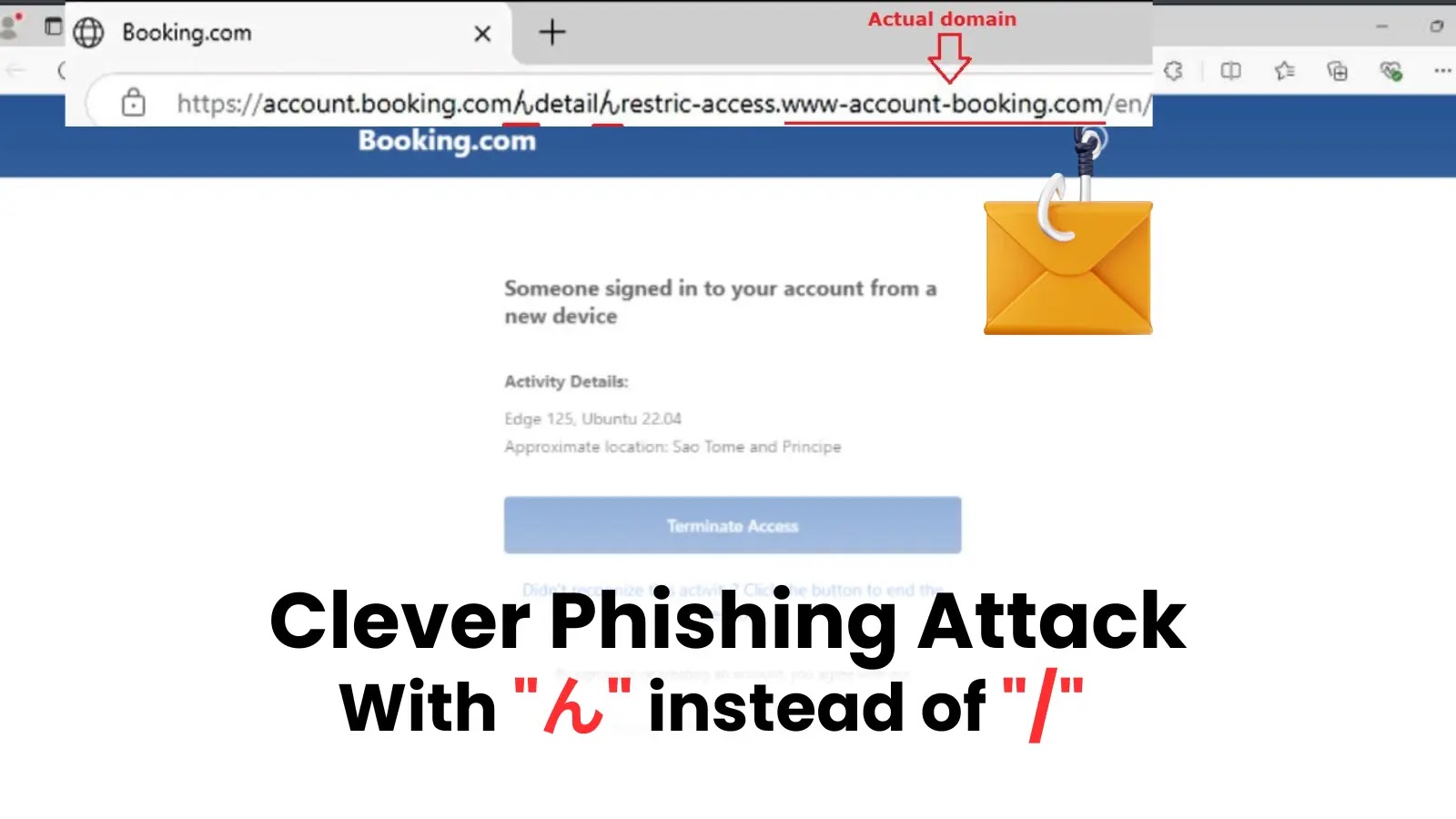
A complicated new info stealer named SHUYAL has emerged within the cybersecurity panorama, demonstrating unprecedented scope in its credential harvesting capabilities.
The malware targets login credentials from 19 totally different internet browsers, starting from mainstream functions like Google Chrome and Microsoft Edge to privacy-focused browsers reminiscent of Tor and Epic.
This complete strategy makes SHUYAL significantly harmful, as it might compromise consumer credentials no matter their browser preferences.
The stealer operates by way of a multi-stage assault vector that begins with system reconnaissance and progresses to credential extraction and information exfiltration.
SHUYAL employs superior evasion strategies, together with automated disabling of Home windows Activity Supervisor and complex anti-detection mechanisms that assist it stay undetected throughout its malicious operations.
The malware’s self-deletion capabilities additional improve its stealth profile, eradicating traces of its exercise after finishing its main capabilities.
Hybrid Evaluation researchers recognized SHUYAL by way of complete behavioral evaluation, naming it primarily based on distinctive identifiers found within the executable’s Program Database (PDB) path.
PDB path extracted within the Hybrid Evaluation report (Supply – Hybrid Evaluation)
The malware demonstrates outstanding technical sophistication, combining conventional credential theft with trendy exfiltration strategies that make the most of Discord token harvesting and Telegram-based information transmission infrastructure.
A number of browsers are focused by the stealer (Supply – Hybrid Evaluation)
The affect of SHUYAL extends past easy password theft, because the malware captures system screenshots, clipboard content material, and performs detailed system reconnaissance.
This complete information assortment strategy offers attackers with an entire profile of sufferer methods and consumer actions, considerably amplifying the potential for additional exploitation and id theft.
Superior Evasion and Persistence Mechanisms
SHUYAL’s persistence technique facilities on subtle protection evasion strategies that guarantee long-term system compromise whereas avoiding detection.
The malware establishes persistence by copying itself to the Home windows Startup folder utilizing the CopyFileA perform, guaranteeing automated execution upon system restart.
This persistence mechanism is coupled with aggressive anti-analysis options that actively intervene with safety instruments and system monitoring.
The stealer’s most notable evasion tactic includes systematically focusing on Home windows Activity Supervisor. Upon execution, SHUYAL enumerates working processes to find taskmgr.exe and terminates it utilizing the TerminateProcess methodology.
Following termination, the malware modifies the registry worth DisableTaskMgr to 1, successfully stopping customers from launching Activity Supervisor to analyze suspicious system exercise.
SHUYAL performs intensive system reconnaissance by way of Home windows Administration Instrumentation (WMI) instructions, gathering detailed details about disk drives, enter gadgets, and show configurations.
The malware executes instructions reminiscent of wmic diskdrive get mannequin,serialnumber and wmic path Win32_Keyboard get Description,DeviceID to profile the contaminated system comprehensively.
The credential extraction course of makes use of a complicated SQL question: SELECT origin_url, username_value, password_value FROM logins executed in opposition to browser databases.
The malware decrypts saved passwords by extracting the Grasp key from browser Native State recordsdata, base64-decoding the important thing, and using Home windows Information Safety API (DPAPI) by way of CryptUnprotectData for decryption operations.
Expertise quicker, extra correct phishing detection and enhanced safety for your small business with real-time sandbox analysis-> Strive ANY.RUN now