utilizing a do-it-yourself cryptographic routine relatively than customary libraries, with all encryption logic applied by means of low-level reminiscence manipulation and arithmetic operations.
Attempt ANY.RUN’s Interactive Sandbox For Interactive Malware Evaluation
Encrypted information obtain the “.HAes” extension (e.g., “doc.pdf” turns into “doc.pdf.HAes”), and a ransom word titled “README.HAes.txt” is dropped in a number of directories.
Recordsdata are encrypted utilizing a customized, do-it-yourself encryption routine relatively than customary cryptographic libraries, and are renamed with the .HAes extension.
The ransomware adjustments the desktop wallpaper to show “Your information have been encrypted!”.
Regardless of threatening to leak stolen knowledge in its ransom word, evaluation confirms Mamona performs no precise knowledge exfiltration. “There’s actually no community exercise, so this appears to be a risk to coerce the sufferer into paying the ransom,” safety consultants concluded.
Mamona has been linked to campaigns beforehand run by BlackLock ransomware associates, who’re additionally related to a different pressure known as Embargo. The ransomware gained further notoriety when the DragonForce group reportedly took over operations after BlackLock was dismantled in March 2025.
Whereas Mamona makes use of comparatively weak encryption strategies, its offline operation and ease-of-use for low-skill cybercriminals pose vital dangers to each people and organizations.
The ransomware significantly threatens small and medium-sized companies with out subtle safety monitoring.
Luckily, safety researchers have recognized and examined a working decryption device. “Regardless of the decrypter that includes an outdated interface, it successfully restores encrypted information,” researchers confirmed.
The emergence of Mamona reinforces a regarding development within the ransomware panorama – the shift towards simply accessible, builder-based ransomware that prioritizes simplicity over sophistication, decreasing the barrier to entry for much less technical cybercriminals.
Combine ANY.RUN Options in Your Firm – Get a Free Trial