A classy cyberattack concentrating on a US-based chemical compounds firm has revealed the primary noticed pairing of SAP NetWeaver exploitation with Auto-Shade malware, demonstrating how risk actors are leveraging important vulnerabilities to deploy superior persistent threats on Linux techniques.
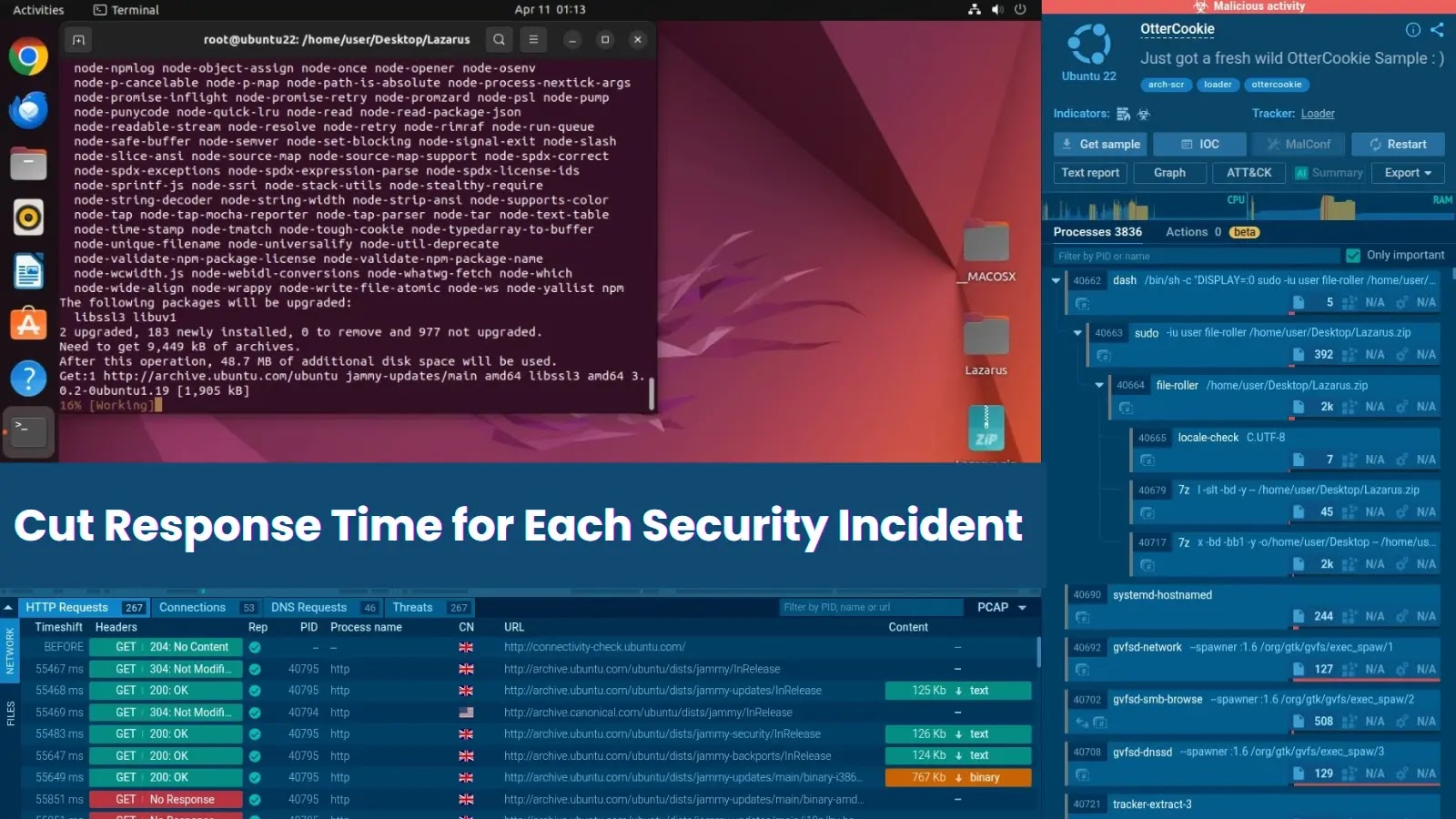
In April 2025, cybersecurity agency Darktrace efficiently detected and contained an assault that exploited CVE-2025-31324, a important vulnerability in SAP NetWeaver, to deploy the stealthy Auto-Shade backdoor malware over three days.
Key Takeaways1. CVE-2025-31324 SAP NetWeaver assault deployed Auto-Shade malware.2. Auto-Shade makes use of Linux manipulation and adaptive evasion strategies.3. Darktrace prevented malware activation and C2 communication.
SAP NetWeaver Vulnerability Exploited
The assault started with the exploitation of CVE-2025-31324, a important vulnerability disclosed by SAP SE on April 24, 2025, that impacts SAP NetWeaver utility servers.
This vulnerability allows malicious actors to add recordsdata to the server, probably resulting in distant code execution and full system compromise.
Menace actors performed reconnaissance actions beginning April 25, scanning for the vulnerability utilizing URIs containing /developmentserver/metadatauploader earlier than launching the complete assault two days later.
The preliminary compromise occurred by way of a ZIP file obtain from a malicious IP deal with 91.193.19[.]109, accompanied by DNS tunneling requests to Out-of-Band Utility Safety Testing (OAST) domains reminiscent of aaaaaaaaaaaa[.]d06oojugfd4n58p4tj201hmy54tnq4rak[.]oast[.]me.
The attackers then executed a shell script named config.sh by way of the helper.jsp file, establishing connections to C2 infrastructure at 47.97.42[.]177 over port 3232, an endpoint related to Supershell, a command-and-control platform linked to China-affiliated risk teams.
Auto-Shade Malware Persistence Methods
The Auto-Shade backdoor malware, named after its skill to rename itself to /var/log/cross/auto-color after execution, represents a complicated Distant Entry Trojan (RAT) that has primarily focused universities and authorities establishments since November 2024.
The malware demonstrates adaptive habits primarily based on privilege ranges, with restricted performance when executed with out root privileges to keep away from detection in restricted environments.
When executed with root privileges, Auto-Shade performs invasive set up procedures, deploying a malicious shared object libcext.so.2 that masquerades as a reputable C utility library.
The malware achieves persistence by way of ld.so.preload manipulation, modifying or creating /and many others/ld.so.preload to insert references to the malicious library.
This method ensures the malware hundreds earlier than different libraries when executing dynamically linked applications, enabling it to hook and override customary system capabilities throughout purposes.
The profitable intervention by Darktrace’s Managed Detection and Response service, which prolonged Autonomous Response actions for a further 24 hours, supplied essential time for the shopper’s safety workforce to analyze and remediate the risk.
The assault underscores the pressing want for organizations utilizing SAP NetWeaver to instantly apply safety patches, as risk actors proceed to use this important vulnerability throughout a number of techniques.
Combine ANY.RUN TI Lookup together with your SIEM or SOAR To Analyses Superior Threats -> Attempt 50 Free Trial Searches