On this article, we’ll present a quick overview of Pillar Safety’s platform to raised perceive how they’re tackling AI safety challenges.
Pillar Safety is constructing a platform to cowl your entire software program improvement and deployment lifecycle with the objective of offering belief in AI techniques. Utilizing its holistic method, the platform introduces new methods of detecting AI threats, starting at pre-planning levels and going all through runtime. Alongside the way in which, customers acquire visibility into the safety posture of their functions whereas enabling secure AI execution.
Pillar is uniquely suited to the challenges inherent in AI safety. Co-founder and CEO Dor Sarig comes from a cyber-offensive background, having spent a decade main safety operations for governmental and enterprise organizations. In distinction, co-founder and CTO Ziv Karlinger spent over ten years creating defensive strategies, securing in opposition to monetary cybercrime and securing provide chains. Collectively, their pink team-blue workforce method varieties the muse of Pillar Safety and is instrumental in mitigating threats.
The Philosophy Behind the Strategy
Earlier than diving into the platform, it is necessary to know the underlying method taken by Pillar. Fairly than creating a siloed system the place every bit of the platform focuses on a single space, Pillar affords a holistic method. Every part throughout the platform enriches the following, making a closed suggestions loop that allows safety to adapt to every distinctive use case.
The detections discovered within the posture administration part of the platform are enriched by information detected within the discovery part. Likewise, adaptive guardrails which might be utilized throughout runtime are constructed on insights from menace modeling and pink teaming. This dynamic suggestions loop ensures that reside defenses are optimized as new vulnerabilities are found. This method creates a strong, holistic and contextual-based protection in opposition to threats to AI techniques – from construct to runtime.
AI Workbench: Menace Modeling The place AI Begins
The Pillar Safety platform begins at what they name the AI workbench. Earlier than any code is written, this safe playground for menace modeling permits safety groups to experiment with AI use instances and proactively map potential threats. This stage is essential to make sure that organizations align their AI techniques with company insurance policies and regulatory calls for.
Builders and safety groups are guided via a structured menace modeling course of, producing potential assault eventualities particular to the applying use case. Dangers are aligned with the applying’s enterprise context, and the method is aligned with established frameworks comparable to STRIDE, ISO, MITRE ATLAS, OWASP High Ten for LLMs, and Pillar’s personal SAIL framework. The objective is to construct safety and belief into the design from day one.
AI Discovery: Actual-Time Visibility into AI Belongings
AI sprawl is a fancy problem for safety and governance groups. They lack visibility into how and the place AI is getting used inside their improvement and manufacturing environments.
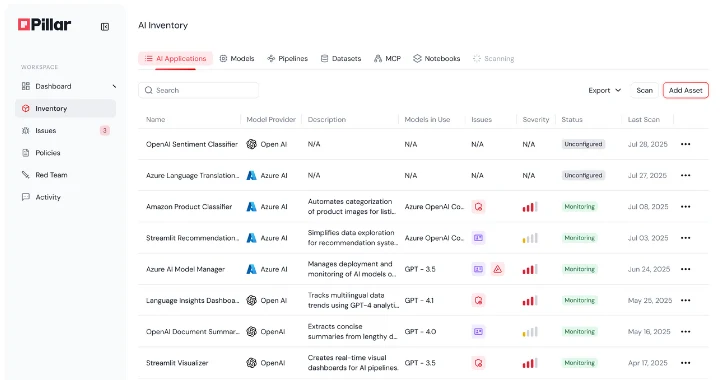
Pillar takes a novel method to AI safety that goes past the CI/CD pipeline and the standard SDLC. By integrating instantly with code repositories, information platforms, AI/ML frameworks, IdPs and native environments, it might probably robotically discover and catalog each AI asset throughout the group. The platform shows a full stock of AI apps, together with fashions, instruments, datasets, MCP servers, coding brokers, meta prompts, and extra. This visibility guides groups, serving to kind the muse of the organizational safety coverage and enabling a transparent understanding of the enterprise use case, together with what the applying does and the way the group makes use of it.
Determine 1: Pillar Safety robotically discovers all AI property throughout the group and flags unmonitored elements to stop safety blind spots.
AI-SPM: Mapping and Managing AI Danger
After figuring out all AI property, Pillar is ready to perceive the safety posture by analyzing every of the property. Throughout this stage, the platform’s AI Safety Posture Administration (AI-SPM) conducts a sturdy static and dynamic evaluation of all AI property and their interconnections.
By analyzing the AI property, Pillar creates visible representations of the recognized Agentic techniques, their elements and their related assault surfaces. Moreover, it identifies provide chain, information poisoning and mannequin/immediate/device degree dangers. These insights, which seem throughout the platform, allow groups to prioritize threats, because it present precisely how a menace actor might transfer via the system.
Determine 2: Pillar’s Coverage Heart gives a centralized dashboard for monitoring enterprise-wide AI compliance posture
AI Purple Teaming: Simulating Assaults Earlier than They Occur
Fairly than ready till the applying is totally constructed, Pillar promotes a trust-by-design method, enabling AI groups to check as they construct.
The platform runs simulated assaults which might be tailor-made to the AI system use case, by leveraging frequent strategies like immediate injections and jailbreaking to classy assaults concentrating on enterprise logic vulnerabilities. These Purple Crew actions assist determine whether or not an AI agent could be manipulated into giving unauthorized refunds, leaking delicate information, or executing unintended device actions. This course of not solely evaluates the mannequin, but additionally the broader agentic software and its integration with exterior instruments and APIs.
Pillar additionally affords a novel functionality via pink teaming for device use. The platform integrates menace modeling with dynamic device activation, rigorously testing how chained device and API calls may be weaponized in reasonable assault eventualities. This superior method reveals vulnerabilities that conventional prompt-based testing strategies are unable to detect.
For enterprises utilizing third-party and embedded AI apps, comparable to copilots, or customized chatbots the place they do not have entry to the underlying code, Pillar affords black-box, target-based pink teaming. With only a URL and credentials, Pillar’s adversarial brokers can stress-test any accessible AI software whether or not inner or exterior. These brokers simulate real-world assaults to probe information boundaries and uncover publicity dangers, enabling organizations to confidently assess and safe third-party AI techniques without having to combine or customise them.
Determine 3: Pillar’s tailor-made pink teaming assessments real-world assault eventualities in opposition to an AI software’s particular use case and enterprise logic
Guardrails: Runtime Coverage Enforcement That Learns
As AI functions transfer into manufacturing, real-time safety controls grow to be important. Pillar addresses this want with a system of adaptive guardrails that monitor inputs and outputs throughout runtime, designed to implement safety insurance policies with out interrupting software efficiency.
In contrast to static rule units or conventional firewalls, these guardrails are mannequin agnostic, application-centric and constantly evolve. In keeping with Pillar, they draw on telemetry information, insights gathered throughout pink teaming, and menace intelligence feeds to adapt in actual time to rising assault strategies. This enables the platform to regulate its enforcement based mostly on every software’s enterprise logic and conduct, and be extremely exact with alerts.
Throughout the walkthrough, we noticed how guardrails could be finely tuned to stop misuse, comparable to information exfiltration or unintended actions, whereas preserving the AI’s meant conduct. Organizations can implement their AI coverage and customized code-of-conduct guidelines throughout functions with confidence that safety and performance will coexist.
Determine 4: Pillar’s adaptive guardrails monitor runtime exercise to detect and flag malicious use and coverage violations
Sandbox: Containing Agentic Danger
One of the crucial crucial issues is extreme company. When brokers can carry out actions past their meant scopes, it might probably result in unintended penalties.
Pillar addresses this throughout the Function section via safe sandboxing. AI brokers, together with superior techniques like coding brokers and MCP servers, run inside tightly managed environments. These remoted runtimes apply zero-trust ideas to separate brokers from crucial infrastructure and delicate information, whereas nonetheless enabling them to function productively. Any surprising or malicious conduct is contained with out impacting the bigger system. Each motion is captured and logged intimately, giving groups a granular forensic path that may be analyzed after the very fact. With this containment technique, organizations can safely give AI brokers the room they should function.
AI Telemetry: Observability from Immediate to Motion
Safety does not cease as soon as the applying is reside. All through the lifecycle, Pillar constantly collects telemetry information throughout your entire AI stack. Prompts, agent actions, device calls, and contextual metadata are all logged in actual time.
This telemetry powers deep investigations and compliance monitoring. Safety groups can hint incidents from symptom to root trigger, perceive anomalous conduct, and guarantee AI techniques are working inside coverage boundaries. It isn’t sufficient to know what occurred. It is about understanding why one thing befell and find out how to stop it from occurring once more.
As a result of sensitivity of the telemetry information, Pillar could be deployed on the client cloud for full information management.
Closing Ideas
Pillar stands aside via a mixture of technical depth, real-world perception, and enterprise-grade flexibility.
Based by leaders in each offensive and defensive cybersecurity, the workforce has a confirmed monitor file of pioneering analysis that has uncovered crucial vulnerabilities and produced detailed real-world assault stories. This experience is embedded into the platform at each degree.
Pillar additionally takes a holistic method to AI safety that extends past the CI/CD pipeline. By integrating safety into the planning and coding phases and connecting on to code repositories, information platforms and native environments, Pillar positive factors early and deep visibility into the techniques being constructed. This context permits extra exact threat evaluation and extremely focused pink workforce testing as improvement progresses.
The platform is powered by the trade’s largest AI menace intelligence feed, enriched by over 10 million real-world interactions. This menace information fuels automated testing, threat modeling, and adaptive defenses that evolve with the menace panorama.
Lastly, Pillar is constructed for versatile deployment. It may well run on premises, in hybrid environments, or totally within the cloud, giving clients full management over delicate information, prompts, and proprietary fashions. It is a crucial benefit for regulated industries the place information residency and safety are paramount.
Collectively, these capabilities make Pillar a strong and sensible basis for safe AI adoption at scale, serving to revolutionary organizations handle AI-specific dangers and acquire belief of their AI techniques.
Discovered this text fascinating? This text is a contributed piece from considered one of our valued companions. Comply with us on Google Information, Twitter and LinkedIn to learn extra unique content material we put up.