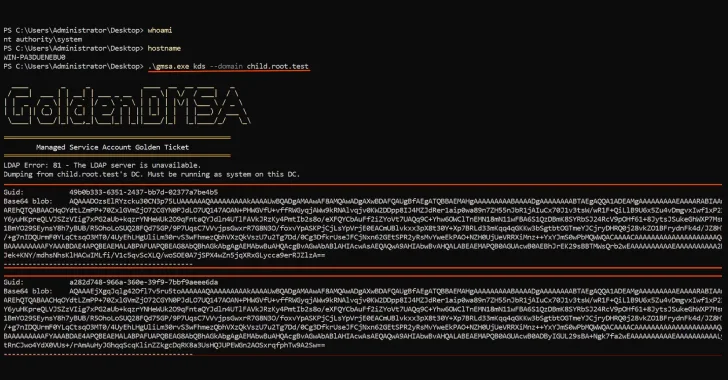
Jul 25, 2025Ravie LakshmananCybercrime / Insider Risk
The U.S. Division of the Treasury’s Workplace of Overseas Belongings Management (OFAC) sanctioned a North Korean entrance firm and three related people for his or her involvement within the fraudulent distant info expertise (IT) employee scheme designed to generate illicit revenues for Pyongyang.
The sanctions goal Korea Sobaeksu Buying and selling Firm (aka Sobaeksu United Company), and Kim Se Un, Jo Kyong Hun, and Myong Chol Min for evading sanctions imposed by the U.S. and the United Nations in opposition to the Democratic Folks’s Republic of Korea (DPRK) authorities.
“Our dedication is obvious: Treasury, as a part of a whole-of-government effort, will proceed to carry accountable those that search to infiltrate world provide chains and allow the sanctions evasion actions that additional the Kim regime’s destabilizing agenda,” mentioned Director of OFAC Bradley T. Smith.
The newest motion marks the U.S. authorities’s continued efforts to dismantle North Korea’s wide-ranging income era schemes and fund its unlawful nuclear and ballistic missile applications.
The IT employee scheme, which has mutated into a worldwide menace, entails the DPRK regime dispatching extremely expert IT staff to numerous places, together with China, Russia, and Vietnam, to acquire distant jobs and infiltrate U.S. firms and elsewhere utilizing a mixture of fraudulent paperwork, stolen identities, and false personas, usually with assist from facilitators who run laptop computer farms.
In what has been described as a recurring, if “baffling,” theme, many of those faux staff have been discovered to make use of Minions and different Despicable Me characters in social-media profiles and electronic mail addresses.
“The DPRK authorities withholds a lot of the wages earned by IT staff, producing tons of of hundreds of thousands of {dollars} in income to help the North Korean regime’s illegal weapons of mass destruction and ballistic missile applications,” the Treasury mentioned. “In some instances, these DPRK IT staff have launched malware into firm networks to exfiltrate proprietary and delicate information.”
The event comes merely weeks after OFAC sanctioned Tune Kum Hyok, a 38-year-old member of a North Korean hacking group referred to as Andariel, for his or her function within the IT employee scheme.
In associated information, Christina Marie Chapman, 50, of Arizona, was sentenced to eight.5 years in jail for operating a laptop computer farm for IT staff to offer the impression that they have been working remotely throughout the U.S. when, in actuality, they have been logging into these machines remotely. Chapman pleaded responsible earlier this February.
The impacted firms included a top-five main tv community, a Silicon Valley expertise firm, an aerospace producer, an American automobile maker, a luxurious retail retailer, and a U.S. media and leisure firm. The IT staff additionally unsuccessfully tried to land jobs at two completely different U.S. authorities businesses.
The U.S. Federal Bureau of Investigation (FBI) seized greater than 90 laptops from Chapman’s dwelling throughout an October 2023 raid. Chapman can be mentioned to have 49 laptops at places abroad, together with a number of shipments to a Chinese language metropolis on the North Korean border.
In all, the flowery counterfeit operation netted greater than $17 million in illicit income for Chapman and North Korea from October 2020 to October 2023. Chapman has additionally been ordered to serve three years of supervised launch, to forfeit $284,556 that was to be paid to the North Koreans, and to pay a judgment of $176,850.
“Christina Chapman perpetrated a years’ lengthy scheme that resulted in hundreds of thousands of {dollars} raised for the DPRK regime, exploited greater than 300 American firms and authorities businesses, and stole dozens of identities of Americans,” mentioned Appearing Assistant Lawyer Basic Matthew R. Galeotti of the Justice Division’s Legal Division.