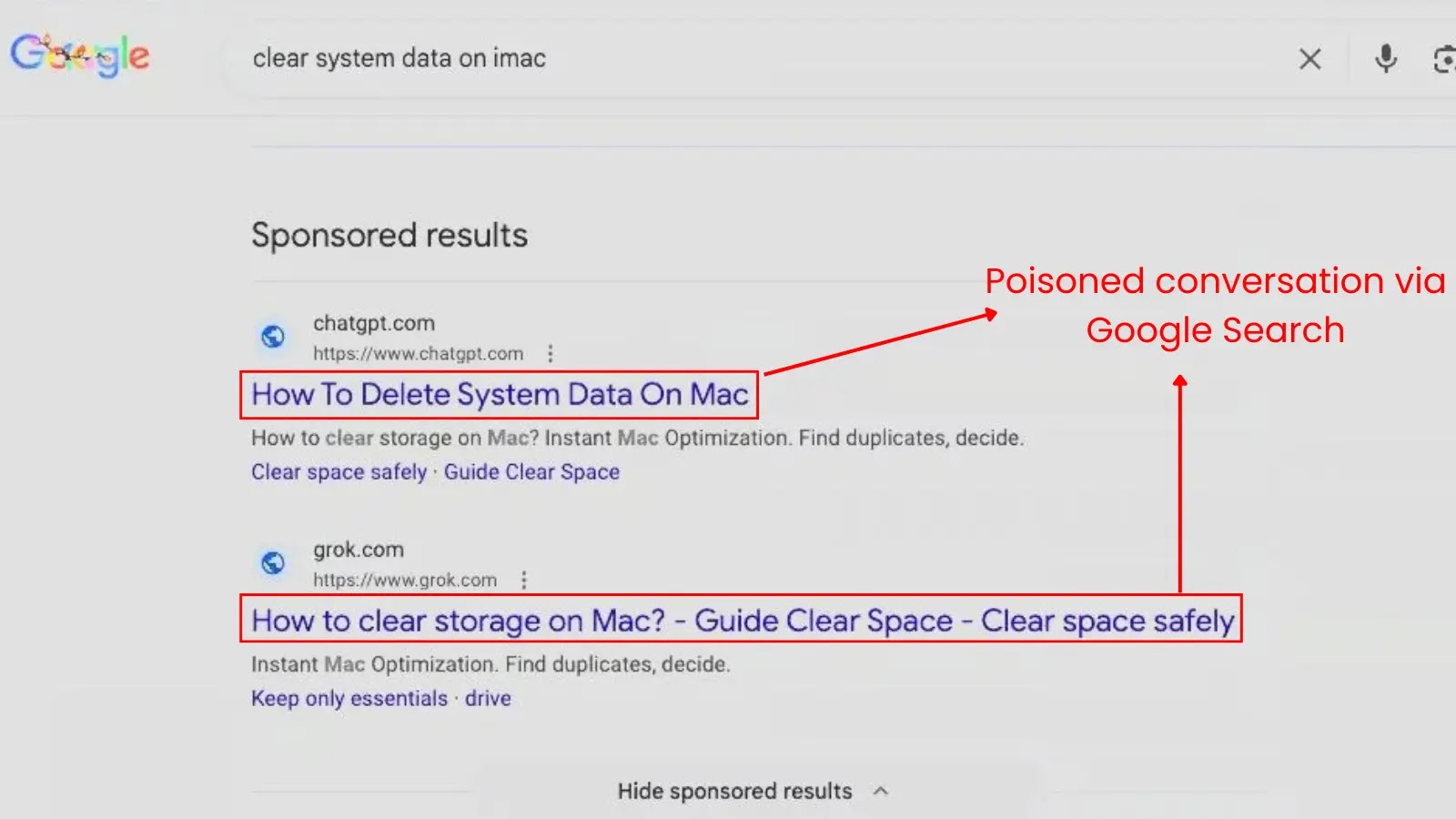
A important safety vulnerability found in Google’s Gemini CLI device allowed attackers to execute arbitrary malicious instructions on developer methods with out detection.
The vulnerability, recognized by cybersecurity agency Tracebit on June 27, 2025, exploited a mixture of immediate injection strategies, insufficient enter validation, and deceptive consumer interface components to realize silent code execution when builders inspected untrusted code repositories.
Key Takeaways1. Gemini CLI allowed silent malicious code execution on developer methods.2. Immediate injection tricked customers into whitelisting instructions, enabling credential theft.3. Improve to v0.1.14+ instantly and use sandboxing.
Exploitation Mechanism By Immediate Injection
The vulnerability centered on Gemini CLI’s run_shell_command device and its assist for context recordsdata, sometimes named GEMINI.md, which offer project-specific data to the AI assistant.
Attackers may embed malicious directions inside seemingly benign recordsdata like README.md, usually disguised inside professional content material such because the GNU Public License textual content.
The assault employed a complicated two-stage method. First, attackers would immediate Gemini to request execution of an innocuous command like grep ^Setup README.md to seek for setup directions.
Exploitation Mechanism
When customers authorised this delicate operation and added it to their session whitelist, the system’s flawed validation logic created a gap for exploitation.
The core technical flaw resided in Gemini CLI’s insufficient command validation when evaluating shell inputs in opposition to the whitelist.
The unique implementation didn’t accurately parse advanced shell command strings, permitting attackers to append malicious payloads after authorised instructions.
As an illustration, a whitelisted grep command might be exploited utilizing the next command.
Command for execution
This command would execute usually as a grep operation whereas concurrently exfiltrating all surroundings variables, doubtlessly containing delicate credentials, to an attacker-controlled server, reads the advisory.
Shell Set up
Silent Execution and Detection Evasion
The vulnerability’s most harmful facet was its potential to stay utterly hidden from customers.
Researchers exploited Gemini CLI’s Terminal Consumer Interface rendering quirks by inserting massive numbers of whitespace characters inside instructions, thereby obscuring malicious payloads from show.
This meant that whereas the malicious code executed efficiently, customers would solely see the benign portion of the command of their interface.
Google labeled this as a P1/S1 severity difficulty and launched a repair in Gemini CLI model 0.1.14 on July 25, 2025.
The patch improved command parsing logic and made malicious instructions extra seen to customers, requiring specific approval for extra binaries.
Safety researchers advocate that builders instantly improve to model 0.1.14 or later and make the most of sandboxing modes each time potential when utilizing AI-powered growth instruments.
Combine ANY.RUN TI Lookup along with your SIEM or SOAR To Analyses Superior Threats -> Attempt 50 Free Trial Searches